(! with the release of Backtrack 4 Final, mdk3 is back with mdk3v6! Found in /pentest/wireless/mdk3/)
The below installation guide only applicable to Backtrack 4 Pre Final.
To get it installed, Virchanza wrote up a means to do so here;
http://forums.remote-exploit.org/backtrack-4-package-feature-requests/23803-mdk3.html
The contents of interest being ;
wget http://virjacode.com/projects/beefup/dloads/mdk3.tar.bz2 tar xjf mdk3.tar.bz2 cd mdk3-v5 sed -i 's|-Wall|-w|g' ./Makefile sed -i 's|-Wextra||g' ./Makefile sed -i 's|-Wall||g' ./osdep/common.mak sed -i 's|-Wextra||g' ./osdep/common.mak sed -i 's|-Werror|-w|g' ./osdep/common.mak sed -i 's|-W||g' ./osdep/common.mak make make install cd .. rm mdk3.tar.bz2 rm -r mdk3-v5
The reason I used it was to decloak hidden SSIDs by means of either a brute force or a dictionary attack, but there are many other interesting options with mdk3 !
In this test setup, I have an AP setup as follows ;
BSSID 00:13:D4:09:32:60 on Channel 3 Hidden SSID of 3 characters only.
So checking the test setup in airodump shows ;
In order to try to crack the hidden SSID, we can try a bruteforce attack, however it is always best to first try a dictionary to see if it isnt a standard essid name.
To get a decent dictionary list, you can get the one which the Church of WiFi used for their tables.
http://www.renderlab.net/projects/WPA-tables/
And of course you can drive around a bit and collect a few more to add.
The general usage in this case for using mdk3 with wordlist is ;
mdk3 [iface] p -c [channel] -t [bssid] -f [path to wordlist] -s [packets/sec]
So in my case;
mdk3 mon0 p -c 3 -t 00:13:D4:09:32:60 -f /wordlists/ssid.txt -s 50
(can do more packets per sec. but just for example's sake)So when successful in finding the SSID and airodump is left running, the found SSID will pop up in airodump;
If the SSID cannot be found in the wordlist, then bruteforce approach can be tried, but only for short SSIDs.
It took my setup around 30min to crunch through all printable characters for the 3 character SSID..
The general usage of the bruteforce attack is as follows ;
mdk3 [iface] p -c [channel] -t [bssid] -b [character set] -s [packets/sec]
The brute force character set is as follows;- a all printable
- l lower case
- u upper case
- n numbers
- c lower and upper case
- m lower and upper case plus numbers
It failed to correctly identify the essid on my test network when no limit was set (then it does max 300pps), however it did work succesfully when limiting to 150 pps.
Mind you it is being tested on a pretty old ASUS WL-530g router.. so not surprising really..
What works for other routers is probably simply a matter of trial and error.
Also, airodump seemed to conk out after about a minute of running possible ssids to the router with the message;
"Caught signal 14 (SIGALRM). Please contact the author!"
Anyway..
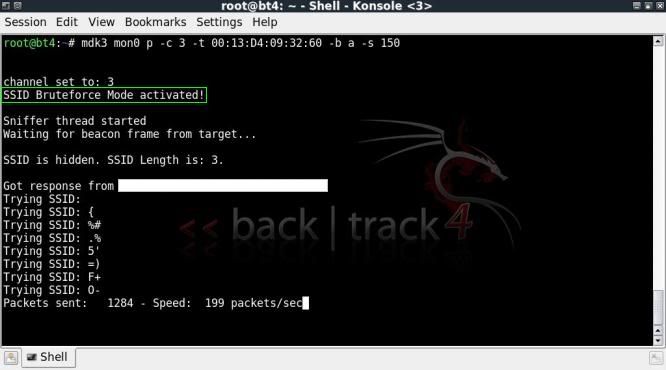
Starting up the attack using brute force;
mdk3 mon0 p -c 3 -t 00:13:D4:09:32:60 -b a -s 150
Again the results may vary using different packets/sec.
The screen will also show SSIDs of other networks which are picked up during the attack, but will then happily continue until either the full scope of the attack is finished, or the SSID is found.
MDK3 also has, among others, the interesting capability to effectively render communicating with a wireless network impossible, however to keep the posts semi short and sweet will come back to that another day..
MDK3 homepage - http://homepages.tu-darmstadt.de
A video showing the above ;
http://blip.tv/file/2681248
or
http://www.youtube.com/watch?v=52d1FsfJ2Ek






thnx for the info
ReplyDeletedani@dani-laptop:~/mdk3-v5$ make install
ReplyDeletecc -g -O3 -w -lpthread mdk3.c osdep/libosdep.a -o mdk3 -Losdep -losdep
mdk3.c:69: error: conflicting types for ‘getline’
/usr/include/stdio.h:651: note: previous declaration of ‘getline’ was here
make: *** [mdk3] Error 1
In the new update of BackTrack, namely back|track 4 final, MDK3 v6 is included.
ReplyDeleteI suggest you try that instead.
thanks, I'll try and I'll answer
ReplyDeleteSometimes I have seen <length: 0> in airodump. What does it mean and what do you do in this case?
ReplyDeleteTo be honest I have never tried mdk3 on an essid showing length 0.
ReplyDeleteWhat it means is that the AP is not revealing how many characters the essid has.
Could be 5 could be 3..
http://tinyurl.com/3ybqv4k
Monitoring long enough with airodump / kismet will usually de-cloak it (when a client connects etc).
Patience is a virtue.. as is only testing mdk3 on networks you are authorized to..
hi im mark, i have aircrack4 FINAL, i have already crack the wep key but my problem is the ssid is hidden .. i tried your tutorial but when i type ""airodump-ng mon0 -c (the channel is 11) -t opn"" it shows me nothing..
ReplyDeleteand when i tried to type the command ""mdk3 mon0 p -b"" it says the mdk3 is unknown...
i dont know how to install mdk3 but i read in other furom they say that mdk3 is already installed in backtrack4 Final..
im sorry for my english, hope you understand me and respons:) thanks..
mdk3 is installed with backtrack4, but to use it you have to navigate to the correct directory;
ReplyDeletecd /pentest/wireless/mdk3/
then when in that directory;
./mdk3 mon0 etc etc
hi Tape im mark again, in new in using backtrack4. can you make me instruction on how do i navigate the MDK3? and is it possible to crack hidden ssid?
ReplyDelete? Seriously ?
ReplyDeleteThe reply to your first comment shows how to navigate to the mdk3 directory..
This whole post is about cracking hidden SSIDs...
Test only on your own network.
This comment has been removed by a blog administrator.
ReplyDeleteYou really shouldnt be posting your email for the interwebz to see.. not smart.
ReplyDeleteAlso I really dont understand what you want to even do :/
in realty you have a very good information.
ReplyDeletei like it and keep it up.
Glad you like the posts, thanks :)
ReplyDeleteHi Tape!
ReplyDeleteDo you know the reason why it "skips" the right pw while brute forcing the hidden ssid?
I have the same problem (i'm writing my dissertation about wifi). It doesn't find the correct ssid always but bf should always work:S
Hey there anonymous ;)
ReplyDeleteAs mentioned, what I found is that if the speed was set to a too high a level that it sometimes missed it.
Try to reduce the speed (-s switch) to a much lower level such as -s 50 or such.
Alternatively, you could make sure that you have a dictionary list in which the SSID is included and run the dictionary attack instead.
I did have consistently good results when using a lower speed.
Let me know what your results are !
Hi! Sorry i forgot to introduce myself:D i'm dkaro!:D
ReplyDeleteI think i have bigger problem than a wrong command.:S
When i try to bf with a dictionary it always fails. I have a dictionary with 10 words (i tried bigger ones also) and i set the packet/s to 1 and it skip the pw.
I read a lot about mdk and watch a lot of tutorials and in every video it writes the tested key for example:
"next try testing xyz"
but in my case it always says last try was NULL.
with normal bf it works but with dictionary it doesnt. and i'd like find it out why.
any idea?
thanks for the help!
dkaro
Hey again dkaro :)
ReplyDeleteI havent played with mdk3 for a while, so I did a few tests again for sake of good order and all worked for me.
You advise that the BruteForce attacks work OK, but that the dictionary attacks fail, correct ?
So I am wondering with what OS you make the dictionary file..
Is it possible that you have made a wordlist in windows, or downloaded one which may possibly have the carriage returns included ?
If that is the case, try making a small dictionary list with for instance crunch in backtrack and add your SSID in that list and run it with mdk3.
I have also seen the 'last try was NULL' sentence, but only after it found my correct SSID !
It has also come up when I was too far away from my AP.
Make sure you are close enough.
I only test on my own equipment so it is never further away than a few metres.
Hi!
ReplyDeleteThe router is next to me so the distance can't be the problem.
I tried my own dictionary and i tried a downloaded one both of them failed.
Whats separator in the wordlist? I wrote every word in a new line (its worked with wpa bf).
Could be the character encoding the problem? i made my list on BT4 with Kate what should the encoding be?
Thanks again and sorry for my english im not too good at it:D
Sounds like you are creating the list OK, when I say carriage return, I mean that some wordlists made in Windows will have a carriage return[enter] at the end of each line (invisible) but which a linux system can read as a character.
ReplyDeleteIf you make the wordlist in Kate in BT4, then should be OK.
Not sure what to say, when I tested it yesterday it all worked for me as long as I didnt try to do it too fast and not too far away.
Can only suggest you double check your syntax (code you are using) and possibly change your router SSID to something easy to find like SMC and try with that.
Ok! I'll post the commands, the outputs and the wordlist when i get home.
ReplyDeleteAnd the SSID was sFg or something like that so not a long one.
thanks
Well, looks like the problem solved but don't ask how. I did a new wordlist with Kate it failed. It contained 10 word included the right SSID wich was "ca". Then i made a same one with nano and it worked. After that retried with Kate and it workd too. So i give up if anyone knows how could it be tell me. btw now its working so i can move on with my dissertation.
ReplyDeleteAnd very good blog, i'll read the other posts after i finish this.:)
thanks for the help.
Glad you finally got it working !
ReplyDeleteThanks for the nice comment :)
hi tape again!
ReplyDeletei'm stuck with mdk3 again but now its mac brute force.
do you have any experience about it?
I've tried 3 different router and non off theme worked. its trying the same mac againg and again.
i read that the routers may not deny the authentication correctly so that could cause the problem.
do you know any other mac bruteforce tool?
dkaro
Well I tried a while ago as well and did not have any success.
ReplyDeleteSee my post I made on the backtrack forums a while ago;
http://www.backtrack-linux.org/forums/beginners-forum/483-mdk3-bruteforce-mac-filters.html
I have no other ideas on bruteforcing MAC addresses, but
the best thing to do is to run a scanning tool and wait till
a client connects, so you can spoof that mac address and gain access that way.
haha i didn't realized that you posted that comment on bt forum:) ofcourse i read all topics on the forum and googled a lot thats why i'm here:)
ReplyDeletewell looks like there is no way to bypass the macfiltering on a "passive" network.
thanx again for your answer!
:)
ReplyDeleteThe only thing you could look for is whether the router
in question is vulnerable to any other type of attack
allowing access.
But in reality, your best bet is to wait for a client to connect and spoof that mac address.
yup this is the best way but i wanted to write about this way too.:)
ReplyDeletethe routers are vulnerable to the attack i tried lot of them. just this one won't work
oops i mixed my nicknames:D that was me dkaro:D
ReplyDeleteI test the following on an hidden ESSID with knwon lenght and mdk starts with 2 characters ?
ReplyDeleteWhy?
mdk3 mon0 p -b a -c $CHANNEL -t $BSSID -s 150
Its probably not.. how many single characters were you expecting to see if
Deleteyou whacking out 150/sec... ?!
More likely is that already all single characters quickly checked and then running into 2 characters.
Hello all,
ReplyDeleteSo I am using mdk3 on my router with a hidden essid and for some reason mdk3 only sends approx 1 - 4 packets. It then says....
Got response from 00:11:22:33:44:55, SSID: ""
The SSID always shows "". Why is this? Also obviously the mac address is not 001122.... im just writing that as an example. Here is the command i write.
mdk3 mon0 p -c 6 -t 00:11:22:33:44:55 -b l -s 150