Security through Obscurity
========================
Methods of hiding information without it appearing that there is any information, is an interesting topic and I recently got thinking on it following a few image challenges which were posted on various security sites a while ago.
I failed miserably at the challenges, but at least picked a few things up on the way to my epic fail..
Although security through obscurity is not truly secure, it is an interesting method of getting information to someone whilst being hidden to the un-informed.
This post is about the simple methods possible to use to hide info from the un-informed, the methods described are not supposed to be terribly secure, but rather, interesting.
The below done on VMWare Image of BackTrack5 R3 and on a Windows 7 PC.
The first stage is to have a look at the file information and see what information is revealed.
LOOKING AT THE BASIC INFORMATION OF AN IMAGE FILE
====================================================
Exif Data
-------------
Image files often contain Exif data which can be read in the hex of a file, but using a tool such as Exiftool greatly simplifies this.
exiftool will also give you information on the file type.
exiftool can be run from the command line, and there is also a Windows GUI for exiftool available.
run 'exiftool file.jpg' from the command line and you will be presented with information available in the file which can include things like GPS positions camera make/model, software, comments, etc etc.
General usage on command line ;
exiftool matrix.jpg
There are a huge amount of options possible with exiftool, and it is a fantastic tool to manipulate information in image files.
Check out the links at the bottom of this post for further information.
Hex Data
--------------
Nearly all files have a so-called 'header' and 'trailer', some files types only have a 'header'.
The header and trailer of files are sections of the file which identify the file type so Operating Systems understand what fileformat they are dealing with.
These headers and trailers are typically unique for the file type and a good resource for checking the file signatures is ; http://www.garykessler.net/library/file_sigs.html
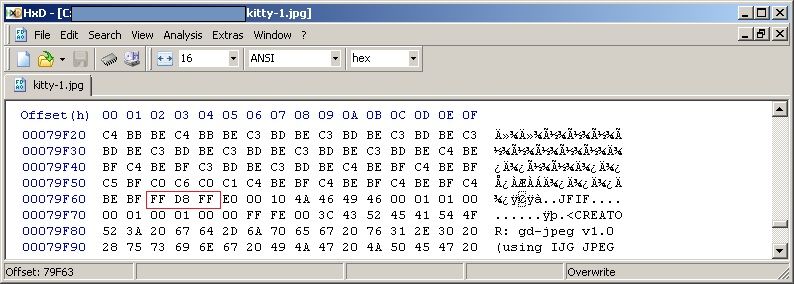
So when we have a file to examine, for instance a JPG file, open it with a Hex Editor (I am using Windows based HxD Hex Editor) and have a look at the file headers and trailers.
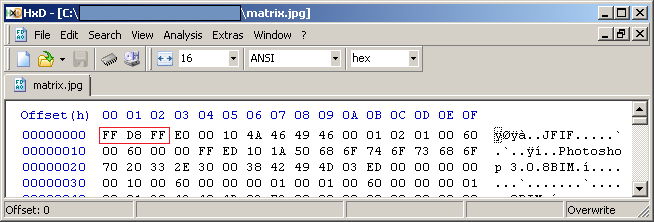
Image file matrix.jpg;
You will see that the file starts with 'FF D8 FF' and ends with 'FF D9'.
Image file header;
Image file trailer;
If there is extra data after the trailer FF D9, then it is possible that there is some sort of extra data to be found.
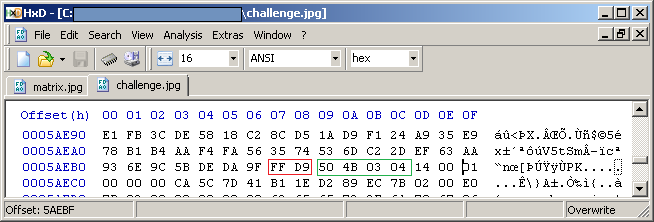
The information after the FF D9 trailer can give you an idea of what the extra information could be. In the below example the information after file trailer FF D9 starts with a known file header '50 4B 03 04' (PK.. in ACSII format), so it would appear that there is a zip file appended to the JPG.
So by checking the information in a Hex editor you can quickly see whether the file appears to be what it is supposed to be, or whether something looks out of the ordinary.
ATTACHING INFORMATION TO A FILE
=================================
With many file formats it is possible to attach file information which can later be retrieved based on the above principal of files having headers and trailers.
kitty-hack1.jpg;
kitty-hack2.jpg;
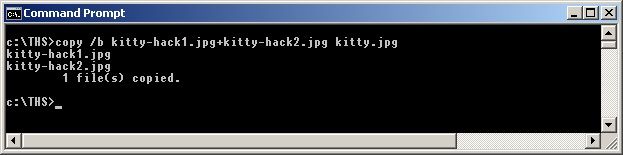
For instance in Windows with 'Command Prompt';
copy /b kitty-hack1.jpg + kitty-hack2.jpg kitty.jpg
In Linux with 'cat' (lolz, no pun intended ;) ) ;
cat kitty-hack1.jpg kitty-hack2.jpg > kitty.jpg
The above commands will copy/append the data from kitty-hack2.jpg to kitty-hack1.jpg and name
the output file to kitty.jpg.
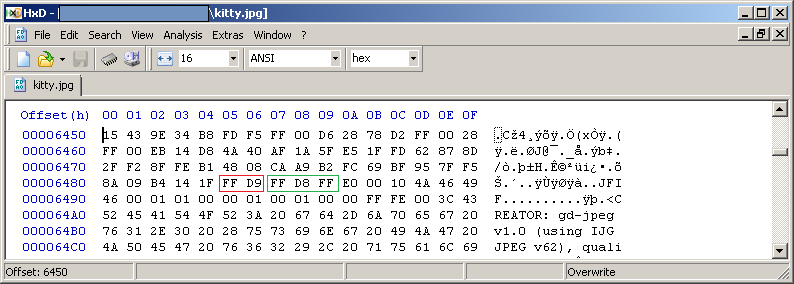
When checking the kitty.jpg in a Hex Editor you will see that there is a JPG trailer 'FF D9' followed by a JPG header 'FF D8 FF' of the second file.
So although it looks like 1 file, there are in fact 2 files which can be confirmed by this check in a Hex editor.
I cant post the kitty.jpg here as the photo sharing site I use (Photobucket) removes any extraneous information after the first found trailer on jpeg files.
This 'limitation' could be bypassed though by converting the 1st image to .bmp format (which has no trailer) and copying the 2nd image to the bmp file ;
Result after the conversion of the 1st image to .bmp format and then appending kitty-hack2.jpg with the above mentioned copy /b method ;
copy /b kitty-hack1.bmp + kitty-hack2.jpg kitty.jpg

Just by looking at the hex you would see something is up, and with a search for the JPG header 'FF D8 FF' in the above image you will find that the 2nd file is appended.
This method of hiding files/data by copying/appending to files can be done with many filetypes.
You can also for instance place files in a zip archive and copy this archive to an image in the
same way (zip secret files, append to image file, image file can then also be opened with Archive tool);
copy /b image.jpg + info.zip hidden.jpg
Of course it should be noted that this is not at all a secure way of hiding information, but for those not in the know, there is no indication that extra information is even there.
For instance I found this one online a while ago, cant remember where, but in any case if anyone objects to it being posted here, just say the word and I'll take it down.(image/content not made by me)
Below is a .png file and contains a .rar file with content.
STEGANOGRAPHY
================
Stegonography is the method of hiding information in a file in a way that only the recipient
of the file should know or be able to extract.
There are quite a few programs out there that can do this, but none are really maintained.
Steghide is a popular one which can hide information in various filetypes (JPG/BMP/WAV/AU)
and is installed on most PenTest distros.
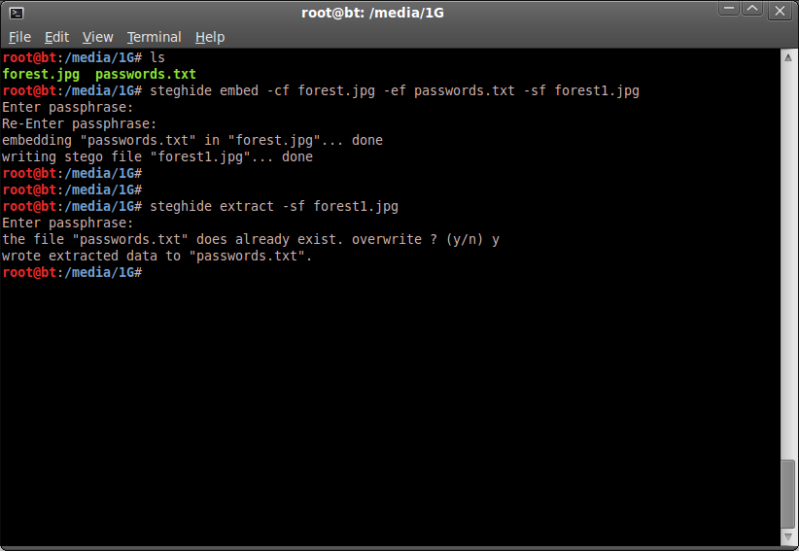
If for instance you have a file 'passwords.txt' and want to hide it in an image 'forest.jpg'
you would run steghide as follows ;
steghide embed -cf forest.jpg -ef passwords.txt
You can also specify a different filename for the output using -sf ;
steghide embed -cf forest.jpg -ef passwords.txt -sf forest1.jpg
You will be prompted to enter a password which you can do or else leave blank for no password.
To later retrieve this information you would run steghide as follows ;
steghide extract -sf forest1.jpg
You will be prompted for a password, if there is none, simply hit enter to leave blank
and steghide will attempt to extract the hidden data.
forest.jpg;

forest1.jpg
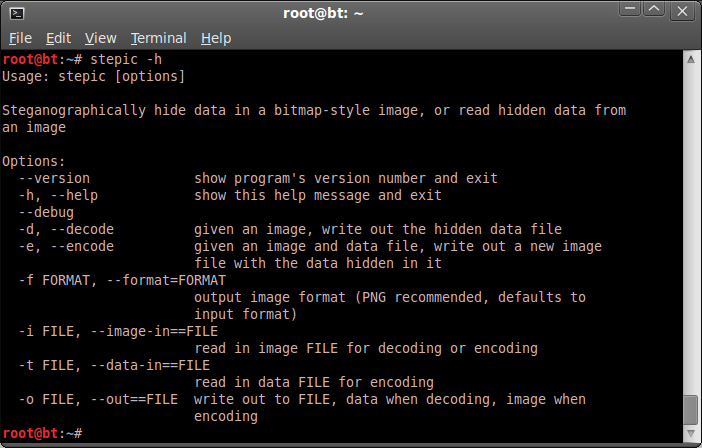
Another interesting one is 'stepic' which is not installed on stock BT5R3 but can easily be done by ;
apt-get install python-stepic
stepic uses LSB (least significant bit) methods to hide any data in an existing png file. It does not include a password / encryption option and so is not a secure method, but works fine to hide data.
stepic -h
FILE CARVING
=============
File Carving is the process of extracting files from data based on headers and trailers.
This is usually done on whole disc images, mainly for data recovery purposes on for instance damaged or unmounted drives requiring data extraction.
Some programs used for such operations on linux and available on most PenTest distros are for instance 'foremost' & ' scalpel'
The same principal however can be used on a single file if it appears that extra information is available within the file.
So if you find a JPG file (file1.jpg) with extra information after the expected trailer,
you could cut the first part of the file from the header 'DD F8 FF' (start of JPG file)
until the end of JPG file (denominated with FF D9).
In your Hex editor select and cut the data away from (the first if there are more than one) 'FF D8 FF'
upto and including 'FF D9' and save the file.
(you could then paste the cut section to a new file in HxD and save as file2.jpg to see
whether it matches what you saw in initial JPG file for verification)
You should then have a stripped file which you can then check again for file properties.
This file may have different properties, and so again you may have to look for headers and trailers.
(is it a different filetype ? check headers and trailers with the aforementioned file signatures link)
The above sequence is just a simple example. Possibly data you have will require different methods,
however for this example it is to simply show how you can 'carve' one file away from another
when dealing with simple appended files.
BASIC ENCODING/ENCRYPTION
----------------------------------------
Some basic encoding and/or encryption can also be used to further obfuscate the hidden data.
The below examples are very weak methods of doing such, however it is simply to show how
data can further be made difficult to retrieve if you are not aware of the methods used to hide it.
BASE64
base64 is a method to convert binary data to ASCII characters.
This could be used to for instance append data to an image file in ASCII form even further obfuscating the data.
base64 is installed on most linux distros, to use simply ;
base64 inputfile > outputfile
to decode ;
base64 -d filein > fileout
On windows you could download the bas64.exe from www.fourmilab.ch
base64.exe -e inputfile outputfile
to decode
base64.exe -d filein fileout
ROT13
ROT13 is an 'encryption' that basically moves all letters of the alphabet up 13 letters, a variant of the Caeser shift cipher.
ROT5 is the same method based on moving numeric values up 5 numbers.
Using them together is sometimes referred to as ROT18.
So it is easy to identify and encode or decode, even more so if you have a reference of some kind and is
NOT a secure encryption method, but fun to play with.
If you were to see a line of text like ; uggc://jjj.paa.pbz
You can see that there are similarities with a normal web address, but the wording/letters don't appear to match up to what you would expect.
Run a ROT13 script over the line uggc://jjj.paa.pbz ;
echo uggc://jjj.paa.pbz | tr a-zA-Z n-za-mN-ZA-M
and you will find outcome ; http://www.cnn.com
If there are digits there you could also include a ROT5 script and make it a ROT18.
So a quick and dirty ROT18 one-liner could look like the below ;
encoding with ROT18
echo "My birthday is 01-01-1900" | tr a-zA-Z0-45-9 n-za-mN-ZA-M5-90-4
Zl oveguqnl vf 56-56-6455
Decoding with ROT18
echo "Zl oveguqnl vf 56-56-6455" | tr a-zA-Z0-45-9 n-za-mN-ZA-M5-90-4
My birthday is 01-01-1900
I made a quick and dirty rot18 encoding/decoding script for shits and giggles should it be of interest
which can be run on either input or on a file.
Download;
http://www.mediafire.com/file/qvfr0p0006oqzyp/rot18.sh
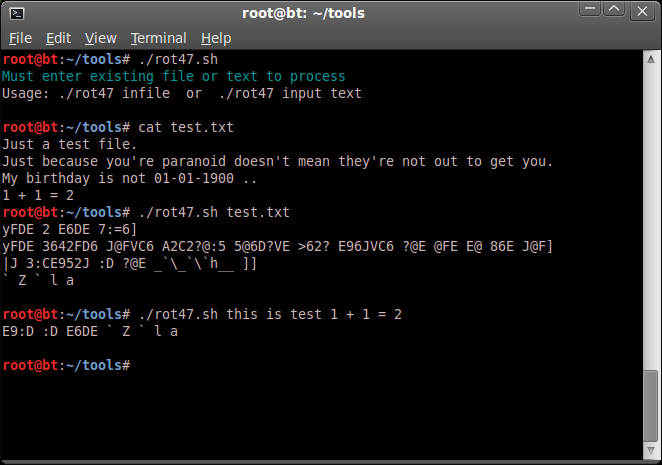
A similar, but more elaborate variation is the rot47 encryption.
Same as the above, a simple script on rot47 encoding / decoding ;
http://www.mediafire.com/file/83pag27jmfvqgqa/rot47.sh
Very basic, but does the job.
Consider this scenario of keeping/sharing your passwords ;
------------------------------------------------------------------------------
-> Create your passwords.txt
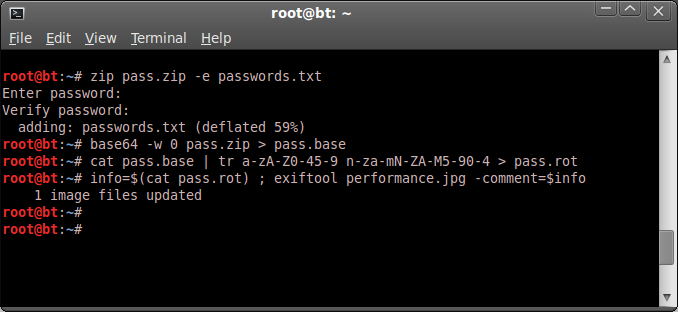
-> Zip passwords.txt and password protect it to pass.zip.
zip pass.zip -e passwords.txt
-> Encode passwords.zip with base64 to pass.base
base64 -w 0 pass.zip > pass.base
(the '-w 0' to prevent linewraps that make it easer to add to an image comment.)
You could even ROT18 the file to further obfuscate the data ;
ROT18 encode the base64 file
cat pass.base | tr a-zA-Z0-45-9 n-za-mN-ZA-M5-90-4 > pass.rot
-> Find or create a nice image that would not arouse suspicion.
As the amount of data is so small, it can be included in the image comment, which is probably safer as if you are using image hosting websites they may strip off superfluous info from the jpg.
-> Add the data to the image comment using exiftool.
info=$(cat pass.rot) ; exiftool performance.jpg -comment=$info
-> Upload image file to photo or file sharing site and send yourself the link or whatever is appropriate.
Performance.jpg ;
Retrieval ;
exiftool performance.jpg -b -comment > out.put
ROT18 decode the file
cat out.put | tr a-zA-Z0-45-9 n-za-mN-ZA-M5-90-4 > rot.out
Decode the base64
base64 -d rot.out > pass.zip
Unzip the created .zip file.
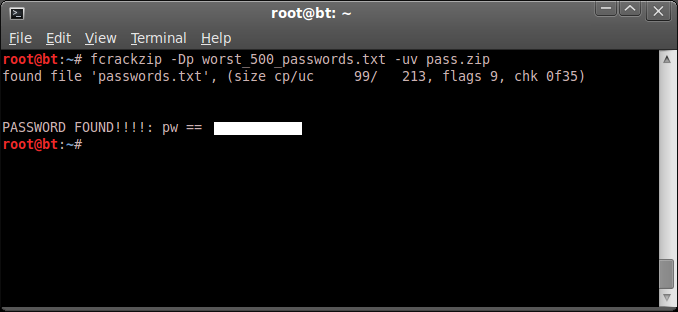
unzip pass.zip
(password hint; worst 500 passwords)
fcrackzip -Dp worst_500_passwords.txt -uv pass.zip
A highly cumbersome and not terribly secure method of doing something simple, but still food for thought on what is possible on hiding information in 'plain sight'.
Team THS Challenge
================
I made the below file for the Top Hat Security team for an article on this same subject in our members magazine, based on the above possibilities.
See what you can discover and post the outcome here or on the THS forums !
Download the challenge (challenge.jpg) here ;
http://www.mediafire.com/?4sgybntg3qy60ov
Edit dd 04-02-2013
No takers / results on the above THS challenge.jpg file ?!
Some hints then..
The file challenge.jpg contains a password protected zip file, contents of which can be
extracted with a password which can be found in the challenge.jpg image data..
The challenge.jpg actually has 4 images (including challenge.jpg) and the final outcome
of the challenge should be a text file starting with ;
Well done !
Challenge complete, hope it was enjoyable !
All required processes are described in the above post, but if you're stuck, leave a comment
with what you have done / tried and I will see if it merrits a response ;)
CREDITS/LINKAGE ;
==================
Top Hat Security
http://top-hat-sec.com/main/
Exiftool
http://www.sno.phy.queensu.ca/~phil/exiftool/
Exiftool GUI
http://freeweb.siol.net/hrastni3/foto/exif/exiftoolgui.htm
Exiftool forums
http://u88.n24.queensu.ca/exiftool/forum/index.php
HxD Hex Editor
http://mh-nexus.de/en/hxd/
Steghide
http://steghide.sourceforge.net/download.php
Stegdetect - Outguess
http://www.outguess.org/detection.php
Stepic
http://domnit.org/blog/2007/02/stepic-explanation.html
File Signatures
http://www.garykessler.net/library/file_sigs.html
Some incredibly annoying challenges can be found here ;
http://www.wixxerd.com/challenges/
========================
Methods of hiding information without it appearing that there is any information, is an interesting topic and I recently got thinking on it following a few image challenges which were posted on various security sites a while ago.
I failed miserably at the challenges, but at least picked a few things up on the way to my epic fail..
Although security through obscurity is not truly secure, it is an interesting method of getting information to someone whilst being hidden to the un-informed.
The below done on VMWare Image of BackTrack5 R3 and on a Windows 7 PC.
The first stage is to have a look at the file information and see what information is revealed.
LOOKING AT THE BASIC INFORMATION OF AN IMAGE FILE
====================================================
Exif Data
-------------
Image files often contain Exif data which can be read in the hex of a file, but using a tool such as Exiftool greatly simplifies this.
exiftool will also give you information on the file type.
exiftool can be run from the command line, and there is also a Windows GUI for exiftool available.
run 'exiftool file.jpg' from the command line and you will be presented with information available in the file which can include things like GPS positions camera make/model, software, comments, etc etc.
General usage on command line ;
exiftool matrix.jpg
There are a huge amount of options possible with exiftool, and it is a fantastic tool to manipulate information in image files.
Check out the links at the bottom of this post for further information.
Hex Data
--------------
Nearly all files have a so-called 'header' and 'trailer', some files types only have a 'header'.
The header and trailer of files are sections of the file which identify the file type so Operating Systems understand what fileformat they are dealing with.
These headers and trailers are typically unique for the file type and a good resource for checking the file signatures is ; http://www.garykessler.net/library/file_sigs.html
So when we have a file to examine, for instance a JPG file, open it with a Hex Editor (I am using Windows based HxD Hex Editor) and have a look at the file headers and trailers.
Image file matrix.jpg;
You will see that the file starts with 'FF D8 FF' and ends with 'FF D9'.
Image file header;
Image file trailer;
If there is extra data after the trailer FF D9, then it is possible that there is some sort of extra data to be found.
The information after the FF D9 trailer can give you an idea of what the extra information could be. In the below example the information after file trailer FF D9 starts with a known file header '50 4B 03 04' (PK.. in ACSII format), so it would appear that there is a zip file appended to the JPG.
So by checking the information in a Hex editor you can quickly see whether the file appears to be what it is supposed to be, or whether something looks out of the ordinary.
ATTACHING INFORMATION TO A FILE
=================================
With many file formats it is possible to attach file information which can later be retrieved based on the above principal of files having headers and trailers.
kitty-hack1.jpg;
kitty-hack2.jpg;
For instance in Windows with 'Command Prompt';
copy /b kitty-hack1.jpg + kitty-hack2.jpg kitty.jpg
In Linux with 'cat' (lolz, no pun intended ;) ) ;
cat kitty-hack1.jpg kitty-hack2.jpg > kitty.jpg
The above commands will copy/append the data from kitty-hack2.jpg to kitty-hack1.jpg and name
the output file to kitty.jpg.
When checking the kitty.jpg in a Hex Editor you will see that there is a JPG trailer 'FF D9' followed by a JPG header 'FF D8 FF' of the second file.
So although it looks like 1 file, there are in fact 2 files which can be confirmed by this check in a Hex editor.
I cant post the kitty.jpg here as the photo sharing site I use (Photobucket) removes any extraneous information after the first found trailer on jpeg files.
This 'limitation' could be bypassed though by converting the 1st image to .bmp format (which has no trailer) and copying the 2nd image to the bmp file ;
Result after the conversion of the 1st image to .bmp format and then appending kitty-hack2.jpg with the above mentioned copy /b method ;
copy /b kitty-hack1.bmp + kitty-hack2.jpg kitty.jpg

Just by looking at the hex you would see something is up, and with a search for the JPG header 'FF D8 FF' in the above image you will find that the 2nd file is appended.
This method of hiding files/data by copying/appending to files can be done with many filetypes.
You can also for instance place files in a zip archive and copy this archive to an image in the
same way (zip secret files, append to image file, image file can then also be opened with Archive tool);
copy /b image.jpg + info.zip hidden.jpg
Of course it should be noted that this is not at all a secure way of hiding information, but for those not in the know, there is no indication that extra information is even there.
For instance I found this one online a while ago, cant remember where, but in any case if anyone objects to it being posted here, just say the word and I'll take it down.(image/content not made by me)
Below is a .png file and contains a .rar file with content.
STEGANOGRAPHY
================
Stegonography is the method of hiding information in a file in a way that only the recipient
of the file should know or be able to extract.
There are quite a few programs out there that can do this, but none are really maintained.
Steghide is a popular one which can hide information in various filetypes (JPG/BMP/WAV/AU)
and is installed on most PenTest distros.
If for instance you have a file 'passwords.txt' and want to hide it in an image 'forest.jpg'
you would run steghide as follows ;
steghide embed -cf forest.jpg -ef passwords.txt
You can also specify a different filename for the output using -sf ;
steghide embed -cf forest.jpg -ef passwords.txt -sf forest1.jpg
You will be prompted to enter a password which you can do or else leave blank for no password.
To later retrieve this information you would run steghide as follows ;
steghide extract -sf forest1.jpg
You will be prompted for a password, if there is none, simply hit enter to leave blank
and steghide will attempt to extract the hidden data.
forest.jpg;

forest1.jpg
Another interesting one is 'stepic' which is not installed on stock BT5R3 but can easily be done by ;
apt-get install python-stepic
stepic uses LSB (least significant bit) methods to hide any data in an existing png file. It does not include a password / encryption option and so is not a secure method, but works fine to hide data.
stepic -h
FILE CARVING
=============
File Carving is the process of extracting files from data based on headers and trailers.
This is usually done on whole disc images, mainly for data recovery purposes on for instance damaged or unmounted drives requiring data extraction.
Some programs used for such operations on linux and available on most PenTest distros are for instance 'foremost' & ' scalpel'
The same principal however can be used on a single file if it appears that extra information is available within the file.
So if you find a JPG file (file1.jpg) with extra information after the expected trailer,
you could cut the first part of the file from the header 'DD F8 FF' (start of JPG file)
until the end of JPG file (denominated with FF D9).
In your Hex editor select and cut the data away from (the first if there are more than one) 'FF D8 FF'
upto and including 'FF D9' and save the file.
(you could then paste the cut section to a new file in HxD and save as file2.jpg to see
whether it matches what you saw in initial JPG file for verification)
You should then have a stripped file which you can then check again for file properties.
This file may have different properties, and so again you may have to look for headers and trailers.
(is it a different filetype ? check headers and trailers with the aforementioned file signatures link)
The above sequence is just a simple example. Possibly data you have will require different methods,
however for this example it is to simply show how you can 'carve' one file away from another
when dealing with simple appended files.
BASIC ENCODING/ENCRYPTION
----------------------------------------
Some basic encoding and/or encryption can also be used to further obfuscate the hidden data.
The below examples are very weak methods of doing such, however it is simply to show how
data can further be made difficult to retrieve if you are not aware of the methods used to hide it.
BASE64
base64 is a method to convert binary data to ASCII characters.
This could be used to for instance append data to an image file in ASCII form even further obfuscating the data.
base64 is installed on most linux distros, to use simply ;
base64 inputfile > outputfile
to decode ;
base64 -d filein > fileout
On windows you could download the bas64.exe from www.fourmilab.ch
base64.exe -e inputfile outputfile
to decode
base64.exe -d filein fileout
ROT13
ROT13 is an 'encryption' that basically moves all letters of the alphabet up 13 letters, a variant of the Caeser shift cipher.
ROT5 is the same method based on moving numeric values up 5 numbers.
Using them together is sometimes referred to as ROT18.
So it is easy to identify and encode or decode, even more so if you have a reference of some kind and is
NOT a secure encryption method, but fun to play with.
If you were to see a line of text like ; uggc://jjj.paa.pbz
You can see that there are similarities with a normal web address, but the wording/letters don't appear to match up to what you would expect.
Run a ROT13 script over the line uggc://jjj.paa.pbz ;
echo uggc://jjj.paa.pbz | tr a-zA-Z n-za-mN-ZA-M
and you will find outcome ; http://www.cnn.com
If there are digits there you could also include a ROT5 script and make it a ROT18.
So a quick and dirty ROT18 one-liner could look like the below ;
encoding with ROT18
echo "My birthday is 01-01-1900" | tr a-zA-Z0-45-9 n-za-mN-ZA-M5-90-4
Zl oveguqnl vf 56-56-6455
Decoding with ROT18
echo "Zl oveguqnl vf 56-56-6455" | tr a-zA-Z0-45-9 n-za-mN-ZA-M5-90-4
My birthday is 01-01-1900
I made a quick and dirty rot18 encoding/decoding script for shits and giggles should it be of interest
which can be run on either input or on a file.
Download;
http://www.mediafire.com/file/qvfr0p0006oqzyp/rot18.sh
A similar, but more elaborate variation is the rot47 encryption.
Same as the above, a simple script on rot47 encoding / decoding ;
http://www.mediafire.com/file/83pag27jmfvqgqa/rot47.sh
Very basic, but does the job.
Consider this scenario of keeping/sharing your passwords ;
------------------------------------------------------------------------------
-> Create your passwords.txt
-> Zip passwords.txt and password protect it to pass.zip.
zip pass.zip -e passwords.txt
-> Encode passwords.zip with base64 to pass.base
base64 -w 0 pass.zip > pass.base
(the '-w 0' to prevent linewraps that make it easer to add to an image comment.)
You could even ROT18 the file to further obfuscate the data ;
ROT18 encode the base64 file
cat pass.base | tr a-zA-Z0-45-9 n-za-mN-ZA-M5-90-4 > pass.rot
-> Find or create a nice image that would not arouse suspicion.
As the amount of data is so small, it can be included in the image comment, which is probably safer as if you are using image hosting websites they may strip off superfluous info from the jpg.
-> Add the data to the image comment using exiftool.
info=$(cat pass.rot) ; exiftool performance.jpg -comment=$info
-> Upload image file to photo or file sharing site and send yourself the link or whatever is appropriate.
Performance.jpg ;
Retrieval ;
exiftool performance.jpg -b -comment > out.put
ROT18 decode the file
cat out.put | tr a-zA-Z0-45-9 n-za-mN-ZA-M5-90-4 > rot.out
Decode the base64
base64 -d rot.out > pass.zip
Unzip the created .zip file.
unzip pass.zip
(password hint; worst 500 passwords)
fcrackzip -Dp worst_500_passwords.txt -uv pass.zip
A highly cumbersome and not terribly secure method of doing something simple, but still food for thought on what is possible on hiding information in 'plain sight'.
Team THS Challenge
================
I made the below file for the Top Hat Security team for an article on this same subject in our members magazine, based on the above possibilities.
See what you can discover and post the outcome here or on the THS forums !
Download the challenge (challenge.jpg) here ;
http://www.mediafire.com/?4sgybntg3qy60ov
Edit dd 04-02-2013
No takers / results on the above THS challenge.jpg file ?!
Some hints then..
The file challenge.jpg contains a password protected zip file, contents of which can be
extracted with a password which can be found in the challenge.jpg image data..
The challenge.jpg actually has 4 images (including challenge.jpg) and the final outcome
of the challenge should be a text file starting with ;
Well done !
Challenge complete, hope it was enjoyable !
All required processes are described in the above post, but if you're stuck, leave a comment
with what you have done / tried and I will see if it merrits a response ;)
CREDITS/LINKAGE ;
==================
Top Hat Security
http://top-hat-sec.com/main/
Exiftool
http://www.sno.phy.queensu.ca/~phil/exiftool/
Exiftool GUI
http://freeweb.siol.net/hrastni3/foto/exif/exiftoolgui.htm
Exiftool forums
http://u88.n24.queensu.ca/exiftool/forum/index.php
HxD Hex Editor
http://mh-nexus.de/en/hxd/
Steghide
http://steghide.sourceforge.net/download.php
Stegdetect - Outguess
http://www.outguess.org/detection.php
Stepic
http://domnit.org/blog/2007/02/stepic-explanation.html
File Signatures
http://www.garykessler.net/library/file_sigs.html
Some incredibly annoying challenges can be found here ;
http://www.wixxerd.com/challenges/











Brilliant article. Now i need hidden info from a .png file extracted which is "Final_Answer.txt" from the image. The password is "admin" for the .zip file without quotes and i need to use the password given to extract the hidden information. I've tried everything i could but no success. Email is dispols@yahoo.com.
ReplyDeleteDL:https://rapidshare.com/#!download|423p10|2793440222|Hackyard%20Security%20Group.zip|2323|0|0
Hints:
Hint1: png
Hint2: You must obtain a file called Final_Answer.txt which contain the final answer.
Hint3: A(yes) B(no) C(no)
Hey man,
DeleteActually most of the information needed is in the above blogpost.
> The file you uploaded is not a zip file, from a quick look at the hex there is a png file with a zip file attached.
So rename the file correctly to .png and carve the zip file from the end of the file.
The resulting zip file is only 4KB, with a directory and a password protected file called hint.txt
The image file is still 2,21MB which seems too large, and possibly something more remaining to extract.
> Cracked the zip file ;
password is : admin
> The hint.txt contains the following text ;
Password is: Hackyard Security Group
So from this information it appears that there is another (archive?) file included in some way which will have the Final_Answer.txt
Havent looked any closer, is this 1 file the only part of the challenge ?
lol, didnt fully read you post, just saw that you already mentioned the zip password... doh ..
DeleteTape!!
ReplyDeleteAwesome job with the articles. Just love 'em. Have been following your posts for quite a while now.
And finally after a long time,
IT'S GOOD TO HAVE YOU BACK!!!
yo tape fu..n nice poost , love the work you do man keep up THS member
ReplyDeleteExcellent post TAPE! Were you ever able to complete challenge 1 from the forums?
ReplyDeleteLove the blog,
~ЯΣDOX
Hey man ! Flad u liked the post, thanks :)
DeleteNever did get that damn lightbulb.png figured out no... after several anger management sessions, decided to just let it go :)
hey man - my internet is somewhat intermittent for the time being; would you mind if i used httrack to copy this page for personal reference? not to be reproduced on the web.
ReplyDeletera1 '-_-'
Dont see why not !
DeleteIf you re-use something from here, just be kind enough to mention where you got it is all ;)
Excellent post. Time for one on alpha channels! :-D
ReplyDeleteHey ! Pleased you dropped by and had a look :)
DeleteYour challenge site is fantastic and I got a few others on it as well who are doing waaaay better than I could ever hope to.
Me, I'm still struggling to get any further at the mo ;)
Will have to have a looksie at alpha channels..
*Beams at the praise*
ReplyDeleteI'll add more as time permits (My bosses have this thing about me actually WORKING... *Pouts*)
Good stuff on here dewd. :-)
Thanks man, this stuff is a loooong way away from what my dayjob entails, so am only learning bit by bit so to speak .. lol..
DeleteBut its all interesting ;)
Stuck on what to do after I get the exif data. This my first try at this and got the zip and the second and third photos. Now stuck
ReplyDeleteIf you look at the exif data of the individual images (carve them to have individual images for clarity's sake) something in one of them stands out like a sore thumb...
DeleteGot the last photo. Bit tricky on processing the data till i realized what it was. Last photo with the # I am clueless on. Not bad for never hearing of this before last night.
ReplyDeleteNot bad at all !! :)
Deletethe last one will require use of a specific tool which also described in the above post.
You're close ! nice work and hope you enjoying it ;)
Oh and also the one thing i am good at... That photo with the rar file you found. Its apart of this. http://www.lbpcentral.com/forums/showthread.php?32119-Something-BIG-is-coming-Kindred
ReplyDeleteWhich seems to be a puzzle for the forum users about a psp game that was coming out. I found other clues the users of the place never found. And they never noticed the info in the picture either. No clue or care if the game came out, it was fun following the_hoader's trail over the web to get the password to only realize the game was over 2 years ago
Can I get a research hint on the last one? I have learned a ton that i can mix with everything else and also. I used a different method to get the image for the last photo, I made it an html file by adding img src="data:image/jpg;base64, and the proper < and > to it. Was that the right way to get the image data? using the stuff on base64 here didn't work out as well for me here.
ReplyDeleteHiya,
DeleteSurprised you couldn't get the info with the standard base64 commands, following bits and bobs used in the above post you should have been able to with standard 'base64 -d filein > fileout' should work fine.
(based on using BackTrack)
As for research hints.. well, Steganography ;)
using ubuntu with extra's installed might be an issue with the base64, can you email the file that you got so i can compare them? And see if that is the issue? If so I will troubleshoot the base64 install till i get a know data match
ReplyDeleteFrom your mention of '#' I am pretty sure you have what you need..
DeleteWhen you say you have extras installed, does that mean that all the tools mentioned in the above post are installed ?
If you dont have steghide.. you are not going to get far ;)
Of course it will come down to getting the right password...
I have had issues with stegbreak, but have tested a script I found on pastebin which works nicely but not too fast.. ;
http://pastebin.com/nLSbbF17
I am giving you far too many hints on all this now, but as you are the only one who has taken the time to respond on your trials, hell, why not :)
Thanks for the interest in the blog !
No after I stopped being stupid I realize what I was doing wrong. but I can now say I learned a ton and got it! Thanks Tape for the hints the last was almost needed till I realized it was right in front of my face. I couldn't see the forest due to the trees in the way.
DeleteHehe :)
DeleteWell glad you enjoyed it all man, its fun stuff right ?!
It is, working on Challenge one from the THS, found the 390 bytes of hidden data in the first file already. plugging at the second one. Can't wait to see what you do next. And I did like that little trip you caused on the photo with the rar. I spent half the day tracking them down and solving the riddle, too bad I was 2 years+ late
DeleteHang on, you got the THS Image Challenge 1 ?
DeleteNow it is I that asks for research hints as I remember getting stuck on both files I am ashamed to say..
If you enjoy this kind of thing you really should look at the challenge site wixxerd.com
It is great fun and soooo frustrating ;)
Tape, sorry i was away for a bit, open them both in gimp. Maximum RGB filter. Will try to get more if i get time later.
Deletehi tape..i think you should make a post on METASPLOIT and how to succesfully bypass it from a powerful antivirus as most of antivirus detect, i tried to crypt the file and it works...please think on it..your greaaat fan..
ReplyDeleteThis is cool!
ReplyDelete