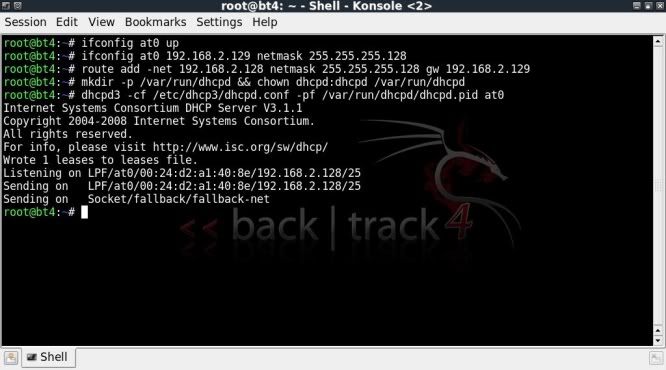
Here I will be looking at cracking password protected archive files with rarcrack which is included in the back|track 4 distro.
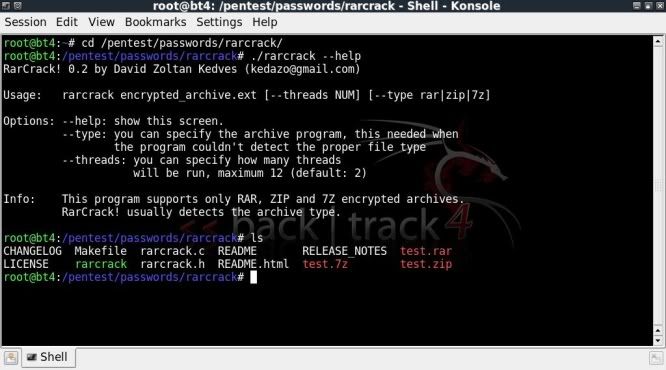
First lets navigate to rarcrack in back|track, see the help file and which files are located in the rarcrack directory.
cd /pentest/passwords/rarcrack
./rarcrack --help
ls
There are 3 test files included in the rarcrack directory, but lets try rarcrack on some of the files which I created which are on a USB drive; /media/4G/
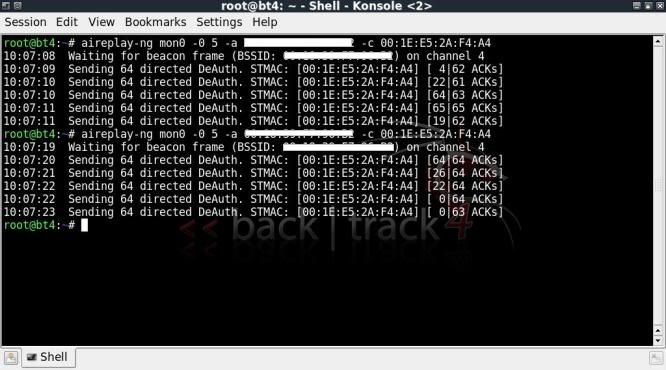
Starting an attack ;
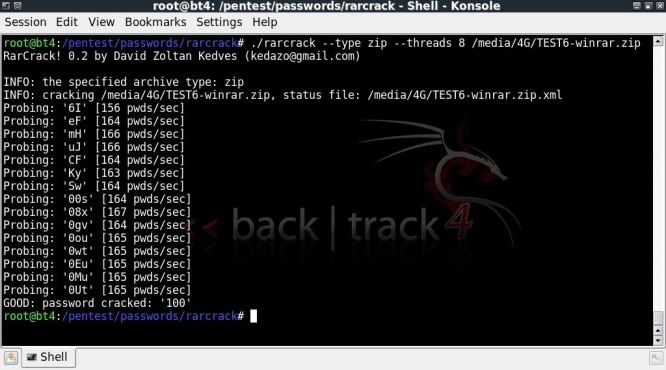
This below on a zip file created with WinRar;
./rarcrack --type zip --threads 8 /media/4G/TEST6-winrar.zip
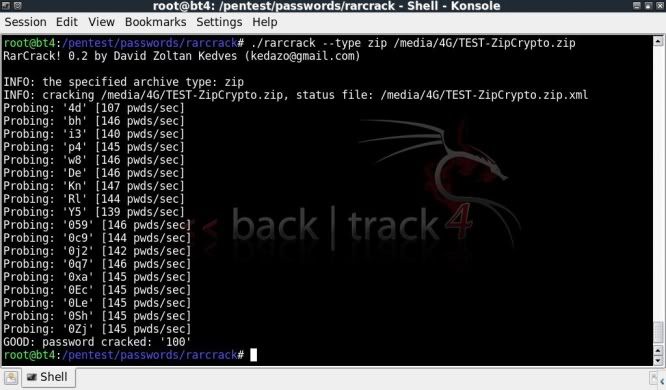
This one below on a zip file created in 7-Zip with ZipCrypto encryption;
./rarcrack --type zip --threads 8 /media/4G/TEST-ZipCrypto.zip
This one below on a 7z archive with AES256 encryption;
./rarcrack --type 7z --threads 8 /media/4G/TEST1-AES256.7z
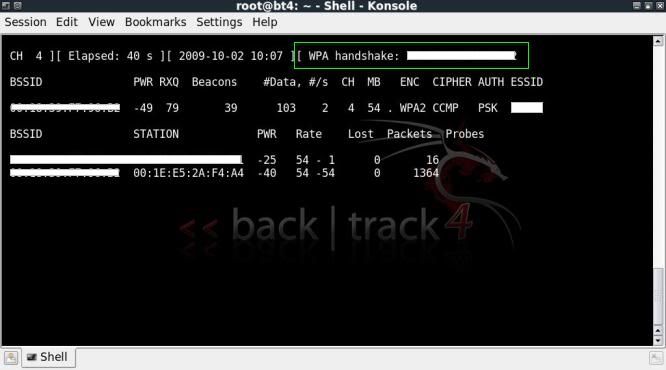
So Slow !When a crack attempt is started, an xml status file is created in the directory where the archive file is located.
So we can stop the crack and edit the values of the xml file to help speed up the cracking process.
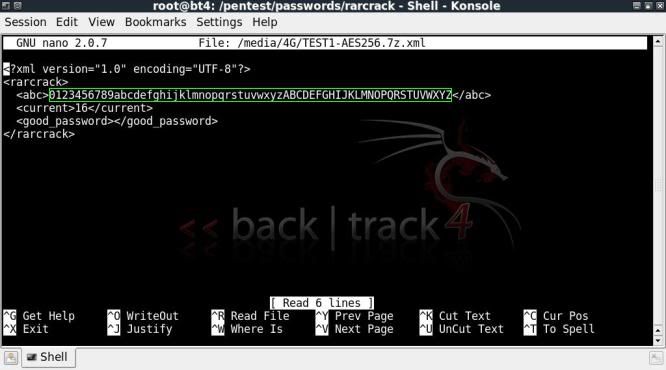
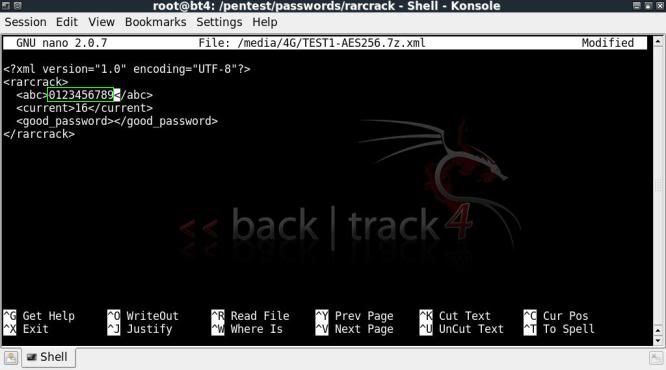
This xml file can be editted to change the character list being used for the crack, in this case as I know the
password is a numerical value, we can edit the xml file so that rarcrack only checks numbers;
nano /media/4G/TEST1-AES256.7z.xml
Changing the character set to numerical only;
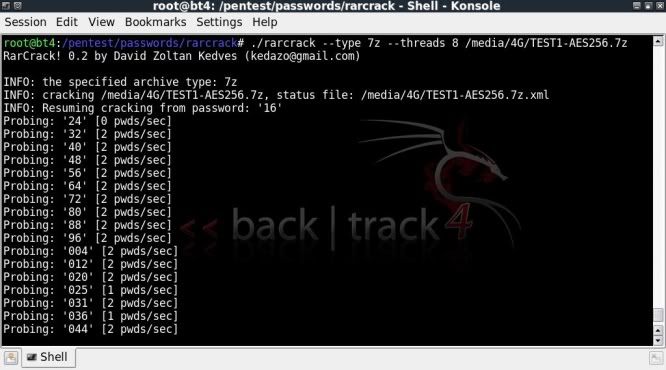
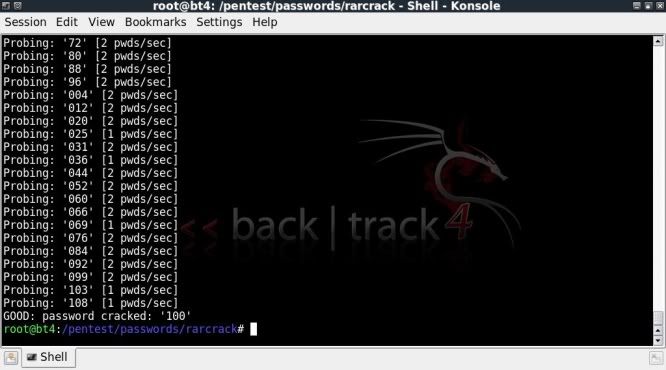
Now we restart the attack on the 7z file and the attack will resume but now only check numerical values;
./rarcrack --type 7z --threads 8 /media/4G/TEST1-AES256.7z
Video on the above using rarcrack can be found here ;
http://blip.tv/file/2816224or
http://www.youtube.com/watch?v=BMFn-jps3iY
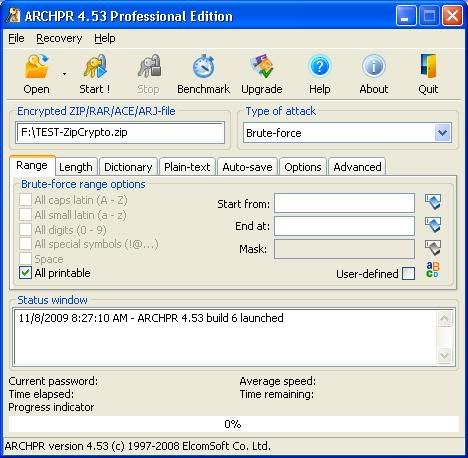
Although I am trying to stick to the back|track tools in my posts, I have to divert somewhat here and mention a Windows tool by Elcomsoft; "Advanced Archive Password Recovery" (ARCHPR).
It is a great tool and Elcomsoft have password recovery tools for a fantastic number of filetypes.
It has an easy interface with various cracking options such as Bruteforce and Dictionary attacks, and is also able to include characters which you think may be correct and mask those you want testing, as in; pass????.
The speed reached is much better in most cases than what rarcrack achieves and also is more flexible on which files can be chosen, although it does not support 7zip created archives.
With rarcrack I was having trouble with it catching the passwords on zip files with AES encryption, ARCHPR has no trouble with these.
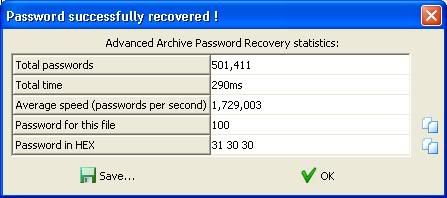
ARCHPR in action with bruteforce options ;
Dictionary attack ;