Scanning for / Alerting on presence of Client Macs / ESSIDs
There are a number of few great posts out there on this very subject, but hell, no harm in another one
as it is an interesting subject.
Basically I thought it would be cool to have some form of alert system based on mobiles so I could keep track of the coming and goings around the house.
(and when the missus returns so have a few secs to hide the empties.. ;) )
So what methods are there ?
Well if we are talking mobiles then bluetooth & WiFi options are what you could look at.
BLUETOOTH
============
ronin (JP Dunning from www.hackfromacave.com) already made a cool script called blueranger.sh which is included in KALI so anything I can think of will have to wait until I consider it to be of similar quality.. ;)
The jist of it however is as follows ;
Use l2ping to ping a known BADDR and then use hcitool to verify the link quality, for example ;l2ping -i hci0 -c 1 00:11:22:33:44:55 ; hcitool -i hci0 lq 00:11:22:33:44:55
WIFI
=====
A way to start is to monitor the packets with probe request as these are what wifi devices are constantly broadcasting to see if they can connect to a (known or preferred) network.
Packets with probe requests can be monitored with a program like wireshark or tcpdump or any other of the available packet sniffers out there that support monitor interfaces.
(You will need a monitor interface to pick up the packets coming from devices not on your network)
Wireshark
--------------
Wireshark is a very well known, well supported & documented programme
Start a capture in wireshark with your card in monitor mode and then use the filter ;
wlan.fc.type_subtype eq 4
This will list all probe requests allowing you to see the Client's MAC address and probed ESSIDs
Drilling down deeper in the packet you can find more information which you may find interesting such as signal strength.
A good tip on how to find out what filter is required to focus on certain information, is to drill down and find the information you want, then simply select row of interest, and then ;
Right Click -> Apply as Filter -> Selected
Now you will see the required filter context and the filter will be in use.
Very handy to find out what the filter context is, as there are a lot...
But I was more looking for something to script with, so needed a CLI variant.
tcpdump
------------
If you're looking for a CLI solution for packet sniffing, then tcpdump is one of the first tools that comes to mind.
Again you will need an interface in monitor mode, let's say we have a mon0 interface, then you could use the below line to sniff for packets with probe requests;
tcpdump -i mon0 -e -s 256 type mgt subtype probe-req 2> /dev/null
(the 2> /dev/null to avoid the standard error message)
tcpdump works great, but when piping the output to a script I was having trouble with its buffering, even when using the -l switch.
---------
tshark is the CLI version of Wireshark and so output can be filtered using the filters which can also be used in the GUI version.
tshark -i wlan2mon -n -l subtype probereq
Using the -T switch we can further choose which fields we want using filters (which can be found using the aforementioned method in wireshark's GUI.
tshark -i mon0 -n -l subtype probereq -T fields -e wlan.sa -e radiotap.dbm_antsignal -e wlan_mgt.ssid
wlan.sa == source address
radiotap.dbm_antsignal == rssi
wlan_mgt.ssid == ESSID
Now with some scripting was able to make something come to life to satisfy my curiosity :D
It can (and probably will in the future) be improved in some areas, but for now it works more or less OK.
Anyways, enter shee.sh, a script to either log all seen probe requests or alert on seeing known or unknown client macs depending on the options chosen.
The script was written on, and intended for use on Kali Linux.
Easiest to first make the script executable;
chmod +x shee.sh
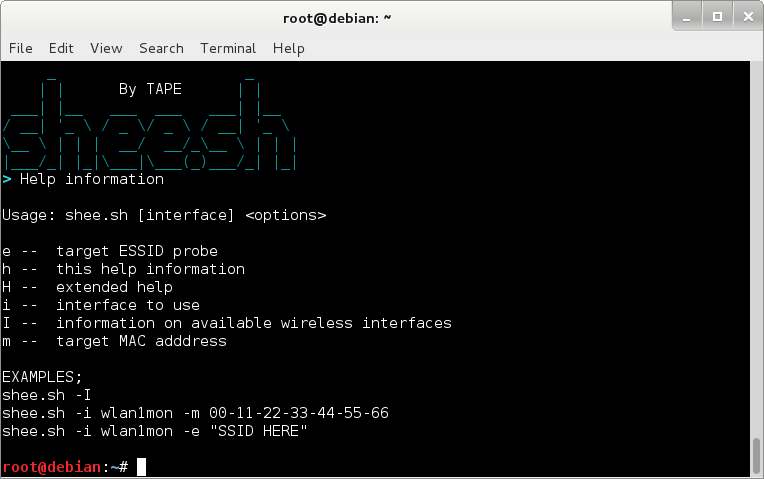
When running the script without any switches or with just the -h switch help info will be shown ;
./shee -h
There are input checks on the Interface (to make sure that the interface exists and is in monitor mode)
and also on the MAC address input (to make sure that correct syntax is used)
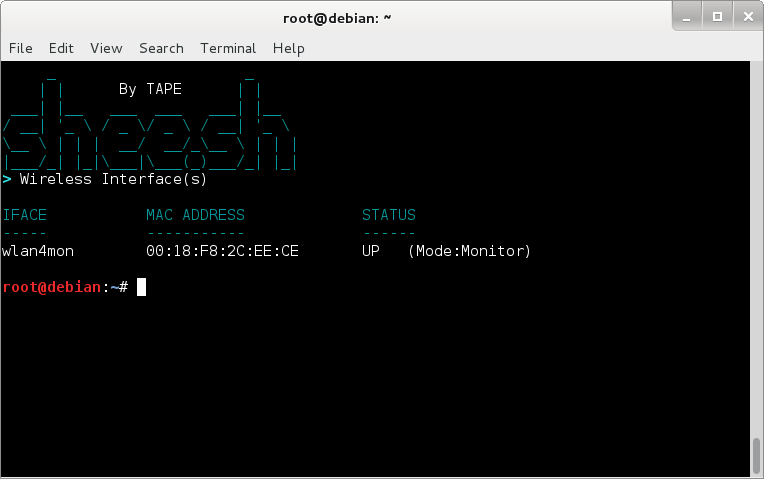
shee.sh requires a monitor interface to function, to check what wireless interfaces you have
and what their status is, you can use the -I switch ;
./shee.sh -I
The interface to use should be specified using the i switch.
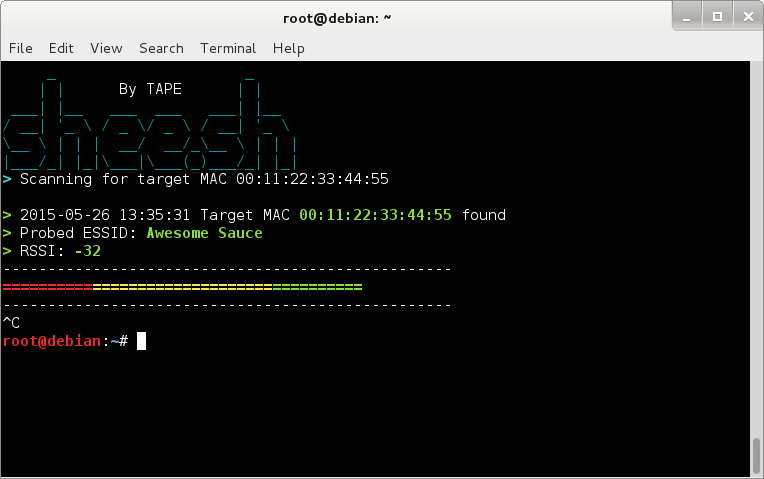
You can set the script up to sniff specific MAC addresses using the -m switch and specifying the MAC address.
The MAC address can either be entered using colons or hyphens;
00:11:22:33:44:55 or 00-11-22-33-44-55
./shee.sh -i wlan4mon -m 00:11:22:33:44:55
Or you can set it up to listen for a specific probed ESSID with the -e switch followed by the target ESSID (use quotation marks if spaces!) ;
./shee.sh -i wlan4mon -e "Awesome Sauce"
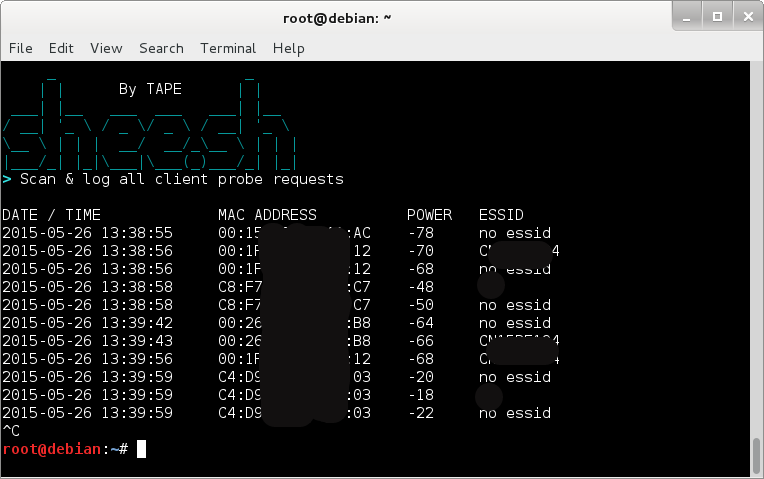
Or you can just set it up to simply log all clients probing about ;
./shee.sh -i wlan4mon
At the moment this function prints all it sees and does not (yet) only print new clients, something for me to think about ;)
All the 3 above scans will continue until stopped with Ctrl-C.
Including the -s switch will allow a sound alert to occur with each found Client for the above 3 options (if further switches are used then it is required to enter the mode) ;
./shee.sh -i wlan4mon -M 1 -m 00:11:22:33:44:55 -s
./shee.sh -i wlan4mon -M 2 -e "Awesome Sauce" -s
./shee.sh -i wlan4mon -M 3 -s
I will be slowly checking the script and improving where I can, but so far it seems like a decent start to the blog after a looong period of silence... (yes kids.. babies, houses and work do that :D )
As always, I appreciate any and all comments.
Script updated to v0.2 12-06-2015
Download link;
http://www.mediafire.com/view/vz2nea6bv1hq779/shee.sh
Useful/Interesting blogs/posts on this
============================