When DHCP is not enabled, you are not automatically given an IP address and the router is only allowing access via set IP addresses.
Basically this means that the router only works with static IP addresses which have been pre-assigned to the computers.
The range of the set IP addresses is variable, so we need to figure out how to find that out.
I am doing this on my test network which is an open network without mac filtering with DHCP disabled.
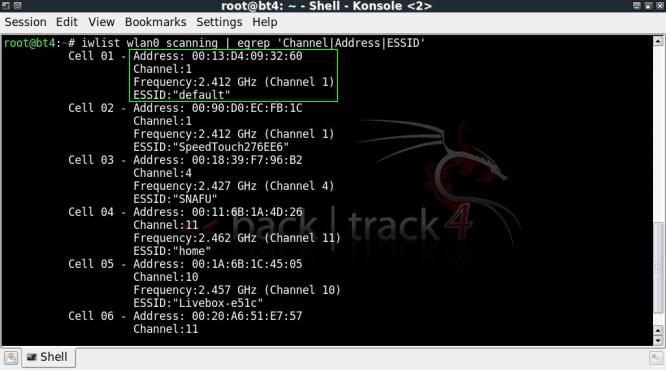
My test network is on channel 1, essid "default", bssid 00:13:D4:09:32:60
no encryption set and DHCP disabled
So if trying to connect with the connection manager WICD for instance, it will fail when trying to obtain the IP address.
This however does not mean we can't associate to the network, it just means we cant (yet) get an IP.
So to get a connection to the router we need the following information;
- The channel the network is on
- The ESSID
- Access Point MAC address
iwlist wlan0 scanning | egrep 'Channel|Address|ESSID'
Or of course can quickly run airodump-ng.
Now we re-configure our interface and enter the above information.
I first put the card down, as I like to control when it starts trying to access any network .
ifconfig wlan0 down
iwconfig wlan0 channel 1 essid default ap 00:13:D4:09:32:60
Check the input to be correct.
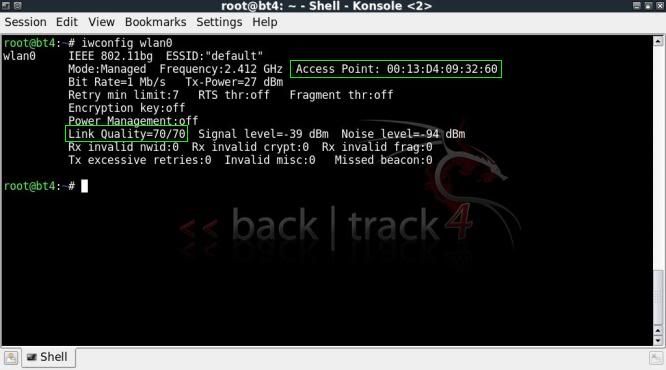
iwconfig wlan0
Note the link quality, no connection.
All is good to go, time to put the card up;
ifconfig wlan0 up
Now when checking we see that we have a connection with the access point !
iwconfig wlan0
So to check the IP address range in use there are a couple of options ;
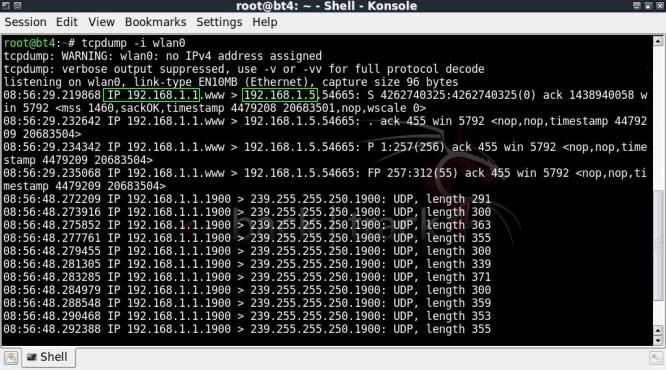
Using tcpdump;
tcpdump -i wlan0
This tool will simply show a running list of all packets sent, in the output there will be some IP addresses in plain text which of course can also help you on your way.
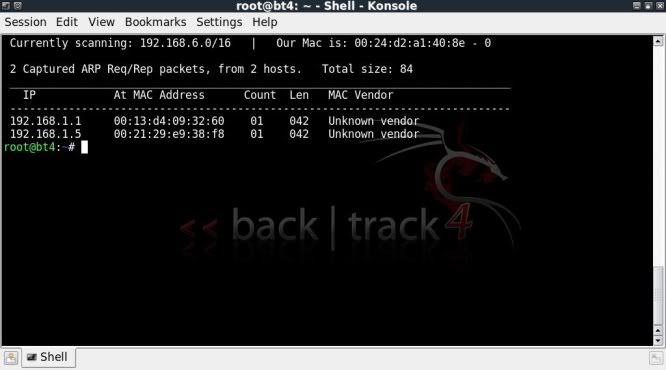
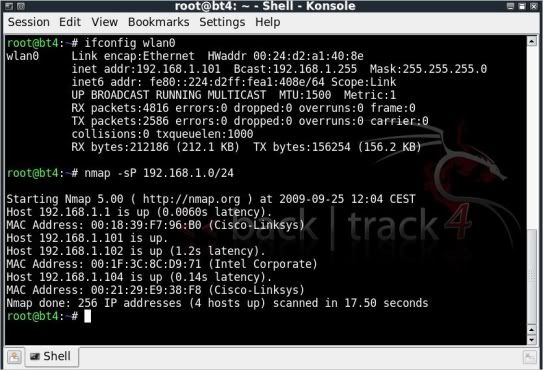
netdiscover -i wlan0
This scans possible IP ranges and will list the IP addresses found and the MAC addresses of the access point and any connected clients.
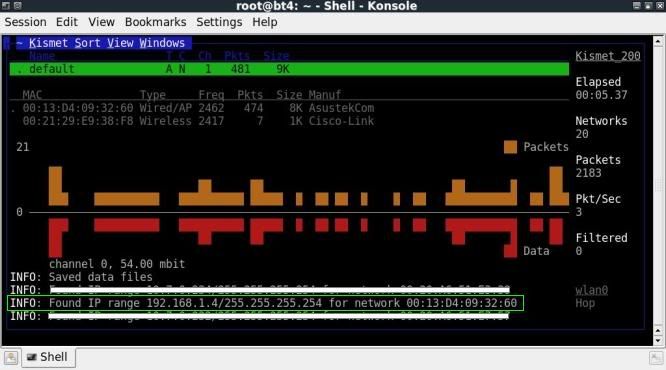
Monitoring with KISMET
Kismet will show IP ranges it has been able to discover as long as there is some activity from the client side.
The above examples have been made with a client connected to the router and for the kismet & tcpdump examples also some activity from the client side.
I was preparing this post playing around with 2 different clients, hence sometimes IP 192.168.1.4 and sometimes 192.168.1.5
When we have either an IP address from a connected client, or an IP address from the router so that we can make an educate guess as to a correct IP range we re-configure the interface again;
Setting the IP address and netmask;
ifconfig wlan0 192.168.1.4 netmask 255.255.255.0
Adding the gateway;
route add default gateway 192.168.1.1
Adding the DNS server;
sh -c "echo nameserver 208.67.222.222 > /etc/resolve.conf"
Of course if a user is already using the IP address, you cannot use the same one as it will cause conflicts.
You can however use the same IP address by kicking the associated client off the network with a deauth attack, possibly spoofing the mac address as well in case the IP is linked to a certain mac address.
My test network is not connected to the internet, however the above should help you on your way in understanding what can be done if having difficulty getting an IP.
You will not always need to enter the DNS server depending on what you are trying to accomplish on the network.
But in the above case the connection should be done and you are able to browse away to your heart's content !
A great reference to connecting to networks in Linux has been made by Virchanza;
http://virjacode.com/tutorials/linux_inet_connect.html