The below is based on being on the network to assess and to have an IP address assigned (DHCP).
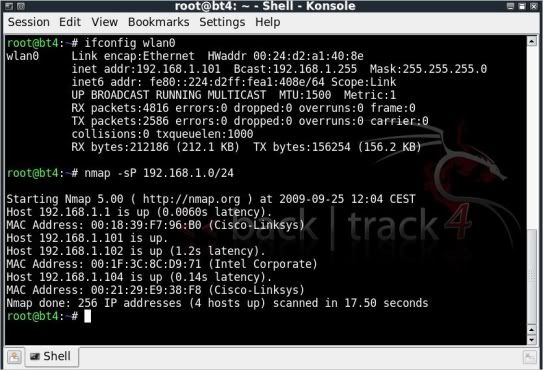
First of all of course, we need to identify the IP address of a target to scan.
This can be done is several ways, either using Netdiscover or Nmap.
With wlan0 being our interface best to check the ip your on with;
ifconfig wlan0
That should give you an idea on the IP range in use.
To find other IPs on the network you can then do ;
nmap -sP 192.168.1.0/24
Now in the OpenVAS Client window, start a new Task.
Go to Task --> New and rename if desired, here I renamed to test.
With the task selected, start a new scope.
Go to Scope --> New and rename if desired, here I renamed to testvictim.
You will need to connect to the server again, by clicking on the connect icon, same as done in previous post.
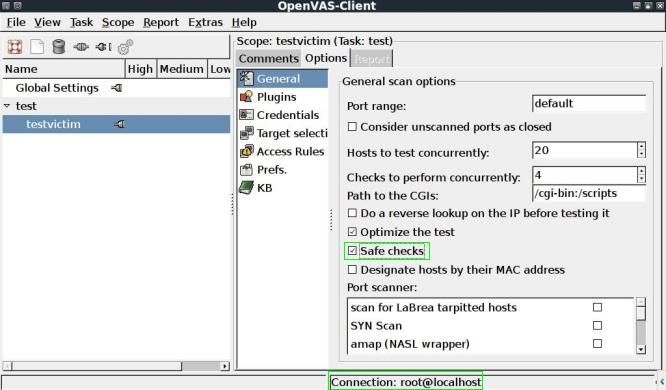
After connecting to the server (see again bottom right is mentioned; Connection: root@localhost) go to the General tab, here the only change I made was selecting "Safe checks".
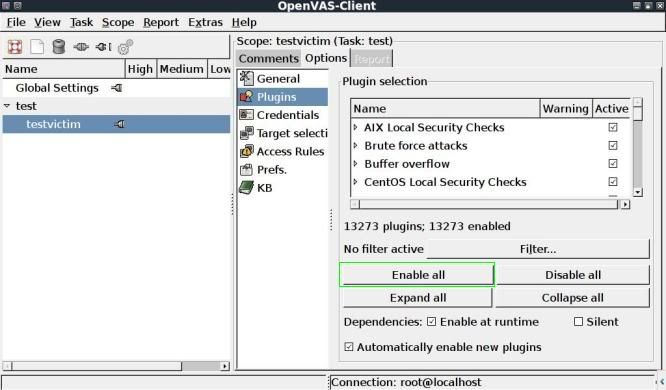
Then head to the Plugins tab, you can select the plugins to be used, in this case I used Enable all to use all plugins available.
Now time to select your target IP. I have chosen to pick 192.168.1.102.
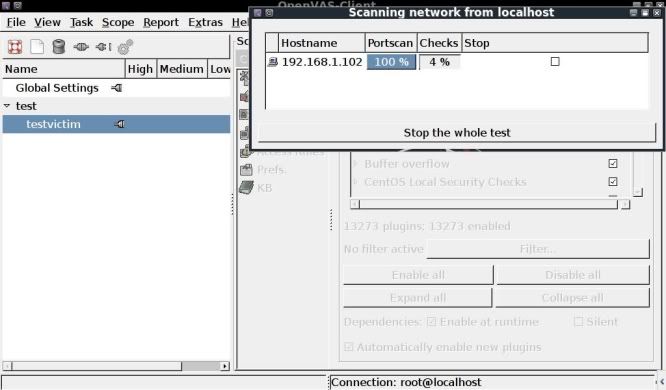
Now to finally start the scan !
Go to Scope --> Execute and the scan will commence, first scanning the ports, then checking them.
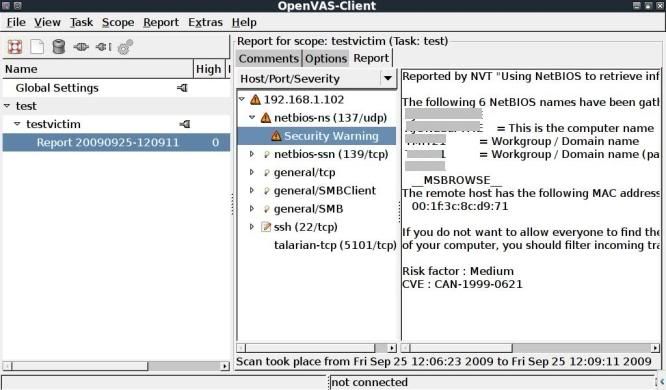
After a while with the scan complete, you will see a report appear under the testvictim scope.
Double clicking it will open it up on the right and you can go through the various warnings / messages noted.
Not much of interest noted from this scan, but the above is the basics of how to get started with vulnerability scanning of hosts on a network !
A lot of the info on the OpenVAS setup was seen on dookie2000ca YouTube video in which he shows the process from vulnerability assessment to auto_pwn-ing a box;
http://www.youtube.com/watch?v=BY2LCGUjm7k&feature=channel
Also excellent references of course found on OpenVAS' site;
www.OpenVAS.org
A great 101 guide ;
http://wald.intevation.org/frs/download.php/558/openvas-compendium-1.0.1.pdf



No comments:
Post a Comment